
10 Cybersecurity Myths You Need To Stop Believing
10 Cybersecurity Myths You Need To Stop Believing
01. No one cares about you or Your business is too small for a cyber attack!
02 . Your Anti-virus is good enough
03 . Your Passwords are Strong and hard to guess
04 . Your industry doesn’t have any cyber threats
05 . Bringing your own device is safe
06 . We have a Perfect Cybersecurity Strategy
07 . Cyber Threats are only external
08 . IT department will take care of it
09 . We don’t need tests or training
10 . We will see any attack or the malware right away
Cybersecurity Myths
01. No one cares about you or Your business is too small for a cyber attack!
There are so many induvial’ s or Small and Mid-Sized Businesses think that they are safe from any kind of cybersecurity attacks because they’re too small , or no one cares about them.
Cyber security is important for individuals because:
- Cyber-attackers can cause damage you via cyber-attacks such as IT theft, phishing, email spoofing and cyber extortion or make you a direct target and to be their victim.
- As a direct victim you can have financial impact , privacy loss or even Intellectual Prosperity losses as an Autor, singer
02 . Your Anti-virus is good enough
Anti Virus by itself can never protect you from an advanced cyber attack by itself. Most of the Anti viruses relays on a database & signature updates, some of them have also behavior analysis, which can protect you bit more, but if your devises are not up to date, if you allow to run a unknown application with full write privileges then there is not much what your software can do. You need a complete Advanced End Point Detection system with much more then just being a Anti Virus . If you need more info Comodo AEP can help you with this.
03 . Your Passwords are Strong and hard to guess
Unfortunately you are not the only one who thinks like that , most people think like you and they assume that their regular passwords are strong enough to stand against multiple break-in attempts. Cracking Passwords is much easier then you think, and the below list is a good example to show you how
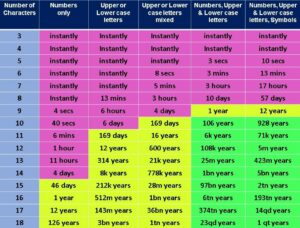
Now if you have a complex password with 18+ digits, yes it might take long to brute force your password , but it will not take long to steal your hash , without even worrying to know your password. You can learn more about this in my book Cybersecurity Attack and Defense Strategies
04 . Your industry doesn’t have any cyber threats
I guess by know you know why this statement is wrong too! Not every hacker is part of Nation State or APT’s , or not every hacker is always after the big fish, as a result you have to take care as an individual, small business or what ever industry you are in
05 . Bringing your own device (BYOD) is safe
BYOD is for sure cost effective for organizations, but today everyone is realizing the importance of Zero Trust , as a CISO if you don’t have the right policies to manage BYOD devises then you might expose more risk in to your organization.
You need to establishing minimum standards for device protection (including formal policies for bring-your-own-device (BYOD) , it’s a must!
06 . We have a Perfect Cybersecurity Strategy
I am sure you have, but then how come so many Fortune organizations are still getting hacked ? As long as a Human Factor is getting involved, no body can be perfect !
A cyber security strategy involves implementing the best practices for protecting a business’s networks from cyber criminals. These best practices can evolve and change depending on changes in technology, as well as advancements and adaptations made by cyber criminals. You need to Plan, Check, Implement your strategy well, you need to “do” the right thing and continuously improve your Cyber Strategy it
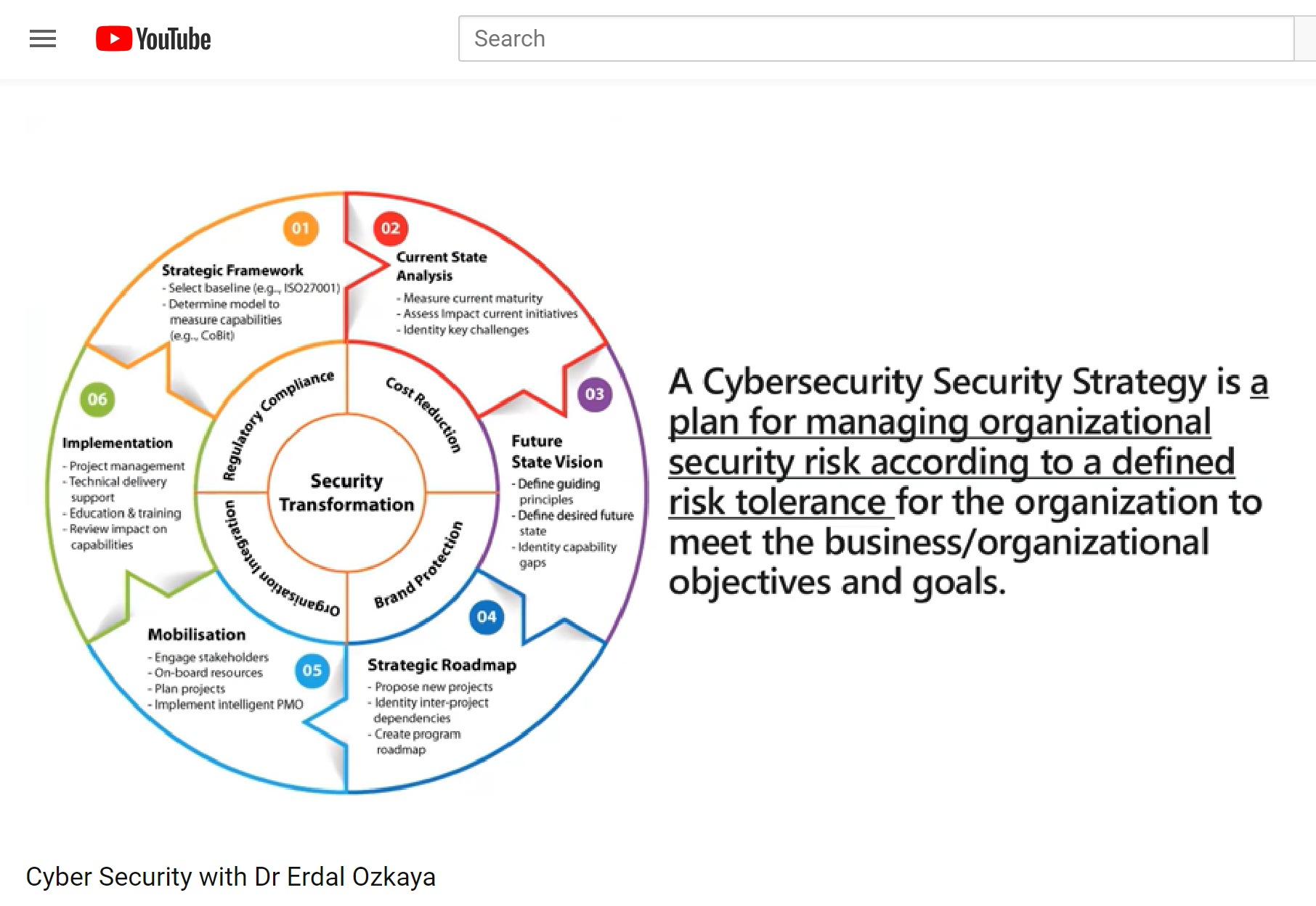
07 . Cyber Threats are only external
I wish there were no such a term like “insiders”. I am sure you came across many Hollywood movies where an insider helps the people outside to come in, or to leak information, and unfortunately this applies in cyber space as well, Even at NSA ( Edward Snowden) , Tesla ( Employee Fired to downloads company secrets) and there are many more examples like this.
So what is an Insider Threat ?
An insider threat refers to a cyber security risk that originates from within an organization. It typically occurs when a current or former employee, contractor, vendor or partner with legitimate user credentials misuses their access to the detriment of the organization’s networks, systems and data.
08 . IT department will take care of it
Your CIO and IT department can handle it ! Yes, IT play a very critical role on any organizations success. The IT department can implement, manage devises, policies but I still believe that every organization needs a CISO which does not report to CIO .
Saying that neither the CIO or CISO can just take care of “Cybersecurity ” but they can create a culture in the organization where everyone can contribute towards cybersecurity, and this can be archived via customized Cyber Awareness training for each departments . If every employee , contractor , partner understands the cyber risks which faces them then they will for sure help you mitigate potential threats such as spear phishing.
09 . You don’t need Penetration tests or training
Do you have your own internal Penetration Tester /s ? No ? You for sure need at least once a year an external pen test. Yes? this is great , but you still need to be tested.
While your team can find most of the internal vulnerabilities, cyber risks via tools ,its important to cover all your assets end to end including your web / cloud assets.
Training means budget, I am fully aware of this. But just looking at some Data breach reports like Verizon‘s will show you clearly that most of the cyber attacks happens because of “misconfiguration” ‘s and misconfiguration usually is done because of lack of knowledge, and knowledge can be improved only with training.
Books will be helpful, that’s why I am writing books like many other other authors, same with Blog’s, hey look at it you are currently either at my LinkedIn page, or in my blog ( or in someone else’s who copied this article – which is OK), us bloggers share lots of valuable information, but most of the articles are designed around a single issue, and not end to end training of a product, service or framework. Of course there are great YouTube Video’s to watch, but unless those video’s are covering end to end a training, and you do not spend a dedicated time to watch and learn them, then you need a “training”
10 . We will see any attack or the malware right away
Based on many data breach reports, it takes up to 100+ days to find a hacker inside your network. Earlier in this article I recommended few products , but don’t forget there are so many different attack vectors, like Social Engineering which is very hard to detect.
Your IDS / IPS, security agents , HIPS or defense in depth strategies are all very important, but never enough to stop a sophisticated attack. While a “containment technology” can help you to see the malware’s , unknown executables, you need to be also in control of your network devices including IOT , in top of your DLP and other software vulnerabilities and more….
In Summary
There is no way to stop a cyber attack, you should adopt the assume breach methodology, have a incident response plan, implement defense in depth, know your crown jewels and keep learning….
Cybersecurity Myths – 10 Cybersecurity Myths You Need To Stop Believing 10 Cybersecurity Myths You Need To Stop Believing 10 Cybersecurity Myths






