Comodo MITRE Kill Chain – Detailed 1nfo
Comodo MITRE Kill Chain
Cyber Intrusion Kill Chain aka Kill Chain, has been adapted from military concepts. Locked Martin’s engineers was the first to adapt it to cyber security area. The core of framework has been arisen from the structure of attack. It describes an end-to-end process , or the entire chain of events, that is required to perform a successful attack.
“First identify the target, find target location, monitor the target’s movement, asses the target and select appropriate weapon, engage with the target and evaluate the effects of the attack. “
The Kill Chain’s can both useable as conducting an attack or detecting, defensing an attack as well. When defense is in action, we are talking about breaking an opponent’s kill chain, making an attack unsuccessful. Lockheed Martin’s CKC model serves as first and the starting point to analyze APT and malware attacks. According to the Lockheed Martin researchers, full kill-chain can be defined as “aggressor must develop a payload to breach a trusted boundary, establish a presence inside a trusted environment, and from that presence, take actions towards their objectives”
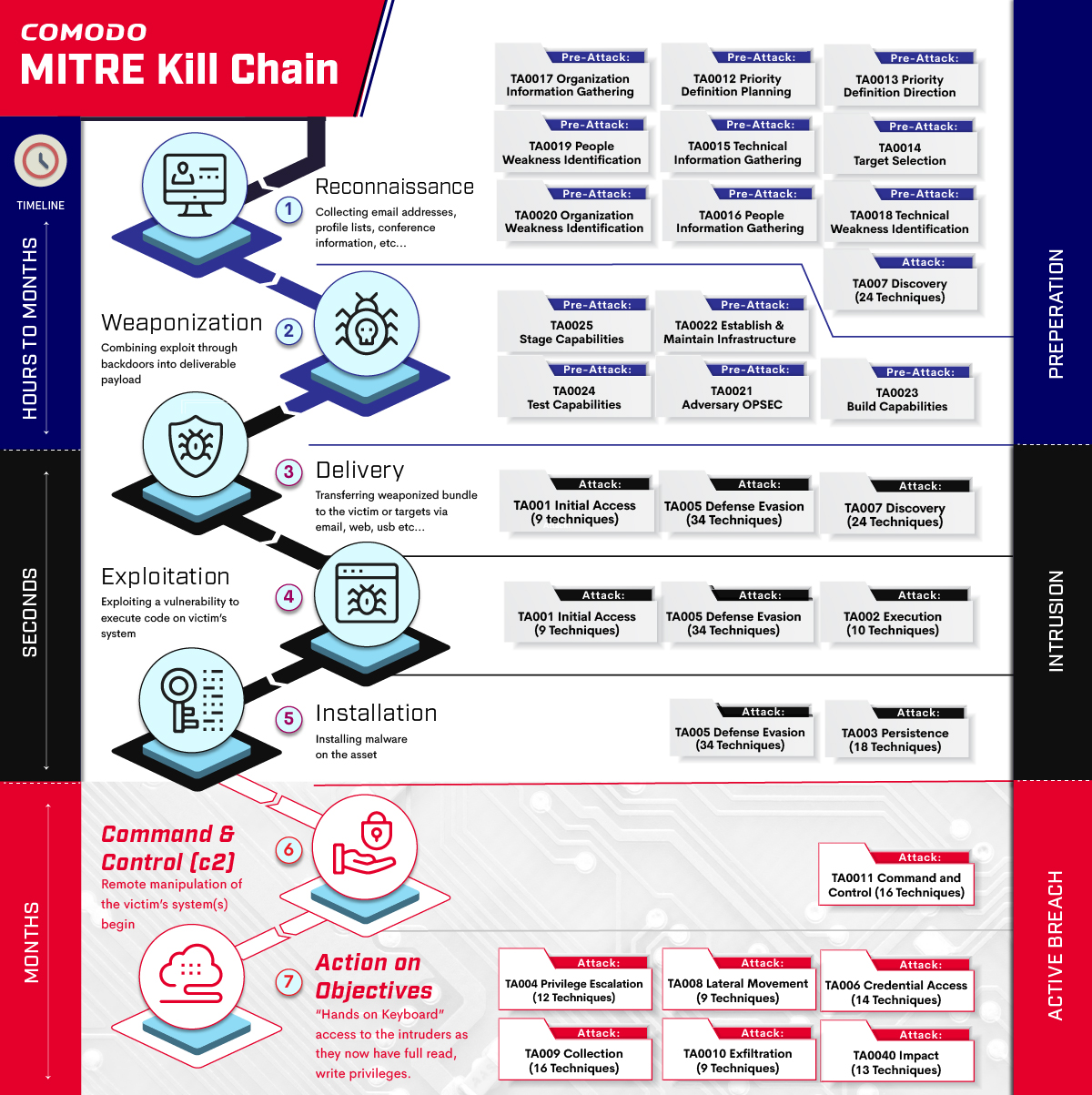
The chain of events, or kill chain, which an external attacker must go through is defined in the CKC on a tactical level as shown:
- Reconnaissance: Passive or Active reconnaissance activities to identify targets for potential weaknesses. Assessment of each possible intelligence against best course of action.
- Weaponization: Creating or finding remote access malware that is suitable to exploit potential weaknesses or vulnerabilities, coupling it into deliverable payloads (like mostly used file types)
- Delivery: Delivery the payload to the target environment. Mostly combined with any other weaknesses discovered reconnaissance phase. Here the attack vector can be including it in emails, using malicious or hacked websites or using USB’s etc.
- Exploitation: is triggering execution of the payload. It can be auto-triggered such as running download program or executing the files in USB or more advanced techniques like targeted attack using social engineering etc are possible.
- Installation: Installing payload to create consistent channel between victim and attacker. Mostly backdoor is deployed to maintain the presence at this point.
- Command & Control: Establishing a C&C channel. This allows attackers a pivotal point to direct and reach the objectives in the target environment.
- Action on Objectives: Final round to reach original objectives, the impact is maximum such as exfiltration of confidential data or compromising integrity or availability of the systems.
The Cyber Kill Chain is regarded as the standard model for defending against APTs. It targets to help detecting APTs during one the phases as well as can also be used to allocate preventive and defensive counter measures. APT was first used within the United States intelligence community to describe Asia-Pacific Threats (mainly from China). Since then, APT becomes Advanced Persistent Threat to describe advanced attackers who persistently use different attack techniques on victim’s systems to reach the final goal. NIST defines APT as:
- pursues its objectives repeatedly over an extended period of time;
- adapts to defenders’ efforts to resist it; and
- is determined to maintain the level of interaction needed to execute its objectives
MITRE started ATT&CK framework in 2013, as oppose to Cyber Kill Chains, they focus on adversary behaviors other than typical indicators such as domains, IP addresses, hashes etc. MITRE works on how adversaries interact with systems, their intention and behavior. To relate behaviors to defenses , MITRE ATT&CK framework breaks down tactics and techniques to low-level definitions. Tactics, techniques, and procedures (TTPs) are foundation store where it creates a common taxonomy , applicable to real environments, comparable and sharable among different platforms.
In MITRE ATT&CK, Tactics represent the “why” where Techniques represent the “how”. Tactics serve as useful contextual categories for individual techniques and cover standard, higher-level notations for things adversaries do during an operation, such as persist, discover information, move laterally, execute files, and exfiltrate data. Techniques show how it can be achievable such as “Exfiltration Over C2 Channel” stealing data by exfiltrating it over an existing command and control channel.
However Kill Chains also show course of action with stages of attacks. This is also very important information about detecting and finding active breach that is hidden behind the curtains. The attack techniques there such as C&C, Privilege Escalation or Lateral Movement is behind achieving final objective from attacker perspective. Here we have merged both taxonomy and map appropriate MITRE ATT&CK tactics and techniques. Continue reading Comodo MITRE Kill Chain – Detailed 1nfo