
The Malware Plague – Part 1
The Malware Plague
Malicious software—commonly referred to as malware—is used by threat actors to perform malicious activities on a host system. These malicious activities include compromising the corporate network, identity theft, and data exfiltration. The evolution of connected devices and the fact that it has become practically impossible to run an enterprise without a computer has increased the volume of threat actors leveraging malware as part of a cyber attack.

Malware can come in the form of scripts or executable code. There are many different classes of malware, but the most well known is by far computer viruses and computer Trojans. Threat actors no longer need to find their own vulnerabilities or build their own malware. Instead, they can procure them through the dark web. There has been an increased demand for sophisticated malware that is used by state-sponsored threat actors and organized crime syndicates:
With advancements in malware development, a new risk has arisen in the form polymorphic malware. Polymorphic malware is malware that runs once and never runs
again, making it extremely difficult for antivirus providers to prevent malicious activities.
Early on, threat actors discovered the benefit of leveraging malware during cyber attacks against institutes in the financial services industry. Once malware had reached the target endpoint, threat actors were able to illegally transfer funds from their target to accounts controlled by the threat actor. In addition to this, because ATMs are connected to the corporate network, threat actors focused on leveraging malware to attack ATMs.
Throughout this article, you will learn about malware classes and get an insight into some of the most commonly used malware families utilized as part of cyber attacks within the financial services industry.
Malware categories
It is important to understand the different malware categories that are leveraged by threat actors during cyber attacks. Only by understanding the differences between a computer virus and a computer Trojan, for example, will you be able to build prevention capabilities.
While end users often assume that malware is only applicable to computers, it is important to understand that malware can also affect any connected device, including smartphones and industry appliances
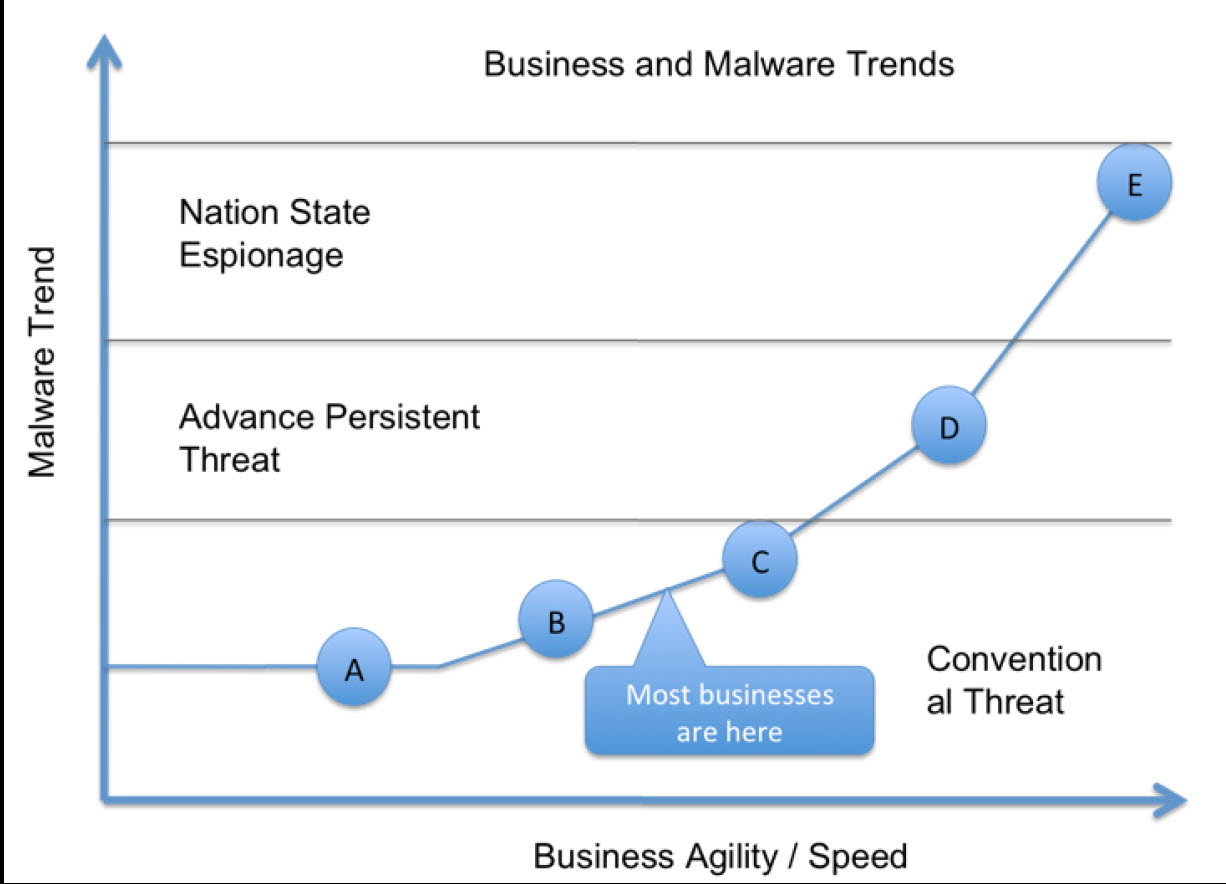
Depending on the objective of the threat actor, the group might use a specific malware family or a combination of malware. It is recommended that security teams build their Indicators of Compromise (IOC) aligned to the cyber attack kill chain.
The attack kill chain is a process that describes how threat actors perform a cyber attack with malware. The following diagram illustrates the attack kill chain:
Computer virus
At its core, a computer virus is very similar to a biological virus and is one of the most commonly used malware families:
Biological virus:
- Consists of DNA surrounded by a protein shell to bond to a host cell
- Replicates itself over the host’s metabolic machinery
- Copies infections to as many cells as possible
- The virus can’t live outside the host cell
The principle for all computer viruses is that they can insert themselves into files and processes on a computer in order to perform malicious actions. The are also able to replicate
themselves by modifying other computer programs:
Computer virus:
- Consists of a set of instructions stored in the operating system or application
- Replicates when the host program is executed
- Can only survive when the host program is executed
- Copies infections to other host programs
A computer virus can infect executables, scripts, documents, or even boot sectors. When a computer virus is able to infect a combination of targets, such as executables and documents, then these kinds of virus are commonly referred to as multipartite viruses.
Computer worm
A computer worm is a self-replicating payload that is able to spread rapidly in the network. While a computer worm and a computer virus are similar in their approach and reach, the big difference is that a computer worm does not require human interaction in order to spread in the network. It is possible for threat actors to combine the characteristics of a computer worm with a computer virus.
The most prominent example of this was in 1999 with the Melissa love letter. The Melissa love letter was an email that was sent to targets, containing a Word document with a virus hidden as a macro. When the end user enabled the macro, a virus would be injected through the document file and, at the same time, a worm would be executed. This would then spread across the network:
SQL Slammer worm
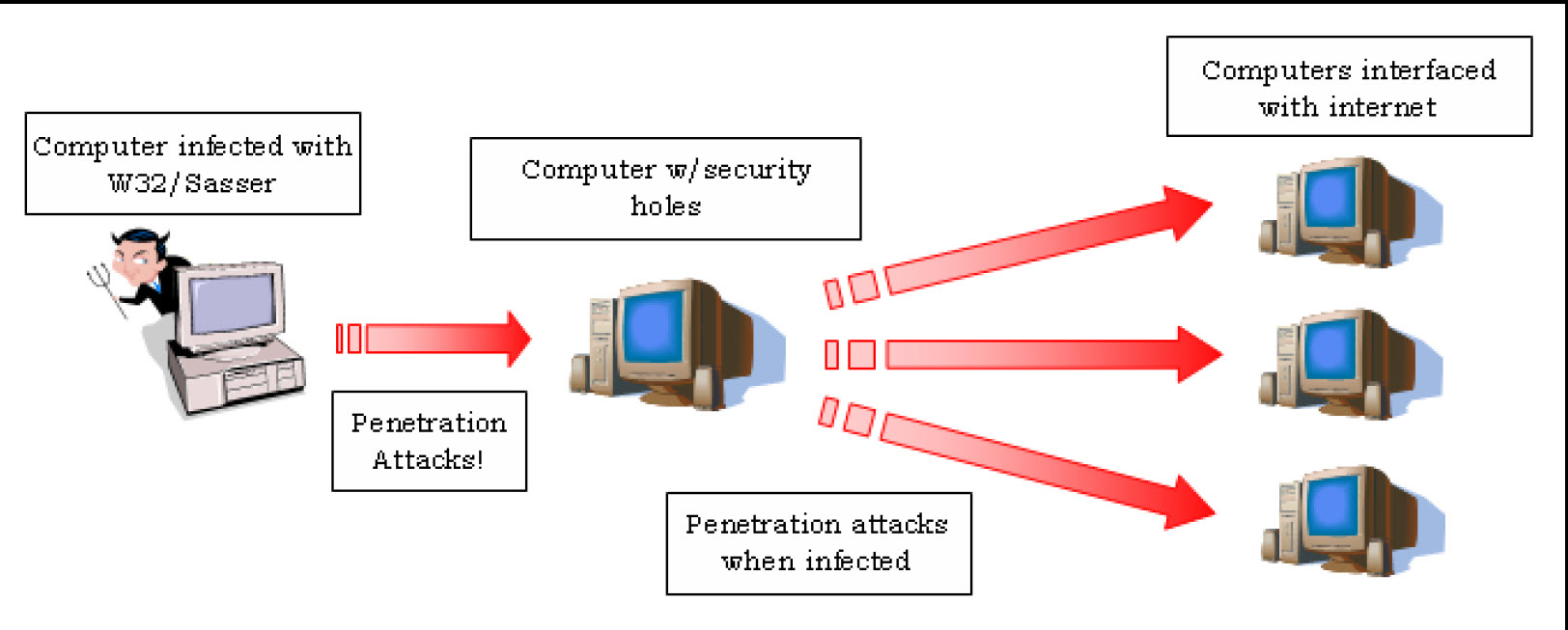
In 2013, the Bank of America was impacted by a web server worm that later was referred to as SQL Slammer. This took down several ATM services. The SQL Slammer worm leveraged a buffer overflow bug in SQL Server and the Desktop Engine database. When the machine was infected, the worm generated a random IP address, which it would use to distribute itself on other machines that had an unpatched SQL Server version installed.
Crypto worm
A crypto worm is a variation on a computer worm that is leveraged by threat actors for ransomware attacks. In general, crypto worms target unpatched or misconfigured computers by encrypting data and then demanding ransom for decryption.
Ransomware ( WannaCry)
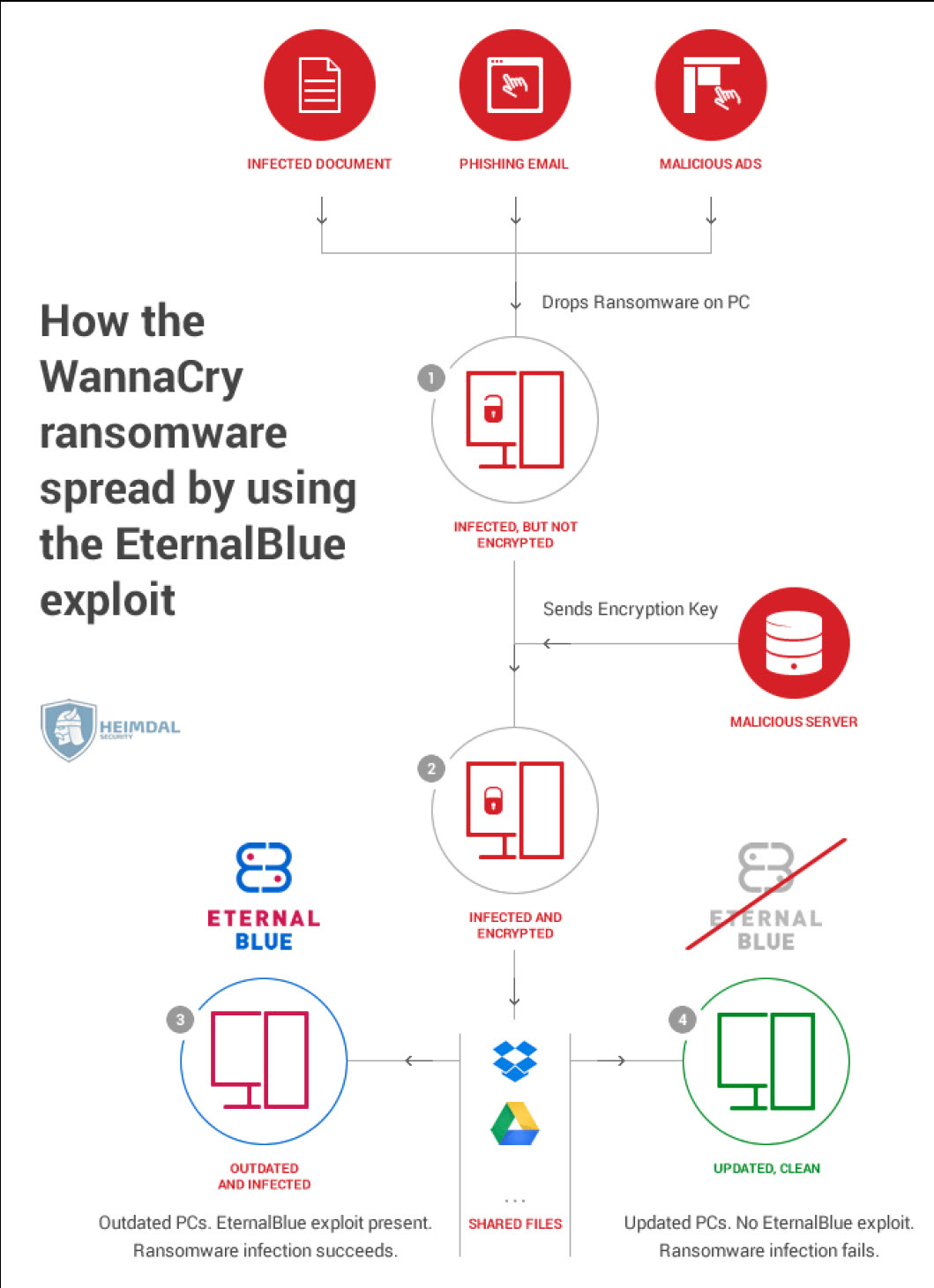
In May 2017, WannaCry (a global ransomware outbreak) impacted thousands of enterprises around the world. WannaCry was a ransomware attack performed by a threat actor group that leveraged a crypto worm. The targets were computers running an unpatched version of Windows, which it attacked by utilizing an SMBv1 vulnerability. WannaCry also leveraged the EternalBlue vulnerability to spread itself.
However, WannaCry was stopped fairly quickly. This was because Marcus Hutchins, a security researcher, discovered a kill switch, which is a programmed stop command, for WannaCry,
by registering a domain name that he had found in its source code:
Trojan
A Trojan is a piece of malware that deceives the target as to its true intent. The term Trojan has its origin with the ancient Greeks, who gave the city of Troy a wooden horse with soldiers hidden inside of it. Once the wooden horse was taken inside the city of Troy, the soldiers attacked. The most common delivery mechanism for a Trojan is through social engineering techniques such as pretexting, phishing, or spear phishing.
Unlike computer viruses or computer worms, Trojans are typically not injected into files or executable files. Similarly, Trojans do not replicate themselves like a computer worm. When Trojans started to arise, they were generally used for denial of service (DoS) attacks. A Trojan may do the following:
- Steal personal information
- Steal credentials (username/password)
- Copy confidential and/or sensitive data
- Perform harmful operations
In many cases, a Trojan attempts to open a port on the machine, which allows the threat actor to establish Command and Control (C2C) communication, which is then used to perform illegal actions:
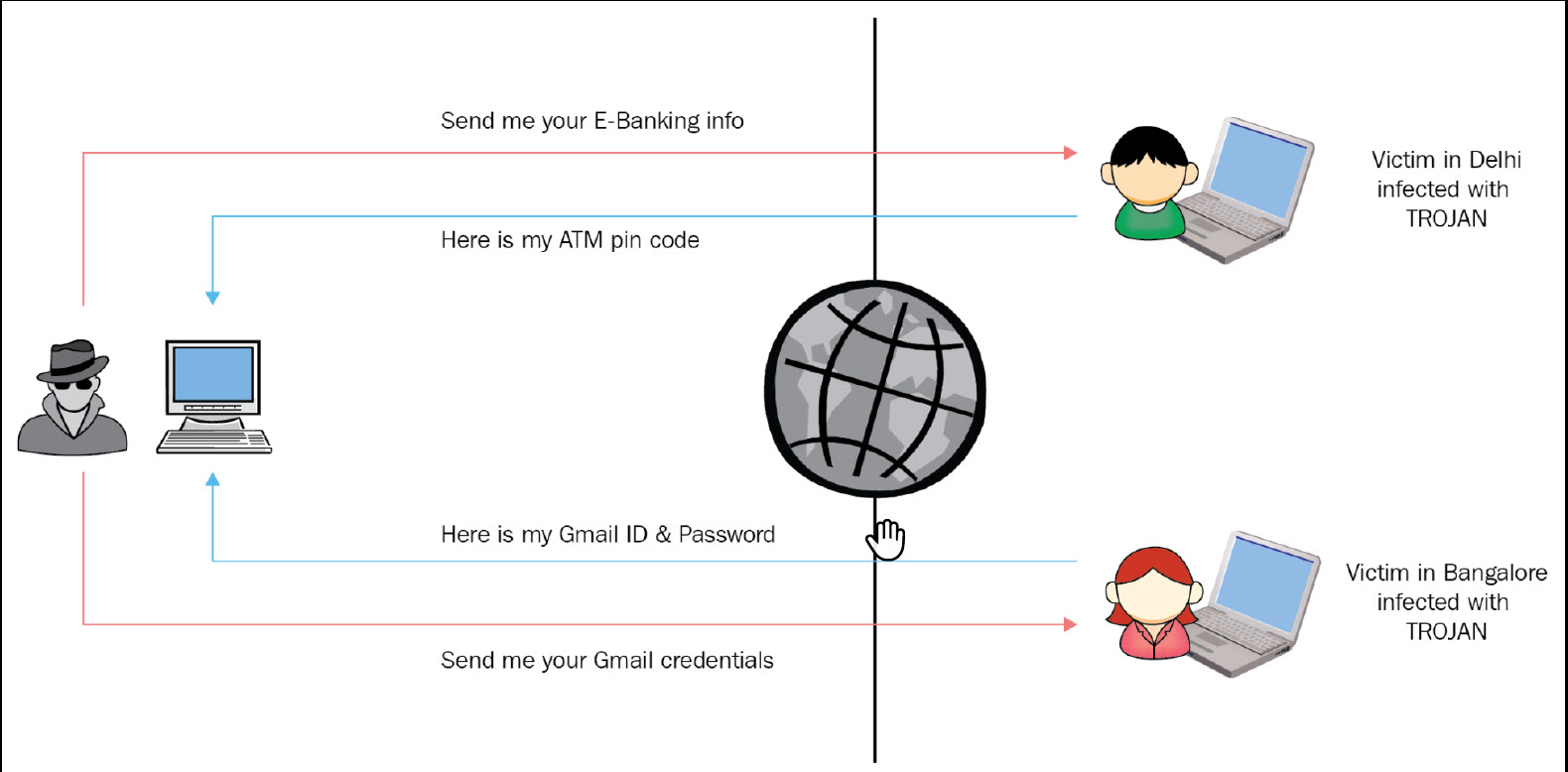
Bebloh
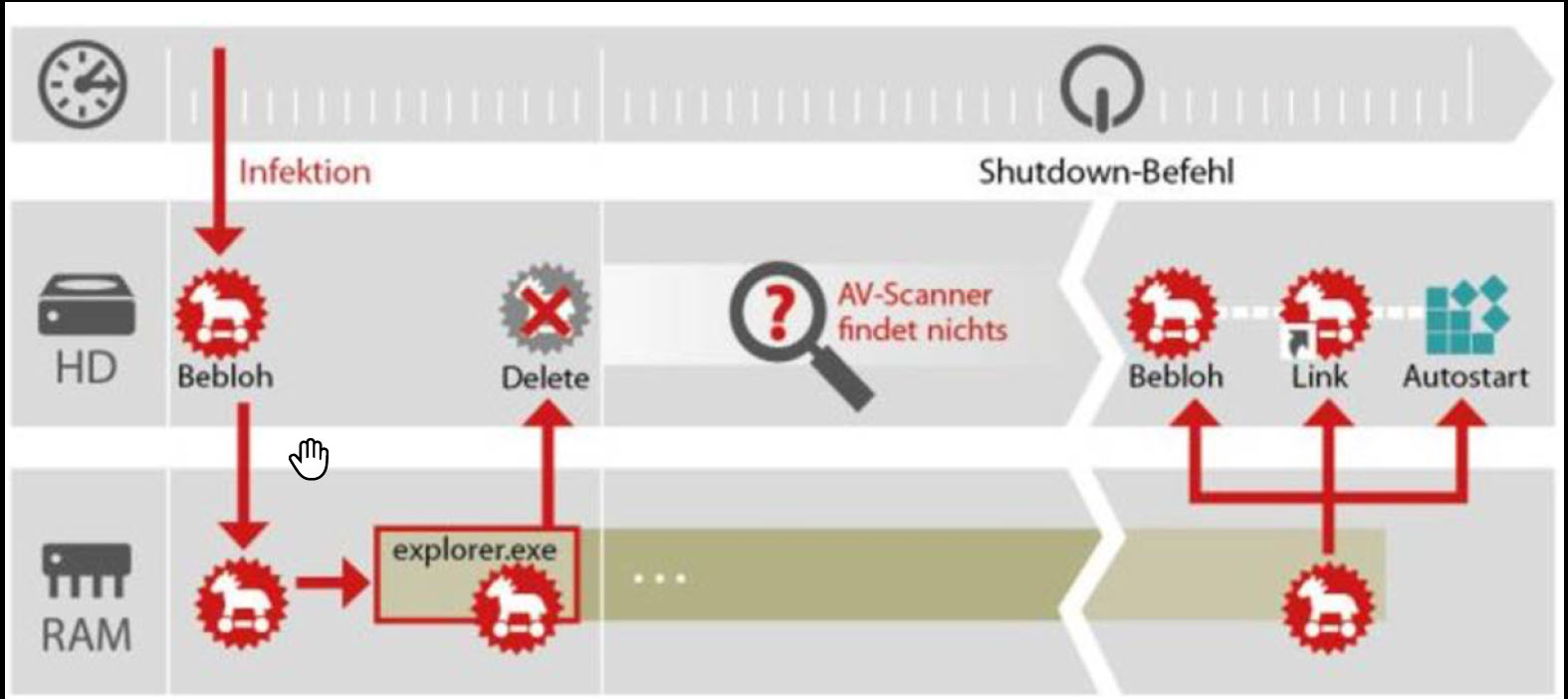
Bebloh is a banking Trojan that is used by threat actors in order to perform credential harvesting and inject the endpoint during a target’s online banking transactions. Bebloh is very popular as a banking Trojan because of its ability to change the balance shown on the target’s computer when logged in to the online banking portal. In order to achieve that, Bebloh leverages a man-in-the-browser (MitB) technique. The delivery of Bebloh is often hidden inside an email with a malicious PDF attachment that is sent as spam.
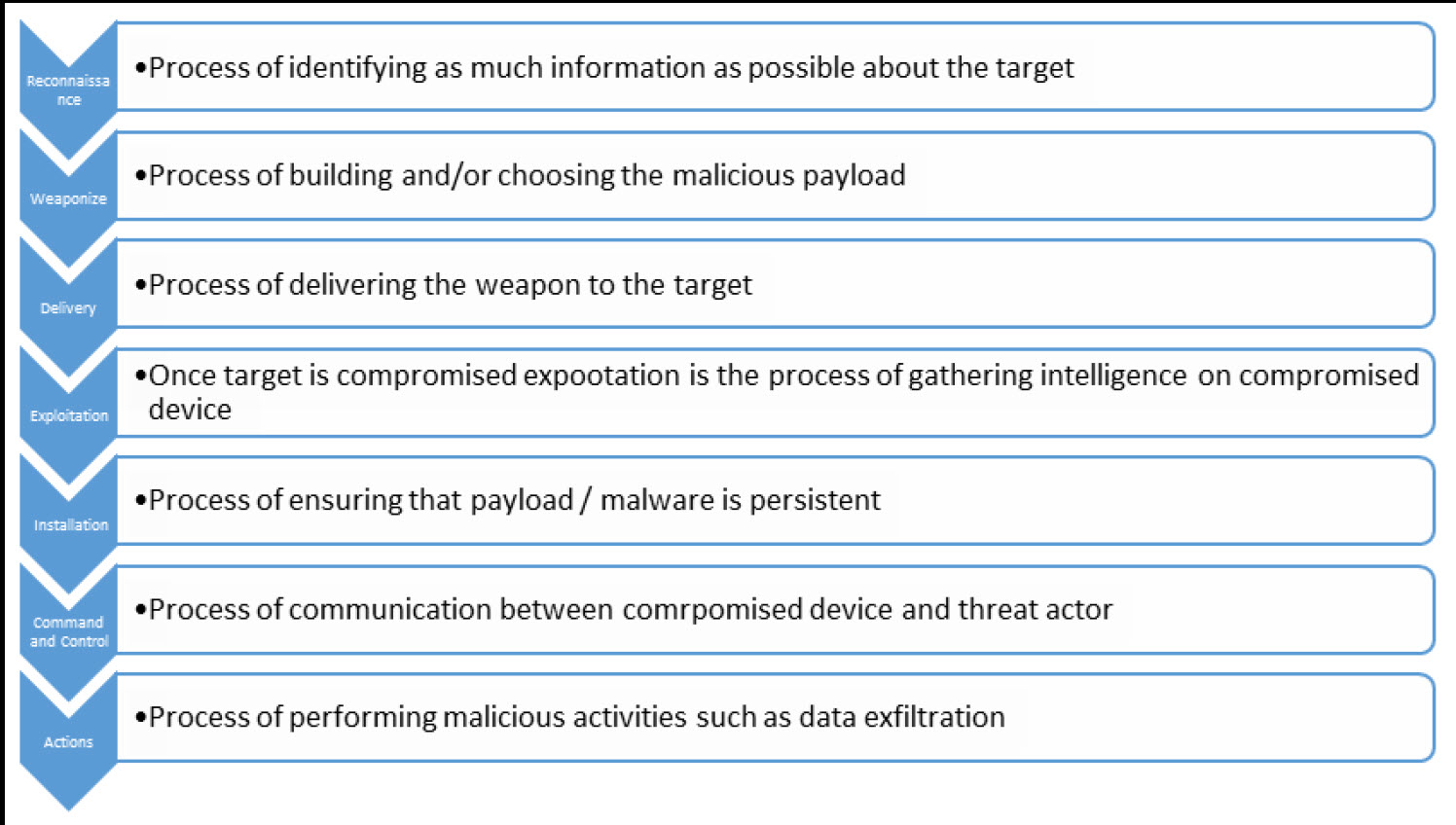
Bebloh makes use of a vulnerability in Adobe Reader 9.3, which causes the Adobe Reader to crash during that process and inject malicious code into the system. Bebloh was first discovered in 2009 and a number of German banks were impacted. The following diagram illustrates the kill chain of Bebloh:
Rootkit
A rootkit is a form of malware that enables other malicious payloads to make use of its privileged access on a computer. A rootkit can be installed either by leveraging a system vulnerability that bypasses account privileges, or when the threat actor has already compromised administrative privileges. Once the rootkit is installed, it allows threat actors to gain remote access to the computer’s low-level systems. A rootkit uses back door tools to modify an operating system and firmware to hide the threat actor’s steps. These back doors can operate either in user or kernel mode.
Torpig
Torpig is a technique first seen in 2005 that combined a banking Trojan, a botnet, and a rootkit. The botnet spread the banking Trojan Mebroot, which was then responsible for stealing the logon credentials for banking websites. The way that Torpig ensured that it wouldn’t be detected by antivirus software was by leveraging a rootkit exploit.
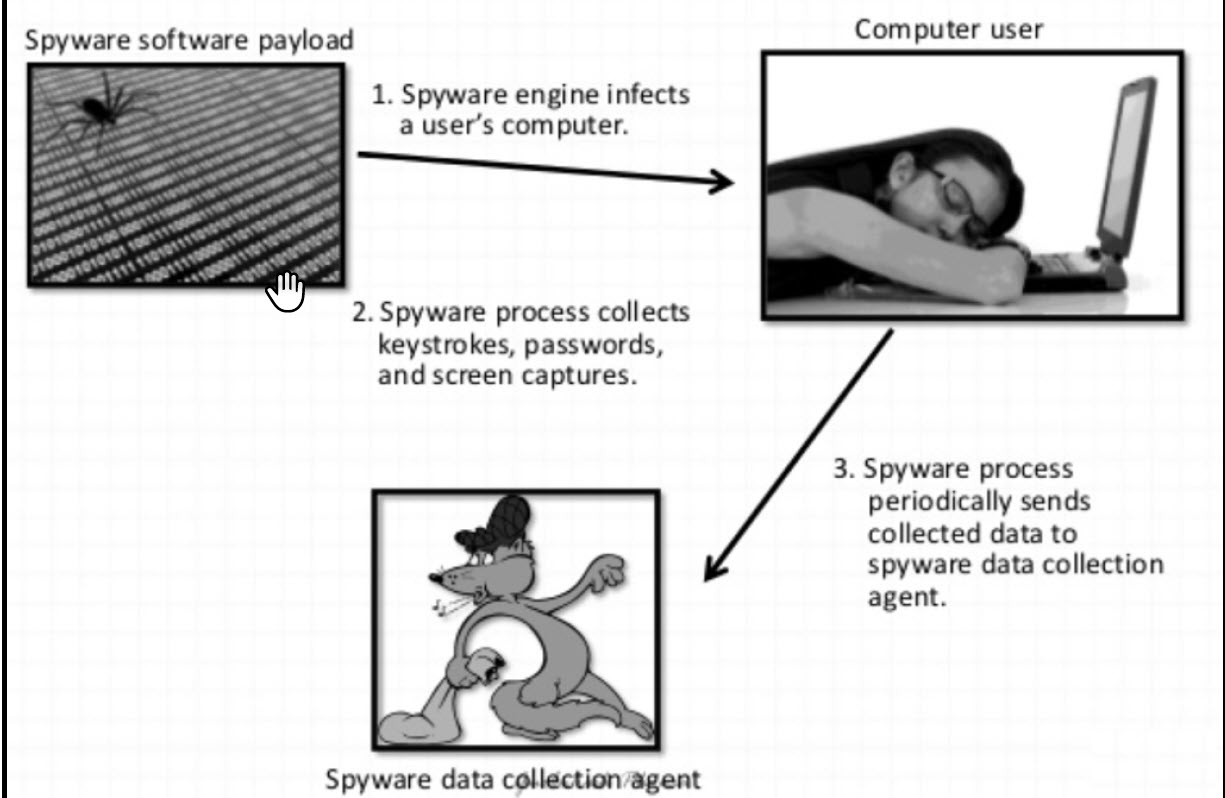
Spyware
Spyware runs in the background of a computer and its primary purpose is collecting information on the computer without the awareness of the target. The delivery mechanism for computer viruses, computer Trojans, worms, and spyware is the same. Often, spyware will contain Trojans such as keyloggers that track all the keyboard inputs of the target, banking Trojans that harvest online banking credentials, or password stealers that perform credential harvesting:
Adware
Adware is a type of malware that displays advertisements on the user interface of the target. Typically, adware is used to gather information on the target, particularly on their
internet behavior.
This is the first part of the article. You can read the second part here
Part 2: www.ErdalOzkaya.com
Which is the best free antivirus ?
Download the Best Free Anti Virus from Comodo





