
Automating Third-Party Patching – Product Review
Automating Third-Party Patching
As a CISO, speaker, author, or security advisor I keep getting the same question again and again. What products do I use or recommend for Third-Party Patching. I deceided to review a few products and share my views as is. In this blog post I will quickly explain what Third Party pathing is and then review a product;
What is Third-Party Patching?
Third-party patching or third-party patch management is the process of deploying patch updates to third-party applications that have been installed on one or more of your endpoints (e.g., servers, desktops, or laptops). Third-party patching addresses bugs or vulnerabilities in the software that either affect its function or security. Patching software vulnerabilities is a critical part of your overall IT security process that helps prevent exploitation by hackers.
Endpoint management tools also perform patch management for operating systems including Windows, Windows Server and macOS to keep them up to date and protected against cyberattacks.
What are Third-Party Applications?
A third-party application is software created by a company other than the original manufacturer of the device on which the application is running or the operating system (OS) that supports it.
For example, Adobe Acrobat Reader is a third-party app that is available for both Microsoft Windows and macOS. (Source: Kaseya )
Now, let’s start with a product review Easy2Patch :
What is 3rd Party Product?
3rd Party products are software developed by software companies / teams other than the operating system manufacturer. Google Chrome, Mozilla Firefox, Oracle Java, 7-zip, WinRAR etc. applications can be given as 3rd Party software examples. These 3rd party applications should be updated on time from the right file, and from the right source to prevent cyber-attacks that can occur.
What does Easy2Patch do?
Easy2Patch eliminates the need to manually update 3rd party software installed on your entire team’s computers, helping you save labor and increase your organization’s information security.
Why Use Easy2Patch?
As everybody knows that, in today’s world cybercrimes are increasing day by day. Attackers infiltrate organizations using known vulnerabilities of applications. For this reason, institutional authorities require and supervise the use of current versions of applications in sector-based regulations.
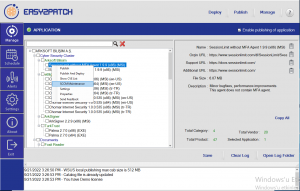
How does Easy2Patch work?
Easy2Patch is an important cyber security product that integrates with SCCM/WSUS and provides automatic and unattended updates to the software in its catalog. The products in the catalog are constantly monitored almost every day by automatic and manual methods. Published CVEs for updates are tracked and added to the Easy2Patch CVE database. Cybersecurity administrators can use this information to see a list of possible malicious vulnerabilities in their structures. With the rules on the SCCM/WSUS side, they can ensure that the distributions are sent sequentially in test and production environments.
It works integrated with Microsoft Endpoint Configuration Manager (SCCM), which is one of the most used software as Endpoint Manager in IT structures, and Windows Server Update Service (WSUS), which is the update system. Detection, automatic distribution, unattended update of outdated software can be performed without the need for an additional agent structure. Easy2Patch allows the system administrator to perform an end-to-end automatic update after making basic settings.
Who needs to use Easy2Patch?
All the organizations give importance to information security.
How do you provide your organization’s information security via Easy2Patch?
As everybody knows that, in today’s world cybercrimes are increasing day by day. Attackers infiltrate organizations using known vulnerabilities of applications. Especially, security vulnerabilities called Zero-Day should be closed very quickly and security should be ensured as quickly as possible. When the importance of security is so prominent these days, updating the operating systems alone is not enough. It is obvious that updating all kinds of software is very important in terms of ensuring security.
Easy2Patch catalog has 200+ 3rd party products. It works integrated with Microsoft Endpoint Configuration Manager (SCCM), which is one of the most used software as Endpoint Manager in IT structures, and Windows Server Update Service (WSUS), which is the update system. Detection, automatic distribution, unattended update of outdated software can be performed without the need for an additional agent structure.
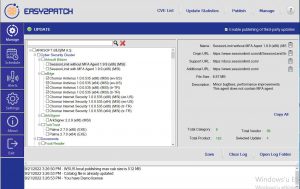
Easy2Patch allows the system administrator to perform an end-to-end automatic update after making basic settings.
Which organizations should use Easy2Patch?
Easy2Patch could be used by all the organizations that give importance to information security.
What does Easy2Patch bring to you when you use it in your organization? What are the advantages?
Easy2Patch provides central (automatic) update/upgrade of software that we define as 3rd party product on computers. It enables software to update from the right source with the right methods through this way, this upgraded/updated structure protects organizations from possible attacks. Let’s have a quick look at the advantages of using Easy2Patch:
- Saving time and labor,
- Finding suitable updates without manual tracking by matching vulnerabilities with the CVE database.
- Updating and creating application or applications without agent,
- Increasing your organization’s security by responding quickly to Zero-Day vulnerabilities.
- Patching potential security vulnerabilities faster with current updates.
- The costs that occur due to cyber-attacks is reduced.
Easy2Patch: Automate Your 3rd Party Patching Stay Update to Date!
Why is it Important to Update Third Party Software?
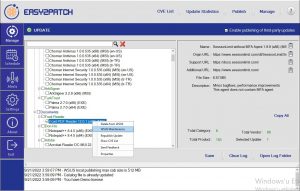
From their web site:
To see my other Reviews click here





