Best Cybersecurity Blogs – Top 100 –
Best Cybersecurity Blogs
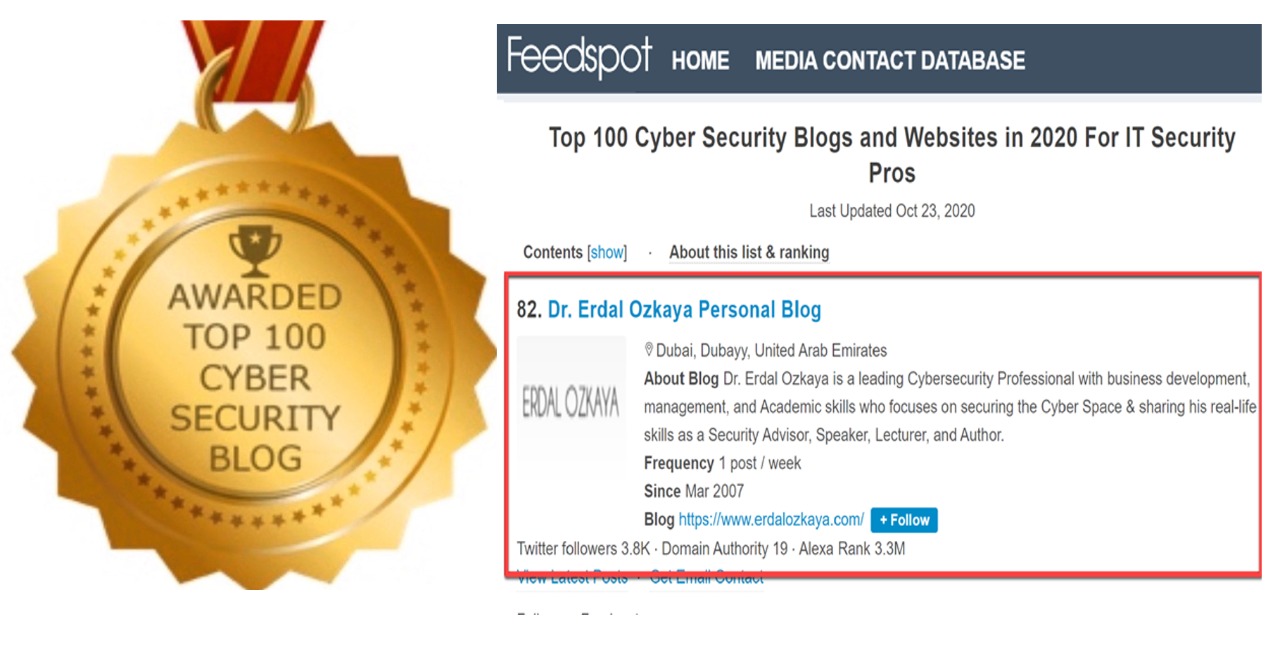
I am delighted to announce that my blog has been recognized in the Top 100 Cybersecurity blogs by Feedspot.com. This would not happen without your support. THANK YOU , for keep visiting my blog and supporting my blog. I promise that I will do my best to give you the best and FREE content as much as I find time in the feature as well.
And of course a very BIG Thank you for selecting my blog at the TOP 100 for feedspot.com .
Feedspot.com selects the best Cyber Security blogs from thousands of blogs on the web ranked by traffic, social media followers, domain authority & freshness.
And here is my last 3 years performance 🙂

2021 : Top 100 Blogs in Cybersecurity Number 87
2020 :Top 100 Blogs in Cybersecurity Number 82
2019 : Top 100 Blogs in Cybersecurity Number 84
You can visit the list from here : https://blog.feedspot.com/cyber_security_blogs/
More About the award
The blogs included in the list, which came from a pool of thousands of other infosec blogs, were ranked based on the following criteria:
- Google reputation and Google search ranking
- Influence and popularity on Facebook, Twitter and other social media sites
- Quality and consistency of posts
- Feedspot’s editorial team and expert review
About Feedspot.com
Feedspot is a Content Reader. It helps you keep up with multiple websites in one place so that you need not visit each website to see what’s new. “Feedspot makes keeping up with your favorite websites as easy as checking your email. ”
Following tools and features empower you to keep track of information that matters the most to you, helps you automate your workflow and make your life easier.
To see more my awards :
https://www.erdalozkaya.com/category/about-erdal-ozkaya/awards/