
Cyber Threat Intelligence Resources – Free and Useful Top 5
Cyber Threat Intelligence Resources
5 Important Cyber Threat Intelligence Resources
This post will take you through Structured Threat Information Expression (STIX), Trusted Automated Exchange of Intelligence Information (TAXII), Oasis Open Command and Control (OpenC2), Traffic Light Protocol (TLP), and Cyber analytics Repository by MITRE (CAR). With the knowledge of the aforementioned resources, you will be better equipped to identify threats and vulnerabilities.
Structured Threat Information Expression
Structured Threat Information Expression, commonly known as STIX, is a special language format to exchange threat intelligence related to cyberattacks. STIX is open source, and free to be used by anyone. STIX allows us to share threat intelligence from any point of view, such as suspicion or compromised information (IoC). It also allows us to represent clearly with objects and detailed relationships between them with threat information.
STIX is generally shared in JSON format but can also be represented visually for any analyst to take advantage of the information. The information shared can be easily integrated with security-analytics tools. STIX has 12 domain objects to define a threat element (more information can be found at https://oasis-open.github.io/cti-documentation/stix/ intro):
Attack Pattern: Allows us to describe how threat actors attempt to compromise any target by providing information about the type of Tactics, Techniques, and Procedures (TTP).
Campaign: Describes the grouping of attacker behavior for a particular set of malicious activities and attacks that are observed over a period of time against a very specific group of targets
Course of Action: Defines what action is to be taken to prevent or respond to an attack.
Identity: This object helps define individuals, organizations, or groups, as well as classes of individuals, organizations, or groups. Indicator: It can contain a pattern of threat information that can be used to detect suspicious or malicious cyberactivity.
Intrusion Set: Describes attacker or adversarial behaviors and resources grouped together as a set, and its common properties are assumed to be orchestrated by an individual threat actor.
Malware: Information about malicious code and malicious software, which can be used to compromise the confidentiality, integrity, or availability of a victim’s data or system.
Observed Data: Contains information observed on a system or network (for example, a source or destination IP address). Report: This object may contain threat information related to the description of a threat actor, malware, attack techniques, or contextual data.
Threat Actor: This object can carry information about any individuals, groups, or organizations assumed to have malicious intent.
Tool: Any information about software packages that can be used by adversaries to perform an attack.
Vulnerability: Vulnerability or bug information of a software that can be directly used by a hacker to compromise a system or network. Here is a sample JSON structure of STIX:
{ “type”: “”, “id”: “object–xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx”, “created”: “yyyy-mm-ddThh:mm:00.000Z”, “name”: “”, “description”: “”
Trusted Automated Exchange of Intelligence Information
Trusted Automated Exchange of Intelligence Information (TAXII) The Trusted Automated Exchange of Indicator Information (TAXII) is a standard way for message exchanges that provides a sharing mechanism of actionable cyber threat information between different organizations and product/service boundaries. TAXII defines concepts, protocols, and message exchanges to exchange cyber threat information for the detection, prevention, and mitigation of cyber threats. Broadly, TAXII covers two primary services of sharing models:
Collection: This is an interface to access a repository of Cyber threat intelligence (CTI) objects provided by a TAXII server, which further allows a producer to host a set of CTI data that can be requested by TAXII clients and servers to exchange information in a request-response model (more information can be found at https://oasis-open.github.io/cti-documentation/taxii/intro ), shown as follows:
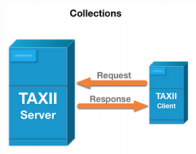
Channel: This is maintained by a TAXII server. Channel allows CTI producers to push data to many consumers and consumers to receive data from many producers. TAXII clients usually will exchange information with other TAXII clients in a publisher-subscriber model,
OASIS Open Command and Control (OpenC2)
OASIS Open Command and Control (OpenC2) is a technical committee that focuses its efforts on artifacts that are generated by the OpenC2 community forum. The OpenC2 TC was chartered to draft documents, specifications, or other artifacts to support the needs of cybersecurity commands and control in an industry-standard manner. The Technical Committee also leverage any preexisting standards to a great extent and practically identify gaps pertaining to the command and control of technologies that provide or support cyber defenses (https://www.oasis-open.org )
Traffic Light protocol (TLP)
The Traffic Light Protocol (TLP) was created in order to facilitate the sharing of information. TLP is a set of designations used to ensure that sensitive information is shared with the appropriate audience. It employs four colors to indicate expected sharing boundaries to be applied by the recipient(s), and the different degrees of sensitivity and the corresponding sharing considerations to be applied by the recipient(s).
TLP only has four colors; any designations not listed in this standard are not considered valid by FIRST. TLP is a simple and intuitive schema to indicate when and how certain sensitive information can be shared, for more repetitive and effective collaboration, but on the other hand TLP is not to be treated as “control marking” or classification. TLP is optimized for easy adoption, human-readable, person-to-person sharing; it can also be used in automated sharing.
The source who is sharing the threat information is responsible for making sure that the recipients of the TLP information have complete understanding of the sharing guidelines of TLP. In case the recipient wants to share the information further, they must obtain explicit permission from the owner of the information. Here are the TLP definitions that can be used to tag information while sharing (for detailed usage, please visit https://www.us-cert.gov/tlp)
Cyber Analytics Repository by MITRE (CAR)
The Cyber Analytics Repository (CAR) is a repository based on analytics of Adversary Tactics, Techniques, and the Common Knowledge (ATT&CK) threat model as developed by MITRE. The analytics stored in CAR include information such as an explanation of the thought process of the analytic of a subject, information about the primary domain (for example, host, network, process, external), available references to ATT&ACK (https://attack.mitre.org ) techniques, and also a pseudocode and unit test that can be used to implement and test the analytic. You can find more details for further research and reading at https://car.mitre.org/.
IntelMQ by ENISA
IntelMQ is a platform for the security teams in any CERT, CSIRT, or other security operations. This platform is a community-driven initiative by the Incident-handling Automation project by ENISA, CNCS (National Cyber Security Centre—Portugal), CERT.AT, CERT-EU, and CERT.BE for collecting and processing security feeds by leveraging a message-queuing protocol.
IntelMQ is focused on reducing the complexity of system administration, writing new modules for new data feeds, using a common format for sharing by JSON, integrating with common existing tools, providing flexibility to store information in popular log collectors, such as Elasticsearch and Splunk. This platform also offers the flexibility to create custom blacklists for your own use and to share threat intel by the HTTP RESTFUL API. Full details on its usage and an implementation guide can be found at https://github.com/certtools/intelmq
Recorded Future
Recorded Future (https://www.recordedfuture.com) is an advanced SaaS-based product. This platform combines the automatic collection and analysis of threat intelligence from open source, dark web, and other technical sources into a single solution. Recorded Future uses advanced technology, such as natural language processing (NLP) and machine learning, to process, enrich, and deliver threat intelligence in real time. This platform has the ability to contextualize threat intelligence to provide proactive threat information for developing a security strategy.
The ability to crunch and process huge volumes of threat intelligence data with machine learning helps analysts reduce their time to come to a conclusion. You can access the threat-intelligence data from Recorded Future in their web based platform, which can also be integrated with a wide range of cybersecurity solutions.
It will help you to get wide visibility of the threat landscape you are in and enrich alerts for your security teams. Recorded Future also provides integration with multiple deep analysis products, incident response tools, intelligence platforms, network detection products, SIEM, SOAR, threat hunting, vulnerability management tool, and ticketing systems.
Anomali STAXX
Anomali STAXX (https://www.anomali.com/community/staxx) is a tool for sharing threat intelligence from STIX/TAXII sources by connecting to STIX/TAXII servers; this gives you access to search and configure your own threat feeds based on your specific needs. It also allows you to import threat-intelligence data into
Anomali STAXX and then upload selected intelligence data to other STIX/TAXII servers. This platform provides a very easy and interactive interface to skim through threat-related information. Anomali platform helps you collect threat intel feeds from OSINT and ISACs.
Cyberthreat-intelligence feeds
As you know by now, cyberthreat intelligence focuses on providing actionable information on adversaries to build a proper cyber defense against attacks.
Knowing the right resources will help you to speed up your research as well as get the right advice from the industry. Check out these resources :
- AlienVault.com : Multiple sources including large honeynets that profile adversaries.
- Cyveilance.com: Unique feeds on threat actors and indications of criminal intent.
- EmergingThreats.net: : A variety of feeds.
- FireEye.com Dynamic Threat Intelligence (DTI) service.
- Hacksurfer.com (SurfWatch): ): Insights tailored to your business.
- InternetIdentity.com: : Threat feeds from their big data solution, ActiveTrust.
- RecordedFuture.com: Real-time threat intelligence from the web.
- Intelligent Security Graph (https://www.microsoft.com/en-us/security/operations/intelligence): Advanced analytics link massive amounts of threat-intelligence and security data to provide you with unparalleled threat protection and detection.
- Secureworks.com: Provides feeds and also instruments networks.
- Symantec.com DeepInsight feeds on a variety of topics including reputation.
- com: Everything there is to know about the past, present, and future of spies.
- Team-Cymru.com: Threat intelligence plus bogon lists.
- TheCyberThreat: Our Twitter feed. High-level but comprehensive and curated.
- Spytales.com: The most critical lessons in cyber conflict and cybersecurity, relevant for your defense today. Security Intelligence Resources
- Team-Cymru.com: Created by Cyber Squared and focused on information sharing.
- ThreatGrid.com: Unified malware analysis. Now part of Cisco.
- ThreatIntelligenceReview.com: Updated reviews of threat-intelligence sources.
- ThreatSTOP.com: Block botnets by IP reputation.
- ThreatStream.com: Famous team. Multiple sources in interoperable platforms.
- ThreatTrack.com: Stream of malicious URLs, IPs, and malware/phishing-related data.
- Verisigninc.com: iDefense feeds that are highly regarded by some key institutions.
- Threat Map :Real time malware detectors https://threatmap.valkyrie.comodo.com
- Valkyrie: https://verdict.valkyrie.comodo.com/ Know what is safe, and what is malware with Valkyrie Verdict – your free analysis service for files and websites.
Some more information about Cyber Threat Intel
Building a Cyber Threat Intelligence Platform in 5 steps
https://www.erdalozkaya.com/cyber-threat-intelligence/
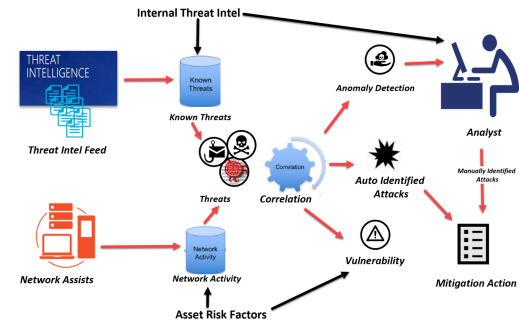
Intelligent security is key to fighting sophisticated threats
https://www.erdalozkaya.com/intelligent-security-is-key-to-fight-sophisticated-threats/
Knowing the threat actors behind a cyber attack
https://www.erdalozkaya.com/knowing-the-threat-actors-behind-a-cyber-attack/





