
4 Cybersecurity Questions Boards Need to Address and Beware of!
4 Cybersecurity Questions Boards Need to Address
The world has changed a lot since the first case of COVID was found in Wuhan, the virus did not just effect our day to day life’s but also our work . As a board member of an organization how much do you understand about Cybersecurity ? Do you have the right advisors who can help your board to be cyber aware and empower the right person to help the organization stay secure ?
If yes answered any of this questions as yes then you are reading the right blog post. This blog post is going to be about how Boards of any size of a company can ensure their CISO /CIO or IT teams are doing the right thing to protect their business. Let’s start !
We all know that there are two type of organizations
- The ones they know they are hacked
- The ones they don’t !
Any company regardless of their size should assume breach and take the right approach to minimize their effect in case of a cyber attack. While there is two types of organizations of course there is also two types of boards.
- Those that approves their teams to take a defensive posture related to their security
- Those they empower their teams to take offensive approach
It’s a famous saying by entrepreneurs that they hire are smarter people then themself , while I saw many hiring managers they do the opposite, also at a board level!. Someone with good connections can be easily hired in C -Level Technical positions, and in my career I helped many of those to get back to their business through Incident Response teams 🙁 A good example for this can be the famous SolarWinds attack , where the ex CEO and current top executives blamed an intern for using a password “SolarWinds123” ! Don’t you think it was a lame excuse ? So what are you doing not to be in the same sport as those executives ?
By now any board member should know that Cybersecurity is not just a cost center and a technical element. IT is a “key” component that can transform business and if the technology is used correctly IT is actually a profit center . Look at companies that invested in the cloud way before COVID, and how easy they transformed from working in the office to remote !
Boards should support innovation, and innovation is mostly done with technology. While Technology is important , securing it is of course as important , that’s why ask Boards should tasks their executive management to have Incident Response in place, foreseen any possible cyber attack and in case it happens how to get back online as soon as possible , and while the tech teams will be busy doing that they should know how to communicate this with their customers / partners /media and of course the regulators / government. Boards needs to be minded innovative and resilient.
Ok then, what are the 4 key questions boards needs to address ?
1- How can IT help to make revenue ?
Your Digital transformation program is not just about technology, but also Risks. While Technology is implemented used, risk management should identify any possible gaps , and any gaps which can not be mitigated should be known by the Board,
2- What is your Cybersecurity Strategy ?
In other words what does cybersecurity mean to your organization?
As the board you need to know the consequences if your organization is breached, how to respond to not just the attack but also customers, share holders , partners , and more ! The Boards needs to approve the “Cyber Risk Framework ” The possible exposers needs to assessed for impacts based on metrics such as response time, cost and legal or compliance implications, and planned for to attract investment commensurate to a risk-based assessment.
Any board should know need what information is business critical, you need to be able to answer the below questions with our any hesitation :
- What your crown jewels are and how you can protect it.
- As board do you to have a periodic review of your cyber resilience program.
- Is the Cyber strategy aligned to your business risks ?
- Are those risks identified ? Do you monitor the risks , and if yes how ? What are the escalation metrics ?
- What is the people strategy around the business and is this also aligned with your Cyber Strategy ? Does the cyber strategy cover insider risks and how you do monitor /mitigate the risk?
- What is the relation with your Partners / Third Parties . Is the relation with your supply chain part of your cyber strategy ?
All the answers for the questions above will give you “satisfaction” on how your critical information , assets and data are secured. The board should have confidence on what is done in the IT space and how it effects the organization.
And the final step about the stagy will be about how the budget is aligned and how the recourses has been allocated to make the Cyber Strategy a successful. In other words the ROI needs to be clear.
3.As a board, what is our plan to develop in the areas in which we’re lacking?
Appointing ownership for the cyber security project is important . Its also important to know / understand the legal implications of cyber risks , the ownership of the Cyber plan, ( The Chief Information Security Officer – CISO) should be empowered to implement the strategy with success and reach to any of the board member as necessary , when needed.
4. Does the board has the right committee to understand cyber matters ?

Most of the boards have external advisors , and its really important to select the right advisor who understands not just business but also Cybersecurity to its core.
I saw many “external board advisors ” which are again assigned based on “recommendations” which is not wring for sure, but if the recommendations comes from a board who is not aware that they are “cyber ready’ then the recommendation is not going to be right !
Again through my career I met many advisors wondering how they were advising others while themself had no clue of even the basics of Cybersecurity . For sure they were excellent communicators using the right buzzwords , based on some articles they were reading.
There will be more blog post in the near future about this topic, so please keep an eye at my LinkedIn page or here to read more.
If you think you need help to understand Cybersecurity better, you might read my new book , which you can see the details below :
Cybersecurity Leadership Demystified
A comprehensive guide to becoming a world-class modern cybersecurity leader and global CISO
Key Features:
- Discover tips and expert advice from the leading CISO and author of many cybersecurity books
- Become well-versed with a CISO’s day-to-day responsibilities and learn how to perform them with ease
- Understand real-world challenges faced by a CISO and find out the best way to solve them
Book Description:
The chief information security officer (CISO) is responsible for an organization’s information and data security. The CISO’s role is challenging as it demands a solid technical foundation as well as effective communication skills. This book is for busy cybersecurity leaders and executives looking to gain deep insights into the domains important for becoming a competent cybersecurity leader.
The book begins by introducing you to the CISO’s role, where you’ll learn key definitions, explore the responsibilities involved, and understand how you can become an efficient CISO. You’ll then be taken through end-to-end security operations and compliance standards to help you get to grips with the security landscape.
In order to be a good leader, you’ll need a good team. This book guides you in building your dream team by familiarizing you with HR management, documentation, and stakeholder onboarding. Despite taking all that care, you might still fall prey to cyber attacks; this book will show you how to quickly respond to an incident to help your organization minimize losses, decrease vulnerabilities, and rebuild services and processes. Finally, you’ll explore other key CISO skills that’ll help you communicate at both senior and operational levels.
By the end of this book, you’ll have gained a complete understanding of the CISO’s role and be ready to advance your career.

What You Will Learn:
- Understand the key requirements to become a successful CISO
- Explore the cybersecurity landscape and get to grips with end-to-end security operations
- Assimilate compliance standards, governance, and security frameworks
- Find out how to hire the right talent and manage hiring procedures and budget
- Document the approaches and processes for HR, compliance, and related domains
- Familiarize yourself with incident response, disaster recovery, and business continuity
- Get the hang of tasks and skills other than hardcore security operations
Who this book is for:
This book is for aspiring as well as existing CISOs. This book will also help cybersecurity leaders and security professionals understand leadership in this domain and motivate them to become leaders. A clear understanding of cybersecurity posture and a few years of experience as a cybersecurity professional will help you to get the most out of this book.
To order from Amazon click here :
he book will help you to answer questions like
- Why is leadership important in cyber security ?
- Learn tp be effective cybersecurity leadership
- Who should lead cyber security ?
- What are the attributes of cyber security ?
- How CISO’s can reduce risks ?
- What is a security leader?
and you will learn :
- cybersecurity executive education
- cybersecurity leadership principles
- cybersecurity leadership training
- roadmap for cyber security career
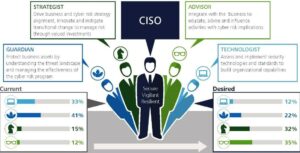
4 Cybersecurity Questions Boards Need to Address





