
Don’t let Hackers steal your password 2
It’s not a secret anymore, Hackers know our passwords. 551,509,767 real-world passwords previously exposed in data breaches. Are you one of those victims? Has your email been compromised or found in a data breach so far? How do hackers get your passwords? In this article, I am going to write the common methods which hackers use to steal your passwords and then I will recommend you the industry best practices to keep you or at least your passwords safe ?
Mass Theft
This is the most convenient way for hackers, instead of hacking 10.000 people, they hack a vulnerable web site, which has all the information they need. Yes, I know this sounds hard but in reality, it’s not. Just recently (3 April 2019) more than 540 million records which included extensive details, including people’s comments, likes, names, and Facebook IDs were found in Amazon unprotected. (plain text) (You can Read here the details )
Hackers can also steal “hashes”, like in 2012, LinkedIn was saving their user database unsalted, which means “a random data was not used as an additional input to a one-way function that hashes data, a password or passphrase. Salting in cryptography is used to safeguard passwords; keeping it short they had no extra safeguard implemented to protect the passwords)
Brute Force
Hackers can use tools that can crack your password by simply entering different passwords over and over until it’s cracked (unless you have account lockout or MFA) ; Depending on the password complexity most passwords can be cracked very fast, as 123456 is still a very common password the time which is required to crack (0.02 seconds) this password is very very low compared P$45w@rd_?!.) £4<*aL^ (198 years depending on the resources available for the attack )
Phishing – Social Engineering
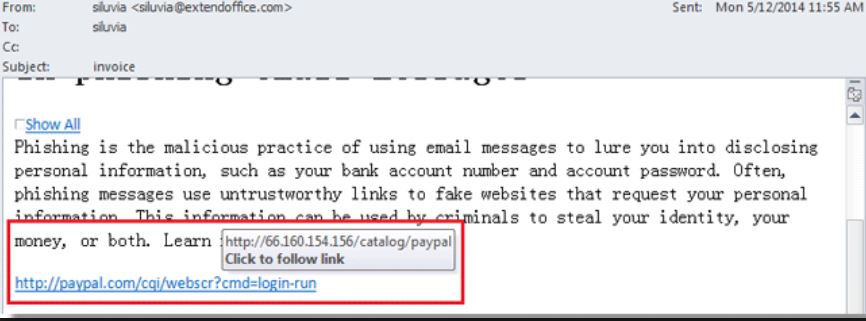
A hacker will send a login page for the account they aim to steal from you, which can be Facebook, Online Banking web site, Outlook, etc. They will try to make you believe that your account is under danger, to be safe click on the “provided” URL’s, which is fake of course, but the victim will not notice that and enter their details…
Malware Attacks
Below are some examples for Malware attacks, out of many different Malware attack types
Keylogger
A basic tool to get your passwords. Keylogger resides in your system memory and runs secretly in the background, it logs every keystroke from your computer, and then sends the information back to the hacker.
RAT
Remote Administration Tool , where a hacker can connect remotely to any PC without any permission ?
Trojan Horse
Malware which lands to your PC’s through “cracked software” through “warez” web site.
WI-FI Sniffers
Once a hacker breaks into a Wi-Fi network, unfortunately, it’s nearly impossible to detect a Wi-Fi sniffer attack, which means they will be intercepting all of the data you communicate.
Recommendations
- Where possible enable 2 Factor authentications
Google, Microsoft, Facebook, Twitter, and many other popular websites do provide this service. You can download an Authenticator app, which can be in an app in your phone, or you set up to receive SMS to the provided phone number or email to a preferred e-mail address.
Based on a current study done by New York University and Google, simply adding a recovery phone number to your Account can block up to 100% of automated bots, 99% of bulk phishing attacks, and 66% of targeted attacks.
If you’ve signed into your phone or set up a recovery phone number an SMS code sent to a recovery phone number helped block 100% of automated bots, 96% of bulk phishing attacks, and 76% of targeted. On-device prompts, a more secure replacement for SMS, helped prevent 100% of automated bots, 99% of bulk phishing attacks and 90% of targeted attacks.
- Make sure to have an up-to-date Anti-Virus
- Make sure to install a Firewall (or make sure your Windows Firewall is enabled)
- Never open suspicious attachments in emails even if they are from someone you know (they might be a Vitim)
- When you need to open a link in an email, compare on what you see in the URL and what actually the URL is (check the screenshot) or check that the web browser resolves the link properly. If, say, a “whatever.bank.com” link changes to “somethingelse.org,” exit the page immediately.
- If you receive a message saying it’s from a person you know and asks for critical data, call the person on the number stored in your contacts (instead of calling the SMS number) and verify that he/she has requested the data.
- Log off from the web sites once you are done using them. log back next time, can be a pain, but at least you’ll know that no one else can steal your token and log in without your permission
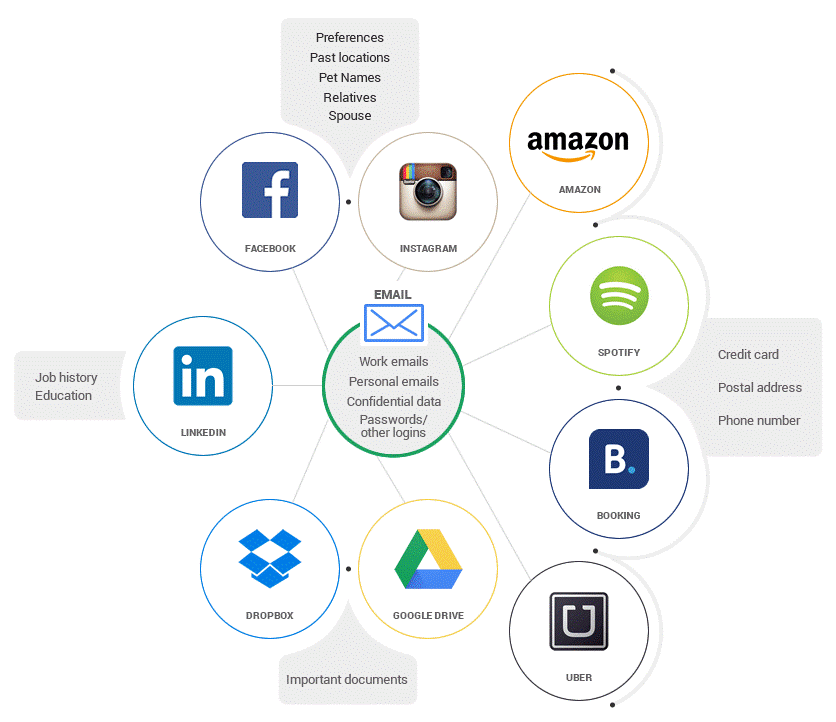
- Try not to reuse the same password, the below image illustrates how a leaked password which is used multiple times can affect you.
- Use biometrics like Windows Helo, Apple Face ID, Samsung fingerprint where possible
- Make sure you have a strong password
- Be aware of Social Engineering attacks.
Password Facts
- Many people are using the same password across multiple sites.
- Password theft is increasing every year
- “Save my password for future” use is still very commonly used
- Easy passwords are still very common
Did they steal your password?
If you are not sure if you are using a “well known or a commonly used ” password, or if you are not sure if your password which You use to connect to a web site/service has been hacked before you can check Have I been Pwned” web site.
I am sure by now you know the World known expert Troy Hunt, if not here is your opportunity to learn about his great, free and useful web site

10 core functions of a trusted operating system
https://www.erdalozkaya.com/core-functions-of-a-trusted-operating-system/
Cybersecurity : The Beginners Guide
Cybersecurity The Beginner’s Guide – Informative step by step Guide (19)





