Implementing Zero Trust : A CISO’s Journey – Free Video Training 2
Implementing Zero Trust
- Improved privileged access management using ‘Zero Trust’;
- Limiting exposure of sensitive data in light of the remote workforce and targeted attacks and new cybercrime scams;
- Essential steps for implementing ‘Zero Trust’ and stakeholder engagement
- CISO’s Journey
For more evets :
https://www.erdalozkaya.com/category/free-events/

Zero Trust is a security concept centered on the fact that organizations should not automatically trust anything outside and inside its perimeters and instead must verify everything trying to connect to its systems prior to granting access. This extra layer of protection has been established to prevent data breaches.
Businesses are presently functioning more differently than they did just a few years ago. We find that devices, employees, and also applications are no longer locked inside the corporate perimeter. They are all on the web and hence a unique approach is needed to provide security for a whole new type of anywhere, anytime workers and cloud-based applications. Organizations are now moving away from solutions that secure the perimeter and are instead going towards employing a zero trust model in order to protect sensitive data and resources.
Zero Trust Definition
A zero trust security solution constantly evaluates trust every time a device or user requests access to a resource. This method prevents attackers from exploiting vulnerabilities in the perimeter to gain entry and then access confidential data and applications.
Zero Trust Principles you need know
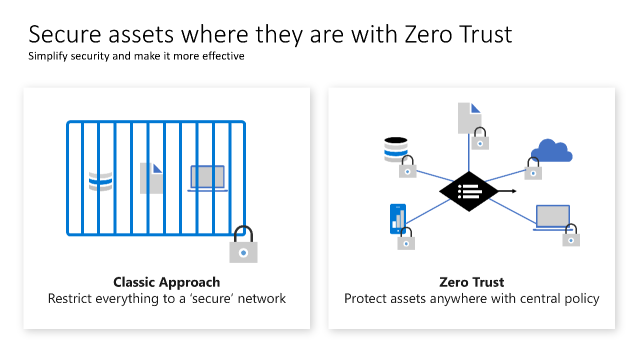
The traditional approach of access control for IT has been based on restricting access to a corporate network and then supplementing it with more controls as appropriate. This model restricts all resources to a corporate owned network connection and has become too restrictive to meet the needs of a dynamic enterprise.
Microsoft Zero Trust : https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/secure/access-control#known-trusted-allowed
Organizations must embrace a zero trust approach to access control as they embrace remote work and use cloud technology to digitally transform their business model, customer engagement model, employee engagement, and empowerment model.
Zero trust principles help establish and continuously improve security assurances, while maintaining flexibility to keep pace with this new world. Most zero trust journeys start with access control and focus on identity as a preferred and primary control while they continue to embrace network security technology as a key element. Network technology and the security perimeter tactic are still present in a modern access control model, but they aren’t the dominant and preferred approach in a complete access control strategy.