
Cybersecurity Frameworks – 2023 : Great Starting Guide
Cybersecurity Frameworks
A cyber security framework provides national and industry security leaders a common language and a set of standards that can help them evaluate, improve, and monitor their security posture. Using a framework makes it easier to define the processes and steps organizations should take to assess, monitor, and mitigate cyber security risks. It can also help organizations evaluate the security posture of their vendors or partners, and coordinate security with third parties.
Generally speaking, cyber security frameworks are voluntary, but they can be extremely important for organizations that need to comply with regulations and industry standards that include cyber security requirements. These frameworks are an essential stepping stone on the way to achieving compliance.
Source: Tutorial Spot,
Nowadays, safeguarding precious data from cybercriminals has never been so essential in this modern world. An organization has vast data, and it is challenging to manage all that without a structured plan. Any organization’s IT professionals cannot do it on their own. Hence, they rely on something called Cyber Security Framework. We will discuss many of these Cyber Security Frameworks here, and you’ll walk away knowing all the core concepts of these frameworks.
What is a Cyber Security Framework?
These documents describe guidelines, standards, and best practices for cyber security risk management. These frameworks reduce an organization’s exposure to weaknesses and vulnerabilities that cybercriminals can exploit. The word ‘Framework’ may seem like it is referred to some hardware, but it is not. It is, as mentioned before, a document. This document gives us information that deals with the infrastructure of servers, data storage, etc.
It is more like a structure, whereas we see the building standing tall in real life. It’s all due to a solid system. But, when it comes to cyber security, the Cyber Security Framework is there to provide the foundation strength the servers need to be protected from cyberattacks.
Types of Security Frameworks
There are mainly three types of frameworks. Each of the types has its different functions. Those three types are −
- Control Frameworks − This framework is known to develop an essential strategy for the cyber security department of an organization. Along with this, it provides an array of security controls, understands the present state of the technology being used, and ensures that these security controls are implemented second to none.
- Program Frameworks − This framework analyses the state of the organization’s security program. This also helps develop a customized cybersecurity program, measures the program’s security, and goes through competitive analysis. Along with this, it also simplifies the communication between the cyber security team and the managers.
- Risk Frameworks − These frameworks suggest essential risk assessment and management processes. It helps in structuring a security program, identifying and measuring an organization’s security risks, and prioritizing security measures and activities.
What is the best Cyber Security Framework out there?
When we must pick one framework for the organization, it can be very tough. There are many frameworks out there, and it’s a tough job to test each one out and figure out the best one. So, we have put together the names of some of the best frameworks. The choice also depends a lot on the needs of the organization. So, there are some frameworks −
- The NIST Cyber Security Framework: The NIST is a set of security standards that many private companies and organizations can use to identify and respond to cyberattacks. This framework has guidelines to help organizations prevent and recover from such cyberattacks. NIST has five functions: Identity, Protect, Detect, Respond and Recover.
- The International Standards Framework (ISO): This is also known as the ISO 270K framework. It is considered the cyber security validation standard for both internal situations and across third parties. ISO 270K assumes that the organization has an Information Security management system. ISO/IEC 27001 requires management to exhaustively manage all the information security risks and to stay alert to threats and vulnerabilities. This can be inferred that the ISO framework is very demanding and requires a lot of hard work to maintain everything perfectly. This framework recommends about 114 different controls broken into 14 categories. If the ISO framework is implemented in an organization, then it will be a selling point for new customers. It is worth it!
- The Health Insurance Portability and Accountability Act: HIPAA provides a framework to manage confidential patient and consumer data, mainly privacy issues. This framework offers electronic healthcare information and is a must for healthcare providers, insurers, and clearinghouses.
- The Centre for Internet Security Critical Security Controls: Better known as CIS, this framework is ideal for start-ups that generally start slow and work their way to the top. Developed this framework back in October 2000. It was made to protect companies from various cyberattacks. It consists of only 20 controls regularly being updated by security professionals from academia, government, and industry. This framework starts from the basics, moves to some critical basic foundations, and finishes with some organization. This framework uses benchmarks based on common standards such as HIPAA or NIST that map security standards and offer different configurations for organizations to improve cyber security.
Why do we need Cyber Security Frameworks?
Cyber Security networks are needed in every organization because setting up one secures many data from cyberattacks. It also removes some guesswork when it comes to securing assets. Frameworks provide a plan to the cyber security managers and give them a systematic plan for acting in different scenarios. Along with the plans, frameworks guide IT and security leaders to manage their organization’s risks more intelligently.
Companies can adjust the existing framework to meet their needs and requirements or even create their custom framework. Custom frameworks can be challenging as some businesses must adopt security frameworks that comply with commercial or government regulations. Custom-made frameworks may be insufficient to meet the standards to secure a network against dangerous cyber threats.
All in all, Cyber Security frameworks are needed by all companies and organizations, no matter if the company is big or small. In the future, there will be even more advanced frameworks.
Cybersecurity Frameworks
1. NIST Cyber Security Framework
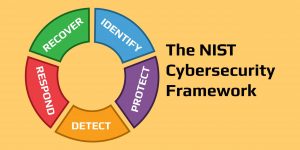
The National Institute of Standards and Technology (NIST) is a non-regulatory US government agency dedicated to promoting American industrial competitiveness and innovation. NIST provides various resources and standards, including a framework for “Improving Critical Infrastructure cyber security,” also known as the NIST cyber security framework.
The NIST cybersecurity framework was designed to help protect critical infrastructure, such as dams and power plants, against cyber attacks, but you can apply these principles to any organization. It offers an organized mechanism to help you identify risks and locate the assets that require protection. It also defines methods that can help protect these assets.
The framework is highly extensive. Its most basic document consists of 41 pages. Implementing the framework may require thousands of work hours and hundreds of procedures, controls, and documentation pages. However, the core principles are easy to understand. The framework offers a basic pattern for cyber defense, including:
- Identification
- Protection
- Detection
- Response
- Recovery
2. ISO/IEC 27001 and 27002

The International Standards Organization (ISO) 27001/27002 framework (also known as ISO 27K) is an internationally recognized standard for cyber security. This framework requires organizations adopting the ISO 27001 standard to adopt the following practices:
- Use an information security management system (ISMS).
- Assign management roles to systematically manage the organization’s security risks while accounting for cyber threats and vulnerabilities.
- Design and implement coherent and comprehensive information security controls to mitigate identified risks.
- Adopt an ongoing risk management process.
3. Center for Internet Security (CIS)
The Center for Internet Security (CIS) is a nonprofit organization created by Eastern Europe and Asia countries. It focuses on improving cyber security readiness and response across the public and private sectors. The CIS includes the following four program divisions:
- The Integrated Intelligence Center—facilitates relationships between private-sector and government entities to help create comprehensive coordinated security intelligence.
- The Multi-State Information Sharing and Analysis Center—aims to improve overall cyber security for local, territorial, tribal, and state governments. It achieves this objective by promoting collaboration and information sharing between members, the United States Department of Homeland Security, and private-sector partners.
- The Security Benchmarks—creates and promotes consensus-based standards to improve the security and privacy of Internet-connected systems and ensure the integrity of private and public Internet-based transactions and functions.
- The Trusted Purchasing Alliance—helps private and public sectors procure cyber security policies and tools cost-effectively.
The CIS provides its members with various resources, including emails detailing cyber safety tips, online papers and guides, instructional videos, and informative podcasts. Additionally, the CIS offers cyber security policy development advice at all levels, including national and international parties.
4. SOC2 Framework
The Service Organization Control (SOC) Type 2 was developed by the American Institute of Certified Public Accountants (AICPA) to provide a trust-based cyber security framework and auditing standard. It helps verify that partners and vendors manage client data securely.
The SOC2 framework defines over 60 compliance requirements and extensive auditing processes for third-party controls and systems. A SOC2 audit may take a year to complete, and at the end of the process, auditors issue a report that attests to the vendors’ cyber security posture.
Since SOC2 is highly comprehensive, it is also one of the most difficult frameworks to implement. Organizations in the banking or finance sector may especially struggle to implement SOC2 because they are required to meet a higher standard for compliance. Still, this framework is highly important and should serve as a central tool in third-party risk management programs.
5. NERC-CIP
The North American Electric Reliability Corporation—Critical Infrastructure Protection (NERC CIP) provides a set of cyber security standards for the utility and power sectors. NERC CIP was created in response to the rise in attacks on critical US infrastructure and increasing third-party risks. It aims to help reduce cyber risk and maintain the reliability of bulk electric systems.
The NERC CIP framework requires organizations to identify and mitigate risks in their supply chain. It specifies various controls to help identify and mitigate supply chain risks, including:
- Categorize systems and critical assets
- Train personnel
- Create and plan incident response programs
- Design effective recovery plans for critical cyber assets
- Perform ongoing vulnerability assessments
6. Cloud Security Alliance (CSA)
The Cloud Security Alliance (CSA) is a nonprofit organization that promotes research into security best practices for cloud computing and using cloud technologies to secure other forms of computing. CSA offers membership to any interested parties with the relevant expertise to contribute to cloud computing security.
CSA employs the expertise of its global members, which include industry practitioners, governments, associations, and corporations, to provide cloud security resources, such as research, certification, education, products, and events.
The organization facilitates activities and knowledge to benefit the entire cloud community. For example, it provides a forum that enables various parties to collaboratively create and maintain a trusted cloud ecosystem.
7. Cybersecurity and Infrastructure Security Agency (CISA)
The Cyber Security and Infrastructure Security Agency (CISA) is a division of the Department of Homeland Security (DHS) responsible for defending the Internet’s infrastructure and improving its security and resilience. It helps protect against infrastructure threats originating from natural disasters, terrorist attacks, cyberwarfare, etc.
CISA constantly identifies and assesses threats to Internet infrastructure, consulting with the government as well as the private sector. It provides many resources, including threat analysis, cyber security tools, and incident response across .gov websites. CISA delivers tools for technical coordination country-wide to facilitate emergency communications between partners.
Some honorable mentions −
- SOC2(Service Organization Control)
- GDPR (General Data Protection Regulation)
- FISMA (Federal Information Systems Management Act)
- NERC-CIP (North American Electric Reliability Corporation Critical Infrastructure Protection
- PCI-DSS (Payment Card Industry Data Security Standards)
- COBIT (Control Objectives for Information and Related Technologies)
- COSO (Committee of Sponsoring Organizations)
cybersecurity frameworks – top cybersecurity frameworks – common cybersecurity frameworks – cybersecurity frameworks list – list of cybersecurity frameworks – nist cybersecurity framework -What is the best framework for cyber security?
https://www.nist.gov/cyberframework
https://www.iso.org/isoiec-27001-information-security.html
https://www.hhs.gov/hipaa/index.htm
https://www.isaca.org/resources/cobit
https://www.cisa.gov/federal-information-security-modernization-act





