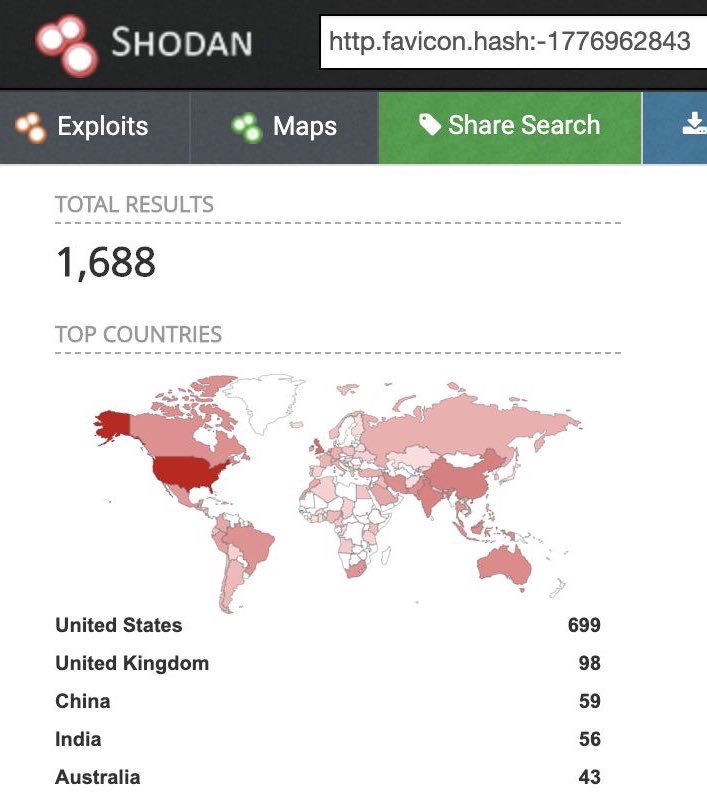
SolarWinds Onion in Shodan – Be aware
SolarWinds Onion in Shodan
As of yesterday there is 1688 open @solarwinds Orion systems . You can easily find them on @shodanhq
#SolarWinds #Orion .Just use the http.favicon string … I will write an detailed blog post later
Background
On 14 December 2020, the ACSC issued an initial alert regarding potential compromise of the SolarWinds Orion software. This alert was informed by an announcement from cyber security company FireEye, who were monitoring a global intrusion campaign linked to compromise of the SolarWinds Orion software supply chain.
Update
As of 25 January 2021, the ACSC has received a number of reports from Australian organisations notifying that they were operating vulnerable versions of SolarWinds Orion. To date, no follow-on compromise of an Australian organisation through SolarWinds Orion has been identified.
The compromise of the supply chain meant that that organisations that were running SolarWinds Orion may have inadvertently installed malicious additions through normal update processes. The malicious software (malware) associated with the supply chain compromise is being referred to as SUNBURST.
Following the identification of SUNBURST, additional malware associated with the SolarWinds Orion supply chain compromise has been identified. These are commonly being referred to as TEARDROP and RAINDROP and have been identified during investigations of follow-on compromises of affected organisations.
During investigations of the supply chain compromise, additional malware targeting SolarWinds Orion was identified. This second set of malicious software is being referred to as SUPERNOVA. The SUPERNOVA malware is not believed to be related to the supply chain compromise, instead targeting an unrelated vulnerability in SolarWinds Orion.
Mitigation
SolarWinds have identified the vulnerabilities exploited by the compromise and issued patches for affected SolarWinds Orion versions.
Accordingly, ACSC’s recommendation for mitigating potentially vulnerable versions of SolarWinds Orion is to apply the latest patches from SolarWinds as soon as possible. This recommendation applies to mitigate against both the SUNBURST and SUPERNOVA malware.
If immediate patching is not possible, the ACSC recommends vulnerable SolarWinds Orion instances be isolated from the internet and internal network connections minimised.
Additional information and supporting tools
The US Cyber security and Infrastructure Security Agency (CISA) has published a number of alerts regarding detection and mitigation of potential compromises of SolarWinds Orion, including CISA and third-party tools that may aid in the detection of follow-on compromise through SolarWinds.
Additionally, the ACSC encourages all organisations to continually assess and apply the Essential Eight strategies to protect their systems.
Assistance
The ACSC is monitoring the situation and is able to provide assistance and advice as required. Organisations that have been impacted or require assistance can contact the ACSC via 1300 CYBER1.

Why the SolarWinds Orion Platform?
The SolarWinds® Orion® Platform is a powerful, scalable infrastructure monitoring and management platform designed to simplify IT administration for on-premises, hybrid, and software as a service (SaaS) environments in a single pane of glass.
There’s no need to struggle with multiple incompatible point monitoring products, as the Orion Platform consolidates the full suite of monitoring capabilities into one platform with cross-stack integrated functionality.
The SolarWinds hack timeline: Who knew what, and when?
Impact, detection, response, and ongoing fallout from the attack on SolarWinds’ Orion remote IT management software.
Details of the 2020 SolarWinds attack continue to unfold, and it may be years before the final damages can be tallied.
While it is “hard to say” if the SolarWinds software supply-chain compromise will become known as the highest-impact cyber intrusion ever, it did catch “many people off guard” despite the security industry’s frequent warnings that supply chains pose substantial risks, according to Eric Parizo, principal analyst of security operations at Omdia, a global research firm.
The SolarWinds attack is unprecedented because of “its capability to cause significant physical consequences,” says University of Richmond management professor Shital Thekdi, an expert on risk management and industrial and operations engineering.
The attack “impacted critical infrastructure providers, potentially impacting energy and manufacturing capacities,” she said, and created an ongoing intrusion that “should be treated as a serious event with potential for great harm.”
Following is a timeline of how events related to the SolarWinds hack have unfolded, to date.
SolarWinds hack timeline (last updated March 28, 2021)
December 8, 2020: How the discovery began — FireEye, a prominent cyber security firm, announced they were a victim to a nation-state attack. The security team reported their Red Team toolkit, containing applications used by ethical hackers in penetration tests, was stolen.
December 13, 2020: Initial detection — FireEye discovered a supply chain attack while it was investigating the nation-state attack on its own Red Team toolkit. The researchers stumbled across evidence that attackers entered a backdoor in the SolarWinds software “trojanising SolarWinds Orion business software updates to distribute malware.” FireEye dubbed it “SUNBURST.”
December 13, 2020: CISA issues emergency directive — The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued Emergency Directive 21-01, “Mitigate SolarWinds Orion Code Compromise” instructing affected government agencies to take several steps for forensic investigative purposes and “immediately disconnect or power down SolarWinds Orion products, versions 2019.4 through 2020.2.1 HF1, from their network.”
December 14, 2020: The Washington Post published a report attributing the attack to Russian hacker group known as Cozy Bear, connected to the Russian foreign intelligence service, the SVR.
December 15, 2020: Victims named and timeline moves back — Wall Street Journal reported that the U.S. Commerce and Treasury Departments, the Department of Homeland Security (DHS), the National Institutes of Health, and the State Department were all affected.
Various security officials and vendors expressed serious dismay that the attack was more widespread and began much earlier than expected. The initial attack date was now pegged to sometime in March 2020, which meant the attack had been underway for months before its detection. More technical details also began to emerge, illustrating how well the malicious activity was covered and why it was hard to detect.
December 17, 2020: New victims revealed — The Energy Department (DOE) and National Nuclear Security Administration (NNSA), which maintains the U.S. nuclear weapons stockpile, were publicly named as victims of the attack.
December 19, 2020 200 more victims listed — Recorded Future, a cyber security firm, identified an additional list of government agencies and companies around the world that had also been attacked, but did not publicly reveal their identities.
Using Twitter for his first comments on the attack, then-U.S. President Donald Trump publicly suggested that China, not Russia, was the source, and also described the hack as a hoax. U.S. Secretary of State Mike Pompeo and other senior members of the administration disputed these claims the same day, stating that “we can say pretty clearly that it was the Russians that engaged in this activity.”
December 31, 2020: Microsoft says the Russian attackers breached some of its source code — The software giant said that the attackers could not modify code, products, or email and they did not use Microsoft goods to attack other victims. By this point, the attacks are largely thought to “have begun as far back as October 2019…when hackers breached the Texas company SolarWinds.”
January 5, 2021: Joint statement by FBI, CISA, ODNI, and NSA released — The Federal Bureau of Investigations (FBI), CISA, The office of the National Director of Intelligence (ODNI), and the National Security Agency (NSA), jointly released a statement on the formation of the Cyber Unified Coordination Group, which “indicates that an advanced persistent threat (APT) actor, likely Russian in origin, is responsible for most or all of the recently discovered, ongoing cyber compromises of both government and non-governmental networks. At this time, we believe this was, and continues to be, an intelligence gathering effort.”
January 6, 2021: CISA issues supplemental guidance — CISA’s supplemental guidance required US government agencies that ran affected versions of SolarWinds Orion conduct forensic analysis; those that accept the risk of running the software comply with certain hardening requirements, and new reporting requirements by agency from department-level CIOs. The deadlines for the agency CIO reports were Tuesday, January 19, and Monday, January 25, 2021.
January 27, 2021: CISA releases a report on Supernova, the malware “that was deployed using a vulnerability in the Orion Platform, and after the Orion Platform had been installed.”
January 29, 2021: SolarWinds issues an advisory for both Sunburst and Supernova.
February 19, 2021: Biden Administration declares intent to punish Russia for SolarWinds attack — Jake Sullivan, national security advisor, told CNN’s Christiane Amanpour that President Joe Biden’s administration would look at a “broad range of responses” after an investigation to further pinpoint the identities of the attackers.
February 23, 2021: First Congressional hearing — Microsoft and FireEye testified before the Senate Intelligence Committee on the SolarWinds attacks. A transcript and a video of the hearing is available on C-Span.
Microsoft president Brad Smith said its “researchers believed at least 1,000 very skilled, very capable engineers worked on the SolarWinds hack. This is the largest and most sophisticated sort of operation that we have seen,” Smith told senators. All defended their own actions before and after the attacks, and all fingers pointed at Russia as the attacker.
February 26, 2021: Second Congressional hearing — The U.S. House Committee on Oversight and Reform and the House Committee on Homeland Security held a joint hearing “examining recent cyber security incidents affecting government and private sector networks, including the supply chain attack targeting SolarWinds Orion Software and other cyber attacks.
On December 17, the Committees launched an investigation into the cyber attacks. On December 18, the Unified Coordination Group provided a classified Member briefing by telephone about the attacks.”
February 24, 2021: SolarWinds issues a FAQ: Security Advisory. This advisory offered further guidance to SolarWinds customers on how to tell if they were affected, what steps to take, and answers to related questions.
March 15, 2021: A Public Affairs spokesperson in the National Press Office of the FBI answered “no comment” to CSO’s questions on the current status of the SolarWinds attacks, stating that “the investigation is ongoing.”
March 28, 2020: Reports state DHS, cyber security leaders’ emails compromised — The Associated Press reported that the SolarWinds hackers “gained access to email accounts belonging to the Trump administration’s head of the Department of Homeland Security and members of the department’s cyber security staff whose jobs included hunting threats from foreign countries.”
What now? What next?
While the country and the world waits for the final measure of the costs and scale of the SolarWinds attack, it is clear to all that the impact continues.
“There are a multitude of reasons why there could still be vulnerable systems out there or with the vulnerable systems patched an attacker could have pivoted and maintained persistence without the company knowing,” warns Amanda Berlin, a security consultant and co-author of the Defensive Security Handbook.
“Some SolarWinds customers may still be unaware that they have SolarWinds on their network. Maybe the staff that installed it isn’t employed there anymore or maybe key personnel didn’t hear the news or the company doesn’t have the tools to detect it. So many environments have limited visibility into what is happening that they may never know until something goes wrong.”
In any case, the future implications are considered grim if lessons learned from this are not acted upon.
“From a long-term perspective, enterprises should not only ensure they have a data exfiltration prevention program, assuming all other defences fail, but also seek to develop a ‘cyber kill chain’ for supply-chain compromises, creating as many opportunities as possible to prevent, disrupt, or at least quickly detect them,” said Omdia analyst Parizo.
“This should include software risk management best practices, such as NIST’s Cyber Supply Chain Risk Management (C-SCRM), and establishing a baseline set of software security requirements that must be met by any software vendor prior to a purchase,” Parizo added.




