Free stuff from the net! Think twice ! Free Malware removal Guide 101
Free stuff from the net! Think twice !
A friend of mine called me during the night, asking for help.
He was downloading “free stuff” (magazine) from the net and enjoying the FREE reading, next day when he wanted to log in back to his PC , guess what happened , his FREE anti virus did not protect him from not getting infected.
After my investigations I found out that this ”free magazine” web site had everything in it, the blog them was exactly same as mine ![]() Anyway…
Anyway…
When I wanted to test the web site, i found the below activities :
First i typed the URL (don’t) , selected a category to download

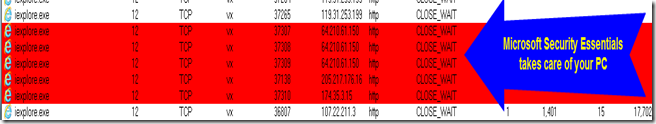
While I was browsing the list “ Microsoft Security Essentials” warned me!
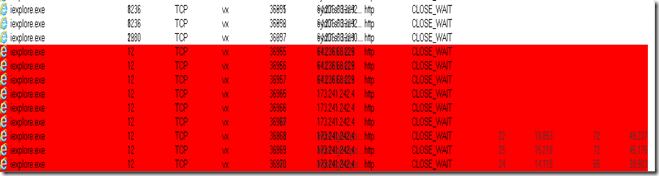
At the same time I did check my Sysinternal TCP view application, and yes the PC started to get many TCP connections in unusual ports
Many different IP addresses ,diverting the traffic from the “harmless (!)” magazine download web site to the TROJAN hosting web sites… Trojan Hosting ? What do I mean with that ? Of course , the redirection from the “Harmless (!) magazine download website to the “website which hosts the attack” , in this example , The magazine website redirects the browser to a malicious website that contains an instance of the “Blackhole” exploit kit. The “Backhole” exploit kit may exploit vulnerabilities in certain software that may be installed the computer. If exploitation is successful, it could lead to the download and execution of arbitrary files.
Below are few screenshots from TCP view, which proofs the diversion of the traffic,
So many connections where happening, I was not able quick enough to take screen shots![]()
What is this Trojan:JS/BlacoleRef.G ?
Trojan:JS/BlacoleRef.G is identified as dangerous Trojan infection. Trojan:JS/BlacoleRef.G makes use of computer vulnerability or network hole to get into the system. For example, it attaches to unknown email message and when you click on attachment, your computer gets infected. It exploits rootkit technique to shun security program. Once it gets executed, Trojan:JS/BlacoleRef.G will make the computer weaker for additional malware. It may drop rogue virus to your computer which is big threat to the system.
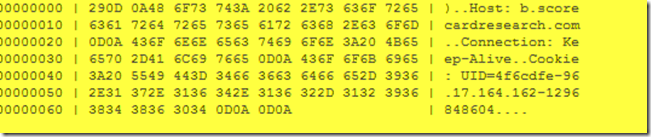
Let’s analyse the source of the traffic :
As you can see from the screenshots, the exploit will try to attack your computer from, unusual ports and weird web URL’s as above.
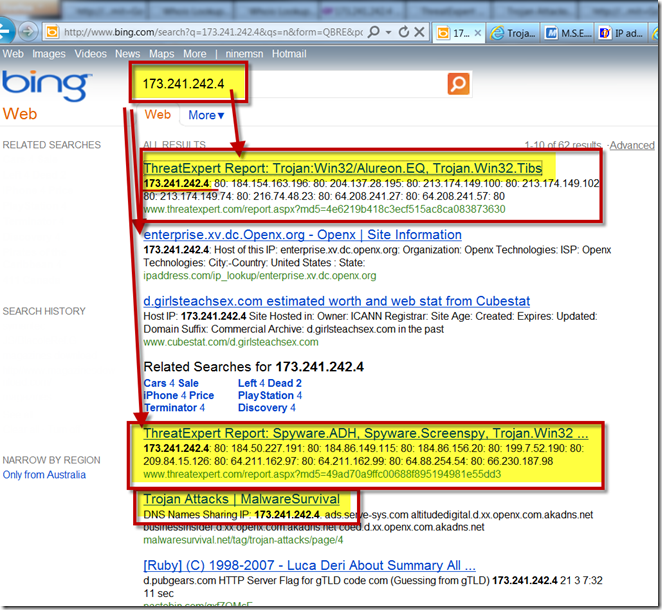
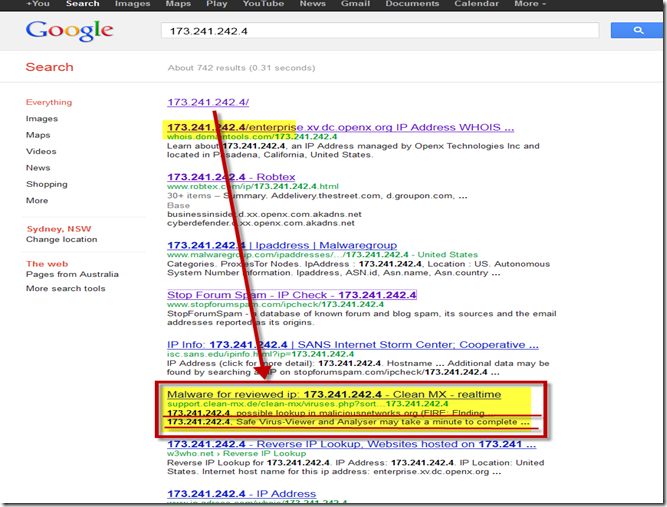
If you search the attacking IP address from your favorite Search Engine, you will also see most probably the IP is already known as BAD:
result from BING
result from GOOGLE
Free Malware removal guide
IP & URL analysis :
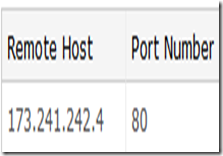
This screen shot indicates that there is an attack launched from IP 173.241.242.4 via HTTP protocol, and its randomly scanning my computer ports during the attack to sneak in to my PC…
While the attack happens, the Trojan is trying to modify the MEMORY via the IEXPLORER.EXE process name, to get some allocated space.
During the infection phase, the trojan is also creating some files in the system “
%AllUsersProfile%\~
%UserProfile%\Desktop\Trojan:JS/BlacoleRef.G.lnk
%UserProfile%\Start Menu\Programs\Trojan:JS/BlacoleRef.G\
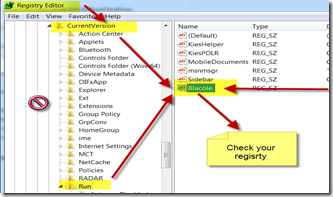
As many other Trojan’s, viruses it sits in the registry, too:
and it does create a OUTBOUND traffic…
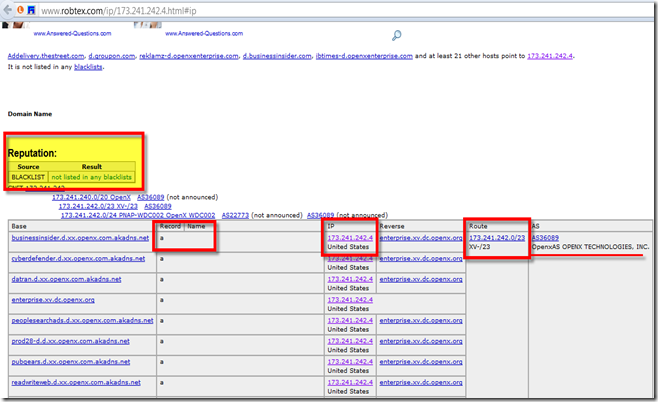
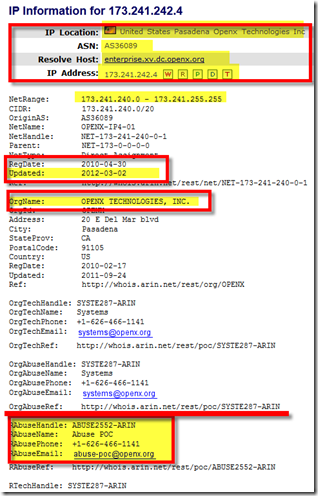
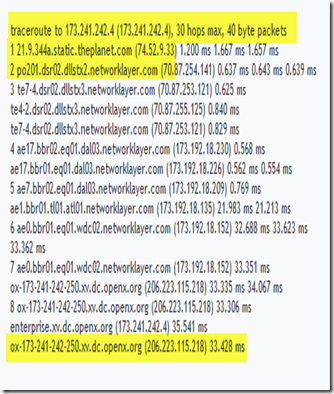
Please be aware that the Trojan is hosted in many different locations and even though its not a new Trojan, interestingly the Trojan hosting web sites are still not in a BLACK LIST. A ping, trace route , who is query is still responding as below:
and
How to remove the Trojan?
If you are using Up to Date Anti Virus & Windows , you should be fine, if not! Try one of the below steps and you should be fine:
To get an Enterprise ready Anti Virus and much more
After cleaning the Trojan from my friends PC, i did recommend him to subscribe to his favourite magazines, as there is really noting for FREE on the internet. Sooner or later you will need to pay to the FREE STUFF , either with a PC virus or Trojan which will steal your information from your PC or with loosing your valuables or dealing with a virus…
Next time think twice before you download.