CISO Vision for 2024 Navigating the Cybersecurity Landscape As we move further into the digital age, the role of the Chief Information Security Officer (CISO) has become increasingly complex and pivotal to the success of any organization. The year 2024 presents new challenges and opportunities for CISOs to protect their organizations from emerging threats while […]
Thrilled to announce I’ll be delivering the keynote address at ITCN, Pakistan’s biggest IT conference!
Unlock Your Cybersecurity Leadership Potential
I’m excited to announce that my article on cyber transparency, published by Black Hat, is now live on their website!
Artificial Intelligence and its impact on Cybersecurity. We’ll uncover AI’s potential to both revolutionize our cybersecurity defenses but also the associated risks it introduces. By the end, you’ll have a clearer grasp of how to harness AI’s power while mitigating its dangers.
AI is a broad field that covers a range of technologies, from machine learning to natural language processing. AI systems can analyze large amounts of data and make decisions based on that data. They can also learn from their mistakes and improve over time.
The U.S. Securities and Exchange Commission (SEC) has recently adopted new rules to enhance the cybersecurity posture of public companies.
and here is what you need to know :
cybersecurity transparency is about being open and honest about cybersecurity risks, incidents, and the measures an organization takes to protect itself. This includes:
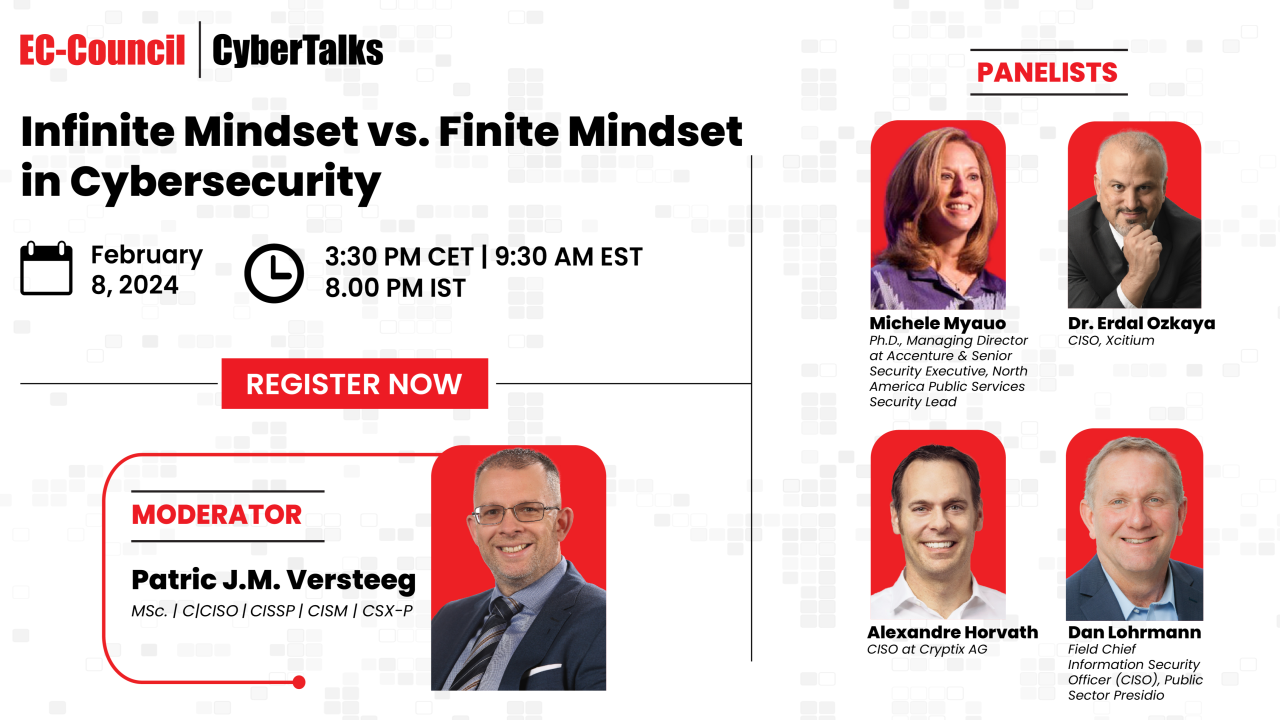
Cybersecurity isn’t just about technology – it’s fundamentally a battle of mindsets. The way we approach challenges shapes our strategies and determines our chances of success in this constantly shifting landscape. Two distinct mindsets dominate: the finite mindset and the infinite mindset.
A thought-provoking panel discussion is scheduled for February 8. It will be moderated by Patric J.M. Versteeg, MSc. and feature Alexandre Horvath, Dr. Erdal Ozkaya, Dan Lohrmann, and Michele Myauo, Ph.D as panelists. Register today to gain expert insights into the finite and infinite business mindset in cybersecurity and the role of an infinite mindset toward building a holistic security approach. Save your spot: https://bit.ly/3vuy0x5
7. Siber Güvenlik Ekosisteminin Geliştirilmesi Zirvesi Türkiye Bilişim Derneği tarafından bu yıl 5 Mart 2024 tarihinde Bilgi Teknolojileri ve İletişim Kurumu (BTK) Ana Konferans Salonunda gerçekleştirilecek olan, “7. Siber Güvenlik Ekosisteminin Geliştirilmesi Zirvesi”’nde Siber Güvenlik Stratejisti ve TBD ABD Temsilcisi, Sn. Dr. Erdal ÖZKAYA “2024’te Bizi Bekleyen Siber Tehditler” üzerine Davetli Konuşmasını gerçekleştirecektir. Siz değerli […]