Digital Transformation Dubai – Free Event May 2023
Digital Transformation Dubai – Free Event
The 2023 Digital Transformation Conference is designed for optimal visitors’ experience. Thus, seats are limited, and attendance is by invitation only , and I will be part of it delivering the keynote
Secure your ticket. Register now.
WHERE
Radisson Blu Hotel, Deira Creek – Zabeel Ballroom
Baniyas Road, Deira, Dubai, United Arab Emirates
WHEN
3 May 2023 | 09:00 – 17:30
My Sessions
- THE REALISM THAT IS THE METAVERSE
- THE PAPERLESS BUSINESS ERA
For more info, click here
ABOUT THE CONFERENCE: DIGITAL TRANSFORMATION OF ENTERPRISES.
Digital Transformation is the way forward to enable organizations to improve current processes. Businesses need to evolve to remain competitive. However, only a few companies can claim that they have effectively transformed their processes.
MAHAM Consulting is working closely with industry leaders .
PAPERLESS, DOCUMENT CONTROL, BLOCKCHAIN, METAVERSE, OR WHAT ELSE
Whatever makes you interested to join us in the MAHAM Digital Transformation Conference rest assured that we promise you a real investment of your time. We’re really looking forward to seeing you there.
HERE IS WHY YOU WOULDN’T WANT TO MISS THIS CONFERENCE:
- BRIDGE GAPS IN TRANSACTING WITH THE PAPERLESS GOVERNMENT
- CONNECT ALL THE DOTS THAT MAKE UP DIGITAL TRANSFORMATION
- GAIN INSIGHTS FROM REAL-LIFE USE CASES AND ACTUAL IMPLEMENTATION
For more events info, click here
METAVERSE
The metaverse is the next evolution in social connection and the successor to the mobile internet. Imagine a set of digital spaces that you can move seamlessly between.
Like the internet, the metaverse will help you connect with people when you aren’t physically in the same place and get us even closer to that feeling of being together in person.
Based on Wired Metaverse is :
To help you get a sense of how vague and complex a term “the metaverse” can be, here’s an exercise: Mentally replace the phrase “the metaverse” in a sentence with “cyberspace.” Ninety percent of the time, the meaning won’t substantially change. That’s because the term doesn’t really refer to any one specific type of technology, but rather a broad (and often speculative) shift in how we interact with technology. And it’s entirely possible that the term itself will eventually become just as antiquated, even as the specific technology it once described becomes commonplace.
Broadly speaking, the technologies companies refer to when they talk about “the metaverse” can include virtual reality—characterized by persistent virtual worlds that continue to exist even when you’re not playing—as well as augmented reality that combines aspects of the digital and physical worlds. However, it doesn’t require that those spaces be exclusively accessed via VR or AR. Virtual worlds—such as aspects of Fortnite that can be accessed through PCs, game consoles, and even phones—have started referring to themselves as “the metaverse.”
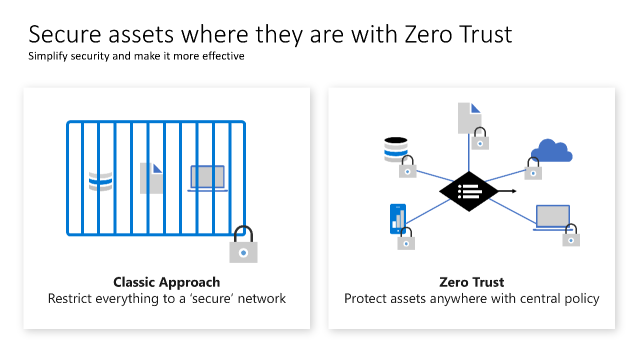
ZERO TRUST
Zero Trust Network Security
If you remember later 90’s early 2000’s everything was based on “default allow” , which was abused easily by Threat actors as it was working based on allowing unknown files and apps to access enterprises ; we still see many organizations or individuals getting effected by cyber attacks. This is how Zero Trust started to get attraction. So what is Zero Trust ? What do you need yo know about Zero trust network or Zero Trust network security ? Lets start with the basics :
A terminology that has been growing substantially over the years is the concept of a zero trust network. The whole idea of this name is to debunk the old mentality that there are “trusted networks”. In the past, most network diagrams were created by using a perimeter, the internal network (also known as a trusted network) and the external network (also known as an untrusted network). The zero trust network approach basically means: all networks (internal and external) are not trustable, all networks by nature can be considered a hostile place, where attackers may already reside.
To build a zero trust network you need to assume that threats exist, regardless of the location, and that user’s credentials can be compromised, which means that attackers might already be inside of your network. As you can see, a zero trust network is more a concept and approach to network security than a technology per se. Many vendors will advertise their own solution to achieve a zero trust network, but at the end of the day, a zero trust network is broader than just a piece of technology sold by a vendor.
One common way to implement a zero trust network is to use the device and the user’s trust claims to gain access to a company’s data. If you think about it, the zero trust network approach leverages the concept that “Identity is your new Perimeter”, Chasing a User’s Identity. Since you can’t trust any network, the perimeter itself becomes less important than it was in the past, and the identity becomes the main boundary to be protected.
To implement a zero trust network architecture, you need to have at least the following components:
- An identity provider Device directory
- Conditional policy
- An access proxy that leverages those attributes to grant or deny access to resources
The great advantage of this approach is that a user, when logged in from a certain location and from a certain device, may not have access to a specific resource, compared to if the same user was using another device and was logged in from another location in which they could have access. The concept of dynamic trust based on those attributes enhances the security based on the context of access to a particular resource. As a result, this completely changes the fixed layers of security used in a traditional network architecture.
Microsoft Azure Active Directory (Azure AD) is an example of an identity provider that also has conditional policy built-in, the capability to register devices, and being used as an access proxy to grant or deny access to resources.
Planning zero trust network adoption
The implementation of a zero trust network is literally a journey, and many times this can take months to be fully realized. The first step is to identify your assets, such as data, applications, devices, and services. This step is very important, because it is those assets that you will help you to define the transaction flows, in other words, how these assets will communicate. Here, it is imperative to understand the history behind the access across these assets and establish new rules that define the traffic between these assets.
These are just some examples of questions that will help you to determine the traffic flow, the conditions, and ultimately the boundaries of trust. The next step is to define the policies, the logging level, and the control rules. Now that you have everything in place, you can start working on:
- Who should have access to the set of apps that were defined?
- How will these users access this app?
- How this app communicates with the backend server?
- Is this a native cloud app? If so, how does this app authenticate?
- Will the device location influence data access? If so, how?
The last part is to define the systems that are going to actively monitor these assets and communications. The goal is not only for auditing purposes, but also for detection purposes. If malicious activity is taking place, you must be aware as fast as possible.
Having an understanding of these phases is critical, because in the implementation phase you will need to deal with a vendor’s terminologies and technologies that adopt the zero trust network model. Each vendor may have a different solution, and when you have a heterogeneous environment, you need to make sure the different parts can work together to implement this model.
You can organize your approach to Zero Trust around these key technology pillars:
- Secure networks with Zero Trust
- Secure identity with Zero Trust
- Secure endpoints with Zero Trust
- Secure applications with Zero Trust
- Secure data with Zero Trust
- Secure infrastructure with Zero Trust
- Visibility, automation, and orchestration with Zero Trust
Zero Trust Principles you need know
From security perimeter to zero trust
The traditional approach of access control for IT has been based on restricting access to a corporate network and then supplementing it with more controls as appropriate. This model restricts all resources to a corporate owned network connection and has become too restrictive to meet the needs of a dynamic enterprise.
Microsoft Zero Trust : https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/secure/access-control#known-trusted-allowed
Organizations must embrace a zero trust approach to access control as they embrace remote work and use cloud technology to digitally transform their business model, customer engagement model, employee engagement, and empowerment model.
Zero trust principles help establish and continuously improve security assurances, while maintaining flexibility to keep pace with this new world. Most zero trust journeys start with access control and focus on identity as a preferred and primary control while they continue to embrace network security technology as a key element. Network technology and the security perimeter tactic are still present in a modern access control model, but they aren’t the dominant and preferred approach in a complete access control strategy.
Microsoft Zero Trust guidance center : https://docs.microsoft.com/en-us/security/zero-trust/

More Zero trust Articles and Videos
https://www.erdalozkaya.com/?s=zero+trust
Hacker Combat Zero Trust
https://hackercombat.com/zero-trust-architecture-and-its-relevance-in-cybersecurity/
Keywords
digital transformation summit uae 2023 – uae digital transformation strategy -digital transformation conference dubai – What is the UAE vision of digital transformation?