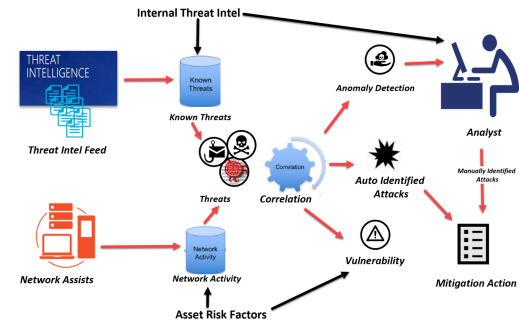
Building a Cyber Threat Intelligence Platform in 5 steps
• Mitigating risk: Adversaries are constantly discovering new ways to infiltrate organizations. Threat intelligence provides visibility into these existing and emerging security hazards, which will reduce the risk of data loss, prevent or minimize the disruption of business operations, and increase regulatory compliance.
You can learn more about Cybersecurity in my book “Cybersecurity : The Beginners Guide”
more info about my book : https://www.erdalozkaya.com/cybersecurity-the-beginners-guide-3
Amazon Australia : https://www.amazon.com.au/Cybersecurity-Beginners-Dr-Erdal-Ozkaya/dp/1789616190/
Case study – Panama Papers
In 2015, an offshore law firm called Mossack Fonseca had 11.5 million of their documents leaked. These documents contained confidential financial information for more than 214,488 offshore entities under what was later known as the Panama Papers. In the leaked documents, several national leaders, politicians, and industry leaders were identified, including a trail to Vladimir Putin. The following diagram shows how much was exposed as part of this attack:

While there is not much information available on how the cyber attack occurred, various security researchers have analyzed the operation.
According to the WikiLeaks post, which claims to show a client communication from Mossack Fonseca, they confirm that there was a breach of their“email server“. Considering the size of the data leak, it is believed that a direct attack occurred on the email servers.
Cyber terrorists
Extremist and terrorist organizations such as Al Qaeda and Islamic State of Iraq and Syria (ISIS) are using the internet to distribute their propaganda, recruiting new terrorists and communicating via this medium. An example of this is the 2008 attack in Mumbai, in which one of the gunmen confirmed that they used Google Earth to familiarize themselves with the locations of buildings. Cyber terrorism is an extension of traditional terrorism in cyber space.
Case study – Operation Ababil
In 2012, the Islamic group Izz ad-Din al-Qassam Cyber Fighters—which is a military wing of Hamas—attacked a series of American financial institutions. On September 18th 2012, this threat actor group confirmed that they were behind the cyber attack and justified it due to the relationship of the United States government with Israel. They also claimed that this was a response to the Innocence of Muslims video released by the American pastor Terry Jones. As part of a DDoS attack, they targeted the New York Stock Exchange as well as banks such as J.P. Morgan Chase.
Cyber criminals
Cyber criminals are either individuals or groups of hackers who use technology to commit crimes in the digital world. The primary driver of cyber criminals is financial gain and/or service disruption. Cyber criminals use computers in three broad ways:
- Select computers as their target: These criminals attack other people’s computers to perform malicious activities, such as spreading viruses, data theft, identity theft, and more.
- Use computers as their weapon: They use computers to carry out “conventional crime”, such as spam, fraud, illegal gambling, and more.
- Use computers as an accessory: They use computers to save stolen or illegal data.
The following provides the larger picture so we can understand how Cyber Criminals has penetrated into the finance sector and wreaked havoc:

Becky Pinkard, vice president of service delivery and intelligence at Digital Shadows Ltd, states that “Attackers can harm the bank by adding or subtracting a zero with every balance, or even by deleting entire accounts”.
Case study – FIN7
On August 1st 2018, the United States District Attorney’s Office for the Western District of Washington announced the arrest of several members of the cyber criminal organization FIN7, which had been tracked since 2015. To this date, security researchers believe that FIN7 is one of the largest threat actor groups in the financial services industry. Combi Security is a FIN7 shelf company.
The screenshot presented here shows a phishing email sent by FIN7 to victims claiming it was sent by the US Food and Drug Administration (FDA)
Case study – Carbanak APT Attack
Carbanak is an advanced persistent threat (APT) attack that is believed to have been executed by the threat actor group Cobalt Strike Group in 2014. In this operation, the threat actor group was able to generate a total financial loss for victims of more than 1 billion US dollars. The following depicts how the Carbanak cyber-gang stole $1bn by targeting a bank:

Case study – OurMine operation
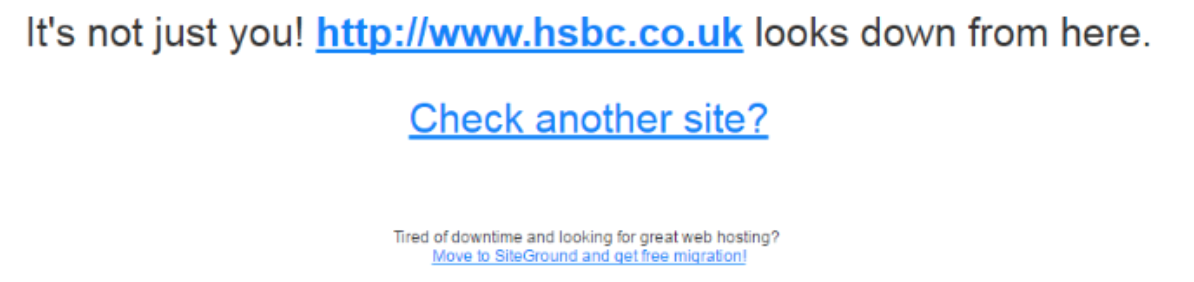
In 2016, the threat actor group OurMine, who are suspected to operate in Saudi Arabia, conducted a DDoS attack against HSBC’s websites, hosted in the USA and UK. The following screenshot shows the communication by the threat actor:

The result of the DDoS attack was that HSBC websites for the US and the UK were unavailable. The following screenshot shows the HSBC USA website after the DDoS attack:
With cybercrime on the rise, companies have started adopting the hard ways of preventing system breaches. Cybersecurity has become the need of the hour. This article will explore how cyberattacks bring companies down to their knees giving rise to cybersecurity. The article also looks at some of the cybersecurity strategies that an organization can adopt to safeguard itself from the prevalent attacks.
“For every lock, there is someone out there trying to pick it or break in.” – David Bernstein
Malware, Phishing, Ransomware, DDoS!
These terms have become widespread today due to the increasing number of cyberattacks. The cyber threats that organizations face have grown steadily during the last few years and can disrupt even the most resilient organizations.
3 cyber attacks that shook the digital world
2011: Sony
Who can forget the notorious Sony hack of April 2011? Sony’s PlayStation Network was hacked by a hacking group called “OurMine,” compromising the personal data of 77 million users. This cyberattack made Sony pay more than 15 million dollars in compensation to the people whose accounts were hacked. A hack made possible through a simple SQL inject could have been prevented using data encryption.
Not long after this hack, in 2014, Sony Pictures was attacked through a malware by a hacker group called “Guardians of Peace” stealing more than 100 terabytes of confidential data. Sony had once again not paid heed to its security audit, which showed flaws in the firewall and several routers and servers resulting in the failure of infrastructure management and a monetary loss of 8 million dollars in compensation.
2013: 3 billion Yahoo accounts hacked
Yahoo has been the target of the attackers thrice. During its takeover by Verizon, Yahoo disclosed that every one of Yahoo’s 3 billion accounts had been hacked in 2013. However, one of the worst things about this attack was that it was discovered only in 2016, a whopping two years after the breach.
2017: WannaCry
One of the most infamous ransomware of 2017, WannaCry spanned more than 150 countries targeting businesses running outdated Windows machines by leveraging some of the leaked NSA tools. The cyber attack that has been linked to North Korea hit thousands of targets, including public services and large corporations. The effects of WannaCry were so rampant that Microsoft, in an unusual move to curb the ransomware, released Windows patches for the systems it had stopped updating. On a somewhat unsurprising note, WannaCry owed its success to the use of outdated technologies (such as SMBv1) and improper maintaining their systems update for months, failing to protect themselves from the lurking attack.
How cyber attacks damage businesses
Cyberattacks are clearly bad for business. They lead to:
- Monetary loss
- Data loss
- Breach of confidential information
- Breach of trust
- Infrastructure damages
- Impending litigations and compensations
- Remediations
- Bad reputation
- Marketability
This is why cybersecurity is so important – investing in it is smart from a business perspective as it could save you a lot of money in the long run.
Emerging cybersecurity trends
Tech journalist and analyst Art Wittmann once said “the idea that security starts and ends with the purchase of a prepackaged firewall is simply misguided”. It’s a valuable thing to remember when thinking about cybersecurity today. It’s about more than just buying software; it’s also about infrastructure design, culture and organizational practices. Cybersecurity is really a range of techniques and strategies designed to tackle different threats from a variety of sources.
Gartner predicts that worldwide cybersecurity spending will climb to $96 billion in 2018. This rapid market growth is being driven by numerous emerging trends, including:
- Cloud computing
- Internet of things
- Machine learning
- Artificial Intelligence
- Biometrics and multi-factor authentication
- Remote access and BYOD–Bring your own device
Effective cybersecurity strategies
The most effective strategy to mitigate and minimize the effects of a cyberattack is to build a solid cybersecurity. Here are some of the ways in which an organization can strengthen their cybersecurity efforts:
- Understand the importance of security
In the cyberage, you have to take the role of security seriously. You need to protect the organization with the help of a security team. When building a security team, you should take into accountthe types of risks that could affect the organization, how these risks will impact the business, and remedial measures in case of a breach
- Top notch security systems
You cannot compromise on the quality of systems installed to secure your systems. Always remember what is at stake. Shoulda situation of attack arise, you need the best quality of security for your business.
- Implement a Red and Blue Team
The organization must use the Red Team and Blue Team tactics, where the Red Team tactics can be used in penetration for accessing sensitive data, and the Blue Team tactics will defend your system from complex attacks. This team can be appointed internally or this job could be outsourced to the experts.
- Security audits
Security audits are conducted with the aim of protect, detect, and respond. The security team must actively investigate their own security systems to make sure that everything is at par to defend against the lurking attack if it should occur. The security team must also be proactive with countermeasures to defend the organization walls against these malicious lurkers. Employees must also be properly educated to take proper precautions and act wisely in case of occurrence of a breach.
- Continuous monitoring
Securing your organization against cyberattacks is a continuous process. It is not a one-time-only activity. The security team must be appointed to do regular audits of the security systems of the organizations. There should be a systematic and regular process, penetration testing must be conducted at regular intervals. The results of these tests must be looked at seriously to take mitigation steps to correct any weak or problematic systems.
- Enhance your security posture
In an event of a breach, once the security team has confirmed the breach, they need to react quickly. However, don’t start investigating without a plan. The compromised device should be located, its behavior should be analyzed and remedial actions should be underway.
- Vigilance
In the words of the world’s most famous hacker, Kevin Mitnick, “Companies spend millions of dollars on firewalls, encryption,and secure access devices, and its money wasted; none of these measures address the weakest link in the security chain.”
It cannot be stressed enough how important it is to be ever vigilant. The security team must stay current with the latest threat intelligence and always be on the lookout for the latest malicious programs that disrupt the organizations.
- Think ahead
The question is never “if”, the real question is “when.” The attackers come sneaking when you are not looking. It is absolutely critical that organizations take a proactive stance to protect themselves by dropping the “if” attitude and adopting the “when” attitude.





