Microsoft Intune in Real Life – Learn 4 Free
Microsoft Intune in Real Life
As you know I am on of the very few people who had access to the Beta program of Windows Intune ,and since Microsoft Management Summit in 2011 (Las Vegas) I am proudly presenting since then how Intune can help you
The session at TechEd took attention of the IT PRO’s and feedback was amazing, all given feedback regarding improvements will be passed to the product group, which will hopefully reflected in the upcoming versions ( Windows Intune 2.0)
Windows Intune, Microsoft’s Web-based PC management and security platform and Microsoft is betting big on Intune to be the cloud service that will facilitate IT’s evolving job of remotely managing
As we covered in the session Intune 2.0 will have those changes :
- IT admins can manage the deployment of Microsoft updates and service packs to all PCs,
- keep track of hardware and software inventory,
- fix PC issues remotely, manage protection from malware threats and set security policies.
- Windows Intune can be accessed from wherever there’s an Internet connection.
Windows Intune costs $11 per PC per month (Software Assurance customers will pay less than $11 -US Price, please verify the price for your country with your Microsoft Intune sellers.), and that price includes an integrated anti-malware product and Windows 7 Enterprise upgrade rights, which could be a real money-saver for smaller companies doing a Windows upgrade.
Microsoft is building parts of its high-end, on-premise enterprise products such as SCCM (System Center Configuration Manger), Forefront Endpoint Protection, and MDOP (Microsoft Desktop Optimization Pack) into Windows Intune. For an extra dollar per PC per month ($12), Windows Intune customers can access the MDOP suite of products, which include application and desktop virtualization tools.

Microsoft also plans to integrate Windows Intune with Office 365 so that IT pros can use Intune to deploy Office in the cloud. But right now, that integration is not in place for Windows Intune 2.0.
Windows Intune also does not support mobile devices like smartphones and tablets; it supports only Windows PCs. But Main says Microsoft plans to extend the support to mobile devices in future versions.
But Windows Intune 2.0 does offer a slew of new features. Here are four notable enhancements that may make Windows Intune a worthwhile service for IT managers.
Software Distribution
Windows Intune 2.0 simplifies the complex task of distributing both Microsoft and non-Microsoft software and updates to all PCs that are managed by Windows Intune.
An IT admin completes a simple wizard from the Windows Intune console to guide them through the process of publishing the software for distribution. These software or update packages can be .EXE, .MSI or .MSP files.
After the information has been entered, the wizard then encrypts, compresses and uploads the package to Windows Azure storage space until it’s ready for deployment. During a trial subscription, 2GB of free Windows Azure cloud storage are provided to store updates or apps until distribution. Paid subscriptions have a pre-determined amount of storage space (greater than 2GB). And customers have the option to purchase more space if needed.
When the software is living it appears in the Managed Software workspace. Administrators can then choose to deploy the software to select PCs. The next time these PCs are online, software installation will begin
Remote Tasks
The Remote Tasks feature gives IT admins more control over software updates and security scans on managed PCs.
When an IT admin right-clicks on a specific managed PC, a context menu appears with actions including Add to Group, Retire and Remote Tasks. When that admin selects “Remote Tasks” he can perform tasks on a Windows Intune managed PC, with options including:
- Run Full Malware Scan, which starts an immediate full scan of the client computer
- Run Quick Malware Scan, which starts a quick scan of the client computer, searching for select files and common file paths in just a few minutes
- Update Malware Definitions, which instructs the client software on the managed PC to check for the latest Windows Intune malware definitions
- Restart Computer, which forces a managed computer to reboot
License Management for Other Licenses
Windows Intune 2.0 extends software license management beyond just Microsoft enterprise software licenses to include Microsoft retail licenses, OEM licenses and other third-party licenses.
IT admins can use this feature to track purchased licenses against actual installations by entering details into the software catalog such as the publisher name, software title or number of licenses purchased. Software licenses can be tracked on the Add Agreements page under Licenses.
Read-Only Access
When adding administrators to a Windows Intune account, admins can select whether or not to grant full administrator rights or read-only access to information.
Someone with read-only rights can view all the information in the Windows Intune Administration Console, but cannot take any action such as approving an update or running a scan.
The read-only admin role can be useful when training new employees. These new employees can get familiar with the console without actually performing an action. Once they are comfortable, a full-access administrator can switch the new employee’s access from “read-only” to “full access” if desired.
For more information on how to subscribe to Windows Intune, click here.
Microsoft Intune Today :
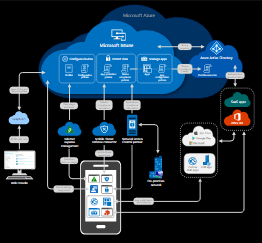
Microsoft Intune is a cloud-based service that focuses on mobile device management (MDM) and mobile application management (MAM). You control how your organization’s devices are used, including mobile phones, tablets, and laptops. You can also configure specific policies to control applications. For example, you can prevent emails from being sent to people outside your organization. Intune also allows people in your organization to use their personal devices for school or work. On personal devices, Intune helps make sure your organization’s data stays protected and can isolate organization data from personal data.
Intune is part of Microsoft’s Enterprise Mobility + Security (EMS) suite. Intune integrates with Azure Active Directory (Azure AD) to control who has access and what they can access. It also integrates with Azure Information Protection for data protection. It can be used with the Microsoft 365 suite of products. For example, you can deploy Microsoft Teams, OneNote, and other Microsoft 365 apps to devices. This feature enables people in your organization to be productive on all of their devices while keeping your organization’s information protected with the policies you create.
With Intune, you can:
- Choose to be 100% cloud with Intune, or be co-managed with Configuration Manager and Intune.
- Set rules and configure settings on personal and organization-owned devices to access data and networks.
- Deploy and authenticate apps on devices — on-premises and mobile.
- Protect your company information by controlling the way users access and share information.
- Be sure devices and apps are compliant with your security requirements.
Manage devices
In Intune, you manage devices using an approach that’s right for you. For organization-owned devices, you may want full control over the devices, including settings, features, and security. In this approach, devices and users of these devices “enroll” in Intune. Once enrolled, they receive your rules and settings through policies configured in Intune. For example, you can set password and PIN requirements, create a VPN connection, set up threat protection, and more.
For personal devices, or bring-your-own devices (BYOD), users may not want their organization administrators to have full control. In this approach, give users options. For example, users enroll their devices if they want full access to your organization’s resources. Or, if these users only want access to email or Microsoft Teams, then use app protection policies that require multi-factor authentication (MFA) to use these apps.
When devices are enrolled and managed in Intune, administrators can:
- See the devices enrolled and get an inventory of devices accessing organization resources.
- Configure devices, so they meet your security and health standards. For example, you probably want to block jailbroken devices.
- Push certificates to devices so users can easily access your Wi-Fi network or use a VPN to connect to your network.
- See reports on users and devices compliance.
- Remove organization data if a device is lost, stolen, or not used anymore.
Online resources:
Try the interactive guide
The Manage devices with Microsoft Endpoint Manager interactive guide steps you through the Microsoft Endpoint Manager admin center to show you how to manage and protect mobile and desktop applications.
Manage apps
Mobile application management (MAM) in Intune is designed to protect organization data at the application level, including custom apps and store apps. App management can be used on organization-owned devices and personal devices.
When apps are managed in Intune, administrators can:
- Add and assign mobile apps to user groups and devices, including users in specific groups, devices in specific groups, and more.
- Configure apps to start or run with specific settings enabled and update existing apps already on the device.
- See reports on which apps are used and track their usage.
- Do a selective wipe by removing only organization data from apps.
One way that Intune provides mobile app security is through app protection policies. App protection policies:
- Use Azure AD identity to isolate organization data from personal data. So personal information is isolated from organizational IT awareness. Data accessed using organization credentials are given additional security protection.
- Help secure access on personal devices by restricting actions users can take, such as copy-and-paste, save, and view.
- Can be created and deployed on devices that are enrolled in Intune, enrolled in another MDM service, or not enrolled in any MDM service. On enrolled devices, app protection policies can add an extra layer of protection.
For example, a user signs in to a device with their organization credentials. Their organization identity allows access to data that’s denied to their personal identity. As that organization data is used, app protection policies control how the data is saved and shared. When users sign in with their personal identity, those same protections aren’t applied. In this way, IT has control of organization data, while end users maintain control and privacy over their personal data.
You can also use Intune with the other services in EMS. This feature provides your organization’s mobile app security beyond what’s included with the operating system and any apps. Apps managed with EMS have access to a broader set of mobile app and data protection features.

Compliance and conditional access
Intune integrates with Azure AD to enable a broad set of access control scenarios. For example, require mobile devices be compliant with organization standards defined in Intune before accessing network resources, such as email or SharePoint. Likewise, you can lock down services, so they’re only available to a specific set of mobile apps. For example, you can lock down Exchange Online, so it’s only accessed by Outlook or Outlook Mobile.
Online resources:
-
Set rules on devices to allow access to your organization resources
-
Common ways to use Conditional Access with Intune
How to get Intune
Intune is available:
- As a stand-alone Azure service
- Included with Microsoft 365 and Microsoft 365 government
- As Mobile Device Management in Microsoft 365, which consists of some limited Intune features
Intune is used in many sectors, including government, education, kiosk or dedicated device for manufacturing and retail, and more.
Next steps
- Read some of the common business problems that Intune helps solve.
- Start with a 30-day trial of Intune.
- Plan your migration to Intune.
- Using your free trial or subscription, step through the Quickstart: Create an email device profile for iOS.