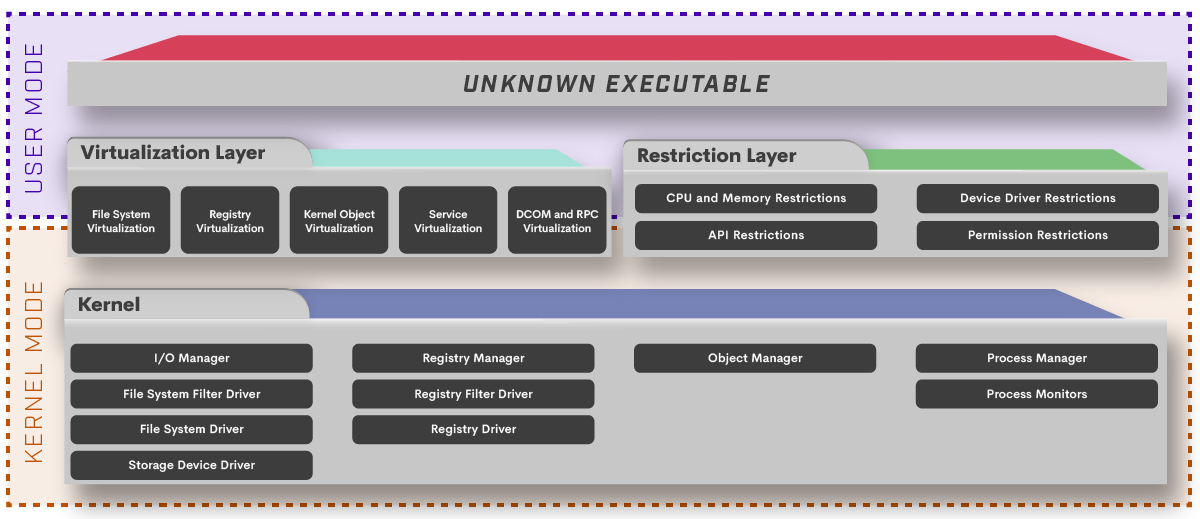
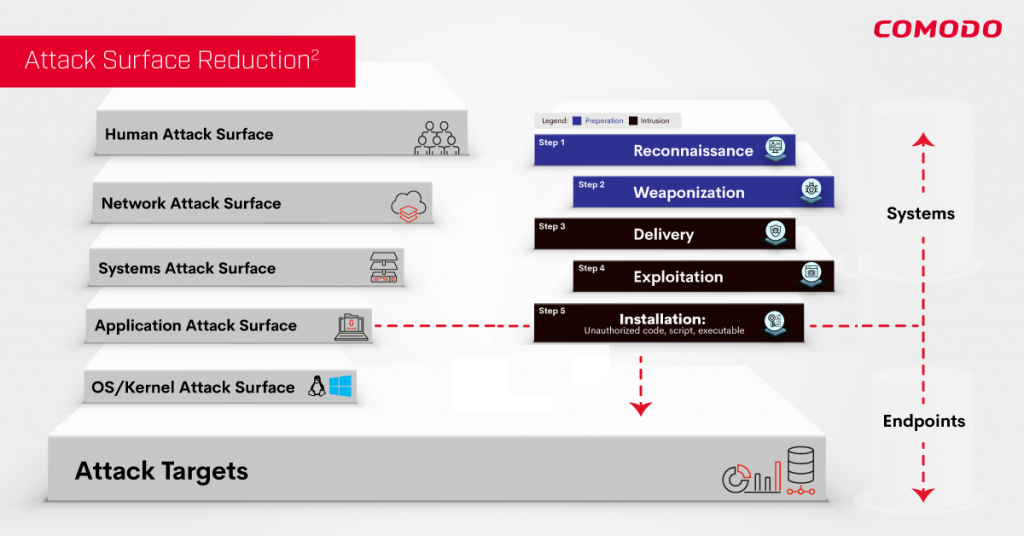
Comodo Security Solutions Rebrands to Xcitium – August 2022
Comodo Security Solutions Rebrands to Xcitium Launches Patented Zero Threat Endpoint Protection to Eliminate Growing Threats Comodo Security Solutions today announced a rebranding to Xcitium, as the company launches its patented zero threat endpoint technology to combat an increase in ransomware and other malware across all industries. Xcitium Zero Threat is the only solution on the […]