
Is your DNS server safe or compromised – Check 4 Free
Is your DNS server safe or compromised ?
If you are not aware of what DNS Exchanger is please check my previous post, below
http://www.erdalozkaya.com/post/2012/02/14/DNSChanger-Malware.aspx
There is now a Australian Government web site which will check your DNS server and will let you know if you are safe or not. Just click in the URL and let’s see how safe your DNS setting is ? (or click here)
Read about the malware at FBI web site
What is it?
The DNSChanger Trojan Horse, also known as OSX.RSPlug.A and OSX/Puper, and OSX/Jahlav-C, has been found on numerous pornographic websites disguising itself as a video codec. Once downloaded and installed, DNSChanger changes the DNS settings on the computer, redirecting websites entered by the user to malicious sites. If personal information is entered on these malicious websites, it can lead to identity theft.
Is DNSChanger spyware?
Yes, due to the nature of installation in tricking the user as well as changing the information requested with altered data DNSChanger Trojan Horse is considered a trojan horse as well as spyware.
Great Article by Topher Kessler
On July 9, the FBI will close down a network of DNS servers that many people have been depending on for proper Internet access. These servers were originally a part of a scam where a crime ring of Estonian nationals developed and distributed a malware package called DNSChanger, but which the FBI seized and converted to a legitimate DNS service.
This malware scam has been widespread enough that even third-party companies like Google and Facebook and a number of ISPs like Comcast, COX, Verizon, and AT&T have joined in the effort to help remove it by issuing automatic notifications to users that their systems are configured with the rogue DNS network.
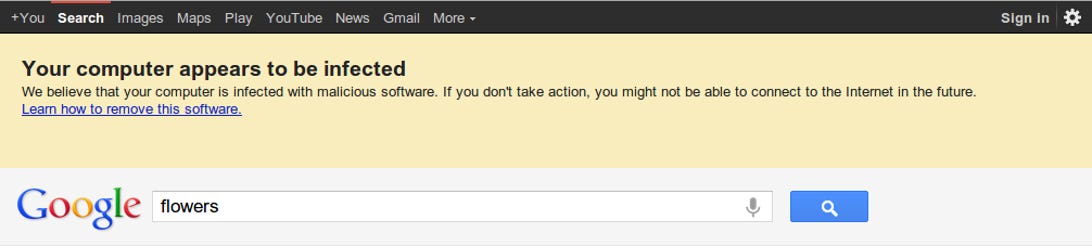
If you have recently received a warning when performing a Google search, browsing Facebook, or otherwise using the Web that claims your system may be compromised, then you might consider taking a few steps to check your system for the presence of the malware. This can be done in a couple of ways. First you can check the DNS settings in your system to see if the servers your computer is using are part of the rogue DNS network.
On Mac systems open the Network system preferences and for each network service (Wi-Fi, Ethernet, Bluetooth, etc.), select the service and then click the “Advanced” button. Follow this by selecting the “DNS” tab and making note of the DNS servers listed. You can also do this in the Terminal by first running the following command:
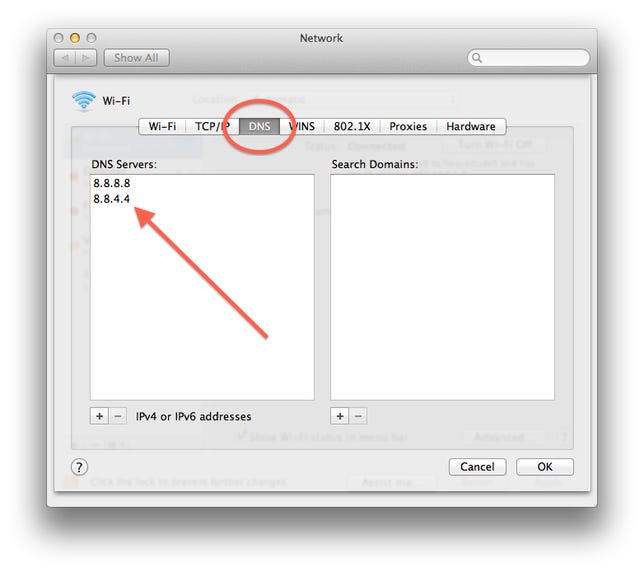
networksetup -listallnetworkservices
After this command is run, next run the following command on each of the listed names (be sure to remove any asterisks from in front of the names, and ensure the names are in quotes if there are any spaces in them):
networksetup -getdnsservers “SERVICE NAME”
Repeat this command for all listed services (Especially Ethernet and Wi-Fi connections) to list all configured DNS servers.
On a Windows machine (including any of those you may have installed in a virtual machine), you can open the command-line tool (select “Run” from the Start menu and enter “cmd,” or in Windows 7 select “All Programs” and then choose the command line from the Accessories folder). In the command line, run the following command to list all network interface information, including configured DNS server IP addresses:
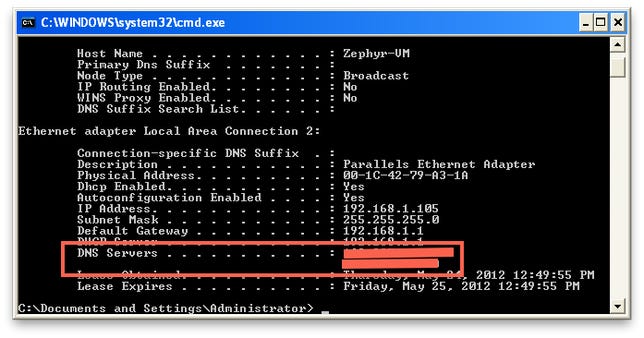
ipconfig /all
Once you have your system’s DNS servers listed, enter them into the FBI’s DNS checker Web page to see if they are identified as part of the rogue DNS network. In addition to manually looking up and checking your DNS settings, a number of Web services have popped up that will test your system for the DNSChanger malware. The DNSChanger Working Group has compiled a list of many of these services, which you can use to test your system (for those in the U.S., you can go to dns-ok.us to test your connection).
If these tests come up clean, then you have nothing to worry about; however, if they give you any warnings, then you can use an anti-malware scanner to check for and remove the DNSChanger malware. Given that the malware was abruptly halted in November 2011, there’s been ample time for security companies to update their anti-malware definitions to include all variants of DNSChanger.
If you have a malware scanner and have not used it recently, then be sure to launch and update it fully, followed by performing a full scan of your system. Do this for every PC and Mac on your network, and in addition be sure to check your router’s settings to see if the DNS settings there are proper ones from your ISP or are rogue DNS settings.
If your router or computer is not showing any valid DNS server addresses after you have removed the malware, and your system is unable to connect to Internet services, then you might try configuring your system to use a public DNS service, such as those from OpenDNS and Google, by entering the following IP addresses into your system’s network settings:
8.8.8.8
8.8.4.4
208.67.222.222
208.67.220.220
If after Monday you find you can no longer access the Internet, then it’s likely your system or network router is still configured with the rogue DNS servers and you will need to again attempt to detect and remove the malware from your systems. Luckily the malware is not viral in nature so it will not self-propagate and automatically re-infect systems. Therefore, once removed and once users have set up valid DNS servers on their systems, then the affected computers should have proper access to the Internet.
Background
DNS is the “Domain Name System,” which acts like the Internet’s phone book and translates human-friendly URLs such as “www.cnet.com” into their respective IP addresses that computers and routers use to establish connections. Since DNS is the interface between the typed URL and the targeted server, the crime ring created its own DNS network that would in large part work normally, but would also allow the ring to arbitrarily redirect the traffic for specific URLs to fake Web sites for the purposes of stealing personal information or getting people to click on ads.
Setting up the rogue DNS network itself isn’t enough, since this network needs to be specified in a computer’s settings in order to be used. To make this happen, the crime ring created the DNSChanger malware (also referred to as RSplug, Puper, and Jahlav), which was distributed as a trojan horse and successfully infected millions of PC systems worldwide. Once installed, this malware would continuously change the DNS settings for the affected computer and even for network routers, to point to the crime ring’s rogue DNS network. As a result, even if people manually changed their computers’ DNS settings, these changes would automatically be reverted by the malware on their systems.
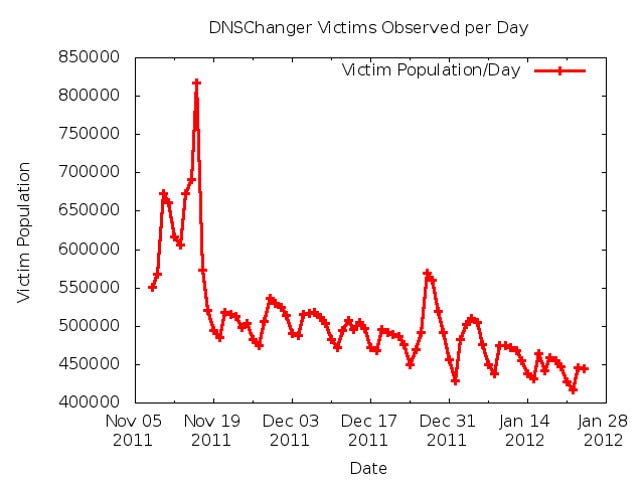
Since millions of PC users had been infected by this malware, once the crime ring was taken down in a November 2011 multilateral sting called Operation Ghost Click, the FBI and other government authorities decided against turning off the rogue DNS network as this would have instantly prevented the infected systems from resolving URLs, and thereby would have effectively shut down the Internet for them. Instead, the DNS network was kept active and converted to a legitimate service while efforts were put in place to notify users of the DNSChanger malware and wait for the number of worldwide infections to fall.
Initially the rogue DNS network was slated for closure in March of this year; however, while the rate of infections fell significantly once the crime ring was broken up, the number of infected computers has remained relatively high, so the FBI extended the deadline to July 9 (this upcoming Monday). Unfortunately, even as this deadline approaches, thousands of PC system worldwide are still infected with the DNSChanger malware, and when the servers are shut down these systems will no longer be able to resolve URLs to IP addresses.








