Threat Hunter Assessment Tool: Free Forensic Scan
Threat Hunter Assessment Tool Technical review
Xcitium Threat Hunter Assessment Tool – Forensic Scan is a free software program that can be used to scan a computer system for evidence of malicious activity. The tool can detect safe, malicious, and unknown files on the endpoint, as well as scan the network, active directory, and user workgroups for potential threats. The tool can generate a report with the scan results and send it to the user by email.
The tool is designed to show the limitations of detection-based cybersecurity solutions, which cannot protect against unknown or zero-day threats that evade traditional signatures and heuristics. The tool claims to use a detection-less approach that treats unknown files as untrusted and guilty until proven innocent. This is supposed to provide true, machine-speed protection with zero dwell time.
The tool is easy to install and use, with a simple interface and a selection of scan types and targets. The recommended scan is the quick scan, which takes less than 10 minutes on average. The tool does not remove any discovered threats, but rather recommends using Xcitium’s Advanced Endpoint Protection, which is a paid product that can prevent 100% of unknown and malicious files from damaging the endpoints.
The tool is a useful way to assess the current state of endpoint security and identify any hidden or unknown threats that may be lurking on the system or network. The tool does not provide any comparison or benchmarking with other cybersecurity solutions, nor does it explain how it identifies unknown files or verifies their innocence. The tool also does not provide any support or warranty for its use.
A deep dive on Xcitium Threat Hunter Assessment Tool
A deep dive on Xcitium Threat Hunter Assessment Tool is a detailed analysis of the features, functions, and performance of the software program that can scan a computer system for evidence of malicious activity.
The tool can be downloaded for free from the Xcitium website1 and can be run on any Windows operating system. The tool does not require installation and can be launched from a USB drive or a network share. You can scan
- Active Directory
- Network Address
- Workgrouo
- And a single PC
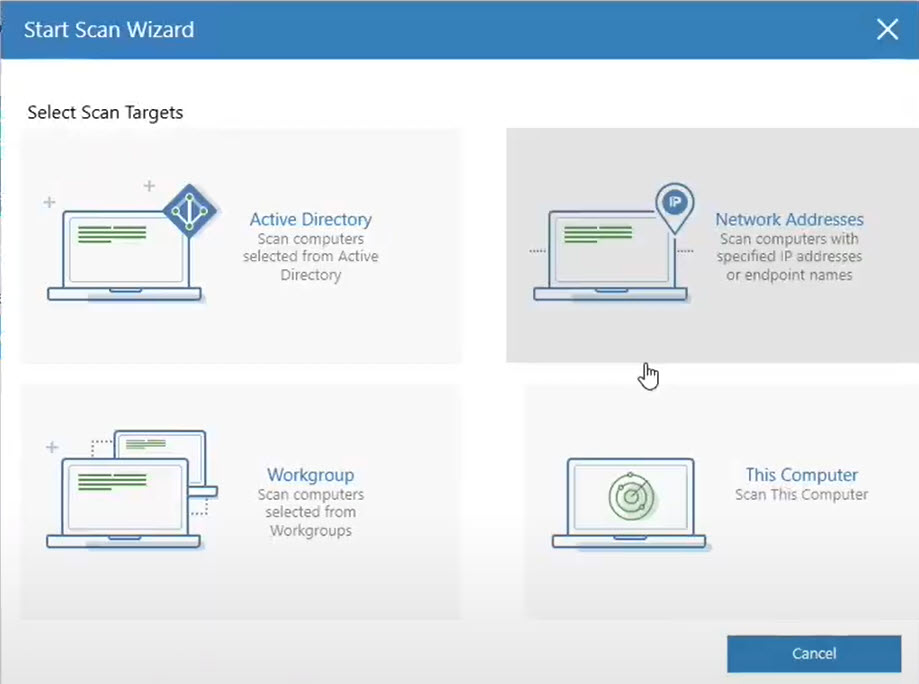
The tool has a simple and user-friendly interface that allows the user to select the type and target of the scan. The tool offers four types of scans:
quick scan, full scan, custom scan, and network scan.
The quick scan is the recommended option, as it takes less than 10 minutes on average and scans the most critical areas of the system, such as the registry, memory, startup items, and common malware locations.
The full scan is more thorough and scans the entire system, including all files and folders.
The custom scan allows the user to specify which files, folders, or drives to scan.
The network scan scans the network, active directory, and user workgroups for potential threats.
The tool uses a detection-less approach that treats unknown files as untrusted and guilty until proven innocent. The tool claims to use a proprietary technology called X-Engine that can analyze unknown files in real time and determine their behavior and intent.
The tool can detect safe, malicious, and unknown files on the endpoint and assign them a risk score based on their characteristics and reputation. The tool can also detect network anomalies, such as suspicious connections, traffic patterns, or protocols.
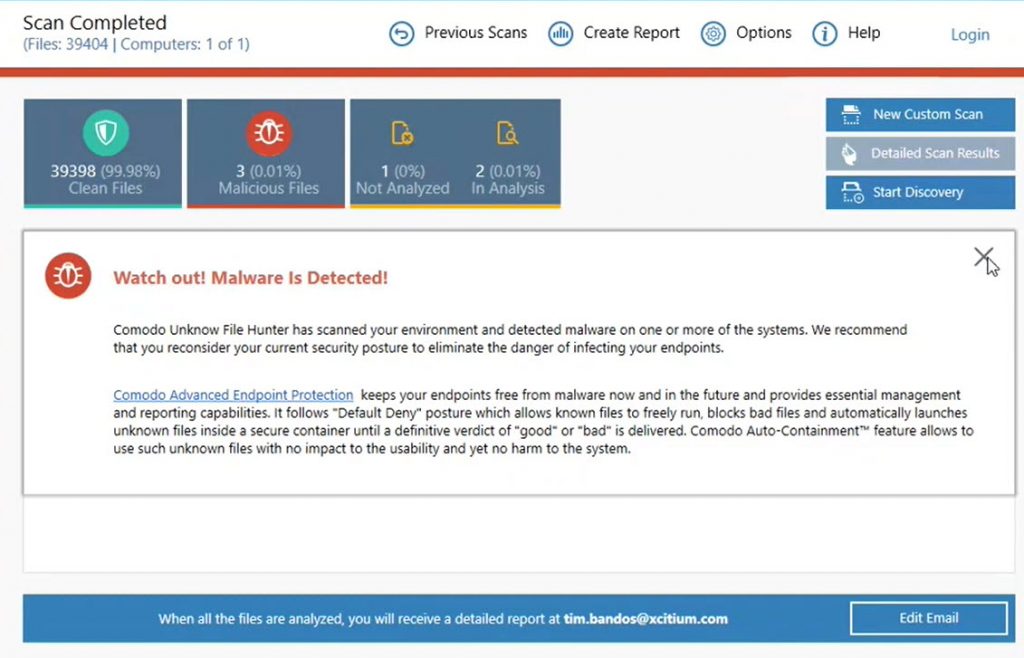
The tool can generate a report with the scan results and send it to the user by email. The report contains a summary of the scan statistics, such as the number of scanned items, detected threats, and unknown files.
The report also provides detailed information about each detected threat or unknown file, such as its name, location, size, hash value, risk score, behavior, and verdict. The report also provides recommendations on how to deal with each threat or unknown file.
The tool is designed to show the limitations of detection-based cybersecurity solutions, which cannot protect against unknown or zero-day threats that evade traditional signatures and heuristics.
The tool aims to provide true, machine-speed protection with zero dwell time by preventing 100% of unknown and malicious files from damaging the endpoints
The tool is a useful way to assess the current state of endpoint security and identify any hidden or unknown threats that may be lurking on the system or network.
Some of the pros and cons of Xcitium Threat Hunter Assessment Tool are:
Pros:
- It is a free and comprehensive tool that can scan the endpoint and the network for evidence of malicious activity.
- It can detect safe, malicious, and unknown files on the system and provide a detailed report with the scan results.
- It can show the limitations of detection-based cybersecurity solutions, which may miss unknown or zero-day threats that evade traditional signatures and heuristics.
- It can help users assess the current state of their endpoint security and identify any hidden or unknown threats that may be compromising their system or network.
Cons:
- It does not remove any discovered threats, but rather recommends the neccessary steps
- It does not provide any comparison or benchmarking with other cybersecurity solutions,
- It does not provide any warranty for its use.
Overall, Xcitium Threat Hunter Assessment Tool – Forensic Scan is a free and comprehensive forensic scan tool that can help users discover if their endpoints are at risk from undetected threats.
To read more malware related articles , click here
Title
Xcitium Threat Hunter Assessment Tool – Forensic Scan
Description
Detect malicious activity and potential threats with Xcitium’s free Threat Hunter Assessment Tool. Scan your system for safe, malicious, and unknown files, as well as network and user workgroups.





