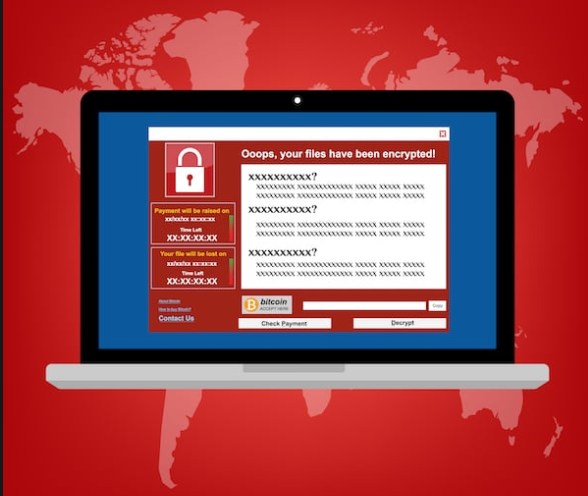
WannaCry Ransomware (Academic Research)
WannaCry Ransomware
It’s the Birthday of WannaCry, today the nasty Ransomware turns out 2 years old. For that “Special occasion”(!) I want to share the academic research paper which I wrote back then. Still interesting to read I believe
1. Introduction
WannaCry, also known as Wanna Decryptor, is a computer worm that targets devices running on the Windows OS . In a span of a few days after its release, it became one of the worst and most widespread malware. The ransomware is said to hunt for and infect vulnerable computers on the internet, rather than through phishing as is common with most other ransomware (Woo & McMillan, 2017).
Once it infects a computer, it finds a number of files and encrypts them then displays a pop-up requesting for the payment of some ransom. It has been charging $300 dollars to decrypt files within 72 hours past which the charges rise to $600 and threatens to permanently destroy files in seven days (McMillan, 2017). Its first infection was tracked down to Asia on 12 May 2017 and from then, it spread to infect over quarter-million computers in over 150 countries (Melba, 2017).
2. Background information
It is believed that the US National Security Agency developed an exploit called EternalBlue that was used to allegedly spy on computers. The exploit targeted a vulnerability in the Server Message Block of the Microsoft Windows operating system. EternalBlue allowed an attacker to execute any command on the OS . The exploit was released two months before the first infection of WannaCry by a group of hackers called the Shadow Brokers (McMillan, 2017). This group has notoriously been releasing NSA weaponized software exploits (Leonhard, 2017).
In 8 months, the group has released over 1GB of exploits made by NSA (Leonhard, 2017). Their release of EternalBlue is regarded as the most damaging. This prompted Microsoft to make patches for its operating systems to address the vulnerability . It also made patches for its older versions such as XP which it had ceased supporting in 2014 (McMillan, 2017). After its release, EternalBlue is believed to have been used by the makers of WannaCry to allow the installation of a backdoor tool called DoublePulsar to the victim computers (Melba, 2017).
This tool was also released by the Shadow Brokers group. With the tool installed, the hackers could execute the WannaCry code in the victim computers and encrypt files.
3. Discussion
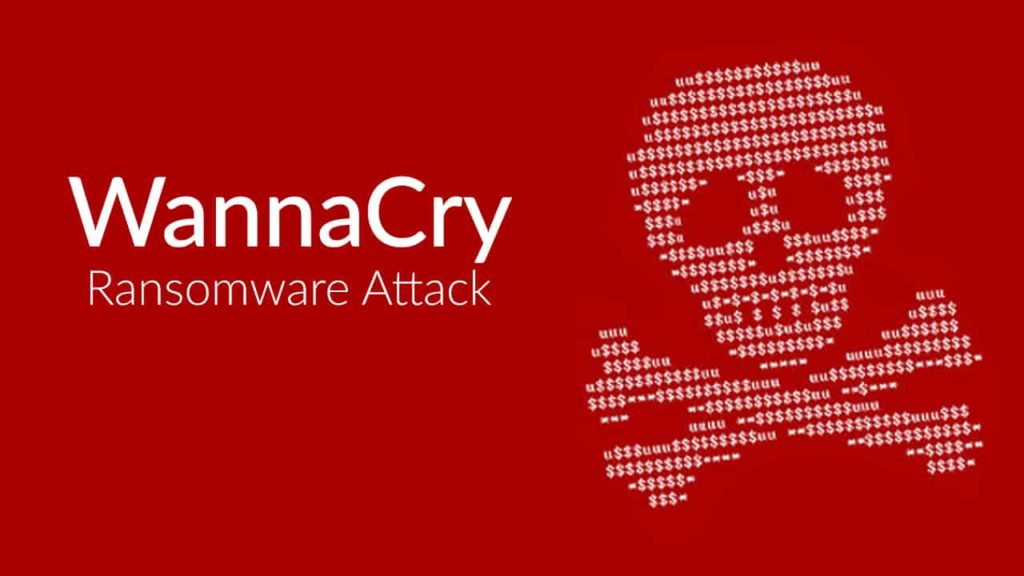
3.1 The attack
As has been said, the malware hunts for vulnerable computers on the internet. It also uses the computers that it has infected to spread itself to more computers in a given network. It is being reported that, after infecting a computer, the ransomware first checks its kill switch domain name. This kill switch enables the virus to tell among other things where it is being run from and whether or not it is being run in a controlled environment. It is said that it will terminate itself in a scenario that it identifies that it’s being run in a controlled environment such as a virtual machine.
The kill switch might have been made in an attempt by the malware creators to avoid the virus from being studied and its countermeasures developed. Unfortunate for the creators, the kill switch domain name has already been identified and activated. This has, in turn, reduced the number of new infections. It is said that, after the malware checks with the kill switch and does not find the domain name, it proceeds to encrypt its host’s data. It then displays the pop up showing the attacker’s demands which currently are certain amounts of money depending on the number of days taken to make the payment. The payment is done through bitcoin, a cryptocurrency that gives anonymity to the parties in a transaction.
It was at first said that earlier versions of Windows such as Windows XP and Windows 2003 were most vulnerable to the malware. However, Microsoft released updates for these operating systems in April 2017 despite its decision not to continue supporting them. Most of the computers that have been infected have been said to be running on newer versions of Windows with Windows 7 leading the list. Microsoft says that updating the Windows OS prevents this malware from infecting computers. Tests have shown that the updates supposedly prevent the virus from spreading to computers in a network. However, the malware will still infect the updated computers if run directly on them as an executable.
3.2 The Kill switch
The discovery of the kill switch was the turning point of the seemingly never-ending menace that the WannaCry malware had spread. It was the most defining moment of the attack progress whereby thousands of computers had already fallen victim. The kill switch was identified by a malware analysis expert known as Marcus Hutchins who was among the first people to examine the WannaCry ransomware. He stumbled on a way to effectively stop it from encrypting computers and this led to a down surge of the number of new infections.
As he was reverse-engineering the malware he discovered that it was first checking a certain URL and then either executing or terminating itself. Out of curiosity of why the malware was checking that URL, Marcus Hutchins searched for the domain name, found that it was available and bought it for $10.69. It turns out that this meager investment would be what would stall the virus and save the world. When the domain name was unregistered and therefore inactive, the queries it made were supposed to have no effect and therefore enable it to infect and spread to computers.
However, when the domain name was found to be active, the virus shut itself down. There are a few explanations to this. One is that the creators made the kill switch intentionally in order to remain in control of the malware and shut it down in case it came out of hand. Multiple analysts of the malware have confirmed that the kill switch was intentionally made for this purpose.
The other possibility, as was said, is that the kill switch was put in place to prevent the malware from being analyzed in controlled environments. It is being argued that it was an anti-analysis defense but it was poorly implemented. In a controlled environment, malware are tricked into believing that they are running on real victims and querying actual IP addresses. In the actual sense, the malware are normally sandboxed in a secured environment and they query dummy IP addresses. Therefore, just about any URL that they query will bring back results, including non-existent domain names.
The creators must, therefore, have used one unregistered domain name to first check whether the malware was running from a test environment and auto-destruct if it was the case. It was poorly implemented because anyone who could find the domain name and register it would make the malware think that it was executing on a test environment continuously and therefore fail to execute. This possibility is being given most attention because after the domain name was registered, the malware almost immediately stopped claiming new victims.
3.3 Temporary fix
It is believed that Hutchins has given a temporary fix to the malware problem but it is not known for just how long. The malware analyst has since directed all traffic to the site to a server environment to capture malicious traffic. He has effectively created what is referred to as a sinkhole. His temporary fix has bought time to all the computers that had not updated to the said patch that Microsoft released for its operating systems to do so. Thankfully, Hutchins had the required infrastructure to sinkhole the domain. Otherwise, the malicious requests would quickly overwhelm a poorly designed sinkhole and allow the malware to continue infecting more computers.
3.4 Resurrection of the virus
A few days after the domain had been bought, there were attempts being made to resurrect the ransomware. Multiple DDOS attacks had started being made on the domain name. It is believed that once the DDOS attacks overwhelm the domain name, the malware will come back to life and continue infecting computers. The aim of the DDOS attacks is to make the URL unavailable again. Therefore, queries made by the malware to the domain name will bring back no results and it will continue executing to infect more computers and spread itself in networks (Layak, 2017). Hutchins says that he has enlisted a DDOS mitigation firm to keep the attacks at bay.
There are also fears that an updated version of the malware will be soon released. The update will most likely have a way to get around the kill switch that has led to the ‘failure’ of the current strain. All it takes is the exclusion of the kill switch in the code of the malware. This would be more dangerous as even the creators would not be in control of how far that the malware could go. Alternatively, the creators could use a dynamically changing IP addresses to do the test environment check.
4. Conclusion
The paper has looked at one of the newest yet most dreaded malware in the world. It has traced back the origins of the malware and how several exploits were put together to enable a simple encryption tool to be used as a weapon. It has discussed who is believed to have made the SMB exploit to take advantage of Windows OSs and how the exploit was leaked. The paper has also discussed how a tool called DoublePulsar was used to create a backdoor to inject the WannaCry code into the victim computers (Melba, 2017). The paper has explained procedurally how the attack was being conducted.
The role of the kill switch in the WannaCry malware has been discussed as well as how it was used to effectively bring a temporary end to the menace. The research paper has explained how a malware analyst identified the kill switch, bought the domain and directed all the requests to the domain to a sinkhole. It has looked at the effects of the activation of the domain name to the procedure of the execution of the malware. Lastly, the study has discussed how attackers are trying to resurrect the malware through DDOS attacks. Recommendations on how to combat such an attack in the future have been discussed.
5. Recommendations
There are a few ways in which internet users can prevent or mitigate this kind of an attack. To begin with, users must install the latest patches to their operating systems (Rashid, 2017). In the case of this malware, it had already been discovered and allegedly weaponized by the NSA (Leonhard, 2017). However, it fell on the wrong hands and was leaked to the creators of WannaCry. When Microsoft came to know this, an update was released but two months down the line, most computers had not installed it.
As a result, there were many computers vulnerable to a totally avoidable malware. Another recommendation is for users to ensure that their computers have an updated antivirus program. In one of the tests, an analyst ran the malware on a Windows 7 OS that had not been patched but had a trial version of Avast Antivirus (McMillan, Gross & Roland, 2017). The antivirus successfully prevented the execution of the malware. This shows the essence of an antivirus program on a computer.
Another recommendation is the backing up of the contents of one’s computer. There are multiple options today for backing up with the cloud leading as the most secure and reliable one. A ransomware will only encrypt the files on the hard disk of a computer but will not access the backed up copies in external storage media or the cloud. Therefore, if at all a computer is infected, a user can simply wipe its hard disk, install a clean OS and transfer the backed up files back to the computer.
Lastly, if a computer is infected, even there are no backups are available and the files that have been encrypted are of high value, it is never good to pay the ransom fee.
References
Woo, S., & McMillan, R. (2017, May 15). Cybersecurity experts try to understand how ransomware invaded networks; investigators think a digital computer outlet that isn’t supposed to be connected to the internet was a possible vector for WannaCry. Wall Street Journal (Online) Retrieved from https://search.proquest.com/docview/1898709140
Leonhard, W. (2017). FAQ: Are you in danger from the WannaCry ransomware?InfoWorld.Com, Retrieved from https://search.proquest.com/docview/1899008262
McMillan, R. (2017, May 17). New threats fuel fears of another global cyberattack; A new attack hit thousands of computers and a hacking group said it would release more attack software. Wall Street Journal (Online) Retrieved from https://search.proquest.com/docview/1899472434
Rashid, F. Y. (2017). WannaCry ransomware slipped in through slow patching.InfoWorld.Com, Retrieved from https://search.proquest.com/docview/1899007972
Melba, B. (2017). ‘WannaCry’ ransomware hits thousands of asian businesses. Newton: Questex Media Group LLC. Retrieved from https://search.proquest.com/docview/1898773761
Layak, S. (2017, May 21). Ransomware: The extortionists of the new millennium internet]. The Economic Times (Online) Retrieved from https://search.proquest.com/docview/1900413817
McMillan, R., Gross, J., & Roland, D. (2017, May 13). Hackers launch global assault. Wall Street Journal Retrieved from https://search.proquest.com/docview/1898644073
https://www.erdalozkaya.com/cybersecurity-attack-and-defense-strategies-second-edition/
https://www.erdalozkaya.com/cybersecurity-attack-and-defense-strategies-second-edition/





