
Cybersecurity Metrics To Report To The Board – With 2 great examples
Cybersecurity Metrics to Report to the Board
Information Technology (IT) is all about metrics. Each and every system creates logs, and in a mid-size organization, the number can be exceedingly high. The same applies to security, of course. It is clear that the Board will not care about every system; they certainly tend to leave day-to-day IT management to the CIO / CISO and their security teams. So which security metrics and measurements should be reported to the Board?
While there are metrics that Boards need to know, it is also important to consider how C Suite technology leaders tackle metrics and related issues. So, this blog post is not just for Board members but also for the CISO, CIO, and CTO.
As cybersecurity shifts from the technical sphere to the boardroom, how to report metrics to the Board is becoming an increasingly significant task for CISOs, CIOs, and CTOs.
Metrics To Report to the Board

Metrics are tools that facilitate decision-making and improve performance and accountability. Measures are quantifiable, observable, and objective in data supporting metrics. Operators can use metrics to apply corrective actions and improve performance. Regulatory, financial, and organizational factors drive the requirement to measure IT security performance
(Source: Cyber Security Metrics and Measures by Paul E. Black, Karen Scarfone, and Murugiah Souppaya )
Data can be overwhelming. Finding relevant figures and statistics is essential.
In other words, metrics are evidence, and this evidence proves what systems are doing or not doing. In the IT world, there can be exceptionally large numbers to report on. As a result, the metrics presented to the Board have to be related to the business, and it should be explained in non-technical language.
Metrics reported to the Board should reflect:
- The potential impact of a cybersecurity attack on the company’s reputation
- The potential financial impact
- The responsibility of the Board members
1) Metrics that demonstrate an ability to detect and respond to Incidents
Having an Incident Response (IR) plan, and measuring the effectiveness of the plan, should be a number one priority. An IR plan specifies how fast a company can respond to incidents. The faster your security programs eliminate an “attack”, the less damage is likely to be done to the business and organization.
Data Breach reports (like Verizon’s) will show that many companies allow hackers to stay up to 100 + days to do whatever they want to do until they finally detect them.
To measure incident response rates, Technology Leaders can: · Use an EDR or XDR to identify security incidents on you’re their network, then manually record their own response time via “simulations”
· Use Threat Intelligence Partners or tools to keep an eye what is happening across the Security Landscape
· Use security ratings providers to identify risks, gaps, and inconsistencies in the environment. Here is a way which you can do it for free via this link.
Ensure that risk management is used in every step for quantitative measurement. You need to have full visibility in your network; the more visibility you have, the better you can monitor benchmark your metric, and build a remediation strategy and deadline.
The IR metrics to report to the Board include:
- Time to respond
- Time to contain
- Time to remediate
These metrics give Board members clear indication of how many cybersecurity investigations are currently underway (if any), and how much time it takes on average to conduct an investigation. Be sure to back up those metrics with:
- Number of security controls added in the past twelve months
- Number of investigations new security controls have created
These numbers present to the Board your readiness for attacks, while you gain lessons from what happened and implement lessons-learned and best practices. If no incident is under investigation or remediation, then you can combine this knowledge with Step 3 which below, which covers where your organizations stand compared to the industry at large.
2) Metrics showing outstanding high-risk findings
Technology teams are remarkably busy, and therefore they are sometimes a bit afraid to make major changes that might break the system or result in an ignored or delayed response or implementation of a patch for a given timeframe. This is why it is important for the Board to track metrics for outstanding or open issues.
The Board should be aware of any outstanding high-risk findings open from the last audit or assessment. Of course, sometimes a patch cannot be deployed because the vendor has not released it, or the patch really does create some serious issues. But as long as Technology executives report these issues to the Board and explain the primary reason for the delay, the appropriate risk management action can be applied.
“Patching” was used as an example above because it is important for the Board to keep an eye on how many “critical” vulnerabilities are not yet patched.
Here are some metrics that Tech Executives should not present to the Board:
- Patches installed successfully
- Number of malware detections
- Number of external attacks detected logs
- Vulnerability, compliance, or any other scan results
It is important to be transparent, and to be ready to answer the following questions from the Board:
- What is the largest risk you are facing, or any risk you may not be able to address at the moment?
- What workarounds do you have available for those risks?
- How you will improve the current security program based on the current open items?
As a Technology Executive, avoid technical talk when addressing the Board, and focus on risks and how they affect the business. While talking about Cyber Risk Levels, list your priorities and solutions, and be clear about what kind of support you need from the Board to move forward.
3) Where your cyber technology stands relative to the industry
Usually, sales teams report these types of relativity metrics to the Board, comparing sales figures with competitors. I strongly believe this should be also reported by technology teams.
The Board should know how their organizations compared to peers in their sector, and what are other security teams doing to be or proactive and improve their organization’s security posture. These kinds of reports can be found by companies like BitSight, Security Scorecard etc.
4) Current Cybersecurity Awareness Level across the organization
It is the Boards job to empower the C Suite technology leader so they can create a cybersecurity culture within the organization such that everyone in the organization understands the cyber risks and threat landscape and can help you mitigate attacks.
As a Technology Leader you need to ensure that your organization has customized cyber awareness training, based on roles and responsibilities. The training status needs to be tracked by the Board, in my opinion.
5) Budget Request (depending on the agenda)
If there are unforeseen high risks not budgeted, then this can be a key topic to open with, whgen addressing the Board. Otherwise, requesting budget should not be a key metric. If there is already a budget assigned, including a line or two to indicate status and current spending, and how the budget is utilized, can also be a good practice.
For example, if there is a new strategy that will decrease the current cyber risk exposure by 30 %, but requires a 10% budget increase, backing up this assertion and request with the supporting figures will convince the board to approve your strategy.
Cybersecurity Dashboard Example 1
Company Details: A mid-size organization with up to 500 staff. The organization undertook a cybersecurity risk assessment to understand their cybersecurity posture. The following major findings are reported to the Board:
- The organization has no security policy and this needs to be addressed.
- There is no security-related training in place; phishing attacks are causing issues.
- There are no regular security assessments.
- One of the company databases was found on the Dark Web, without any details about how it was leaked
| Current Cybersecurity Risk Status | Key Risk Factor |
| Business Continuity Planning (BCP) | BCP needs to be implemented |
| Access Management | Access to resources has been implemented but Data Loss Protection (DLP) is not yet implemented |
| Policy | A security policy is missing and the business is exposed to cyber-attack risks |
| Information Protection | The database is leaked but the current status is unknown, fixes need to be implemented |
| I.T. Risk Management | The lack of a regular security review program leads to unknown risks and exploits |
| Physical Security Management | Access Cards, CCTVs, and Security Guards in place |
| Security Awareness | Staff require cybersecurity awareness training to help prevent attacks such as phishing |
Emerging risks, threats, or vulnerabilities
Be sure to add statistics from your country’s CERT (Computer Emergency Response Team )
This section of your report to the Board can include cybersecurity trends (based on CERT) for the sector your business is in.
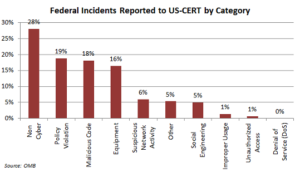
Impacts on the organization
Example: Based on the latest report by US-CERT, both phishing and credential harvesting attacks are trending significantly. This is evidence of why we need to invest in Phishing Incident Response and cybersecurity awareness training.
Continue your report to focus on unauthorized access to both internal and client information. For example, several internal incidents might have been due to incorrect staff access rights or privileges being assigned. Or there may have been an external, malicious attack that attempted to access PII data. In conversations with other similar organizations, this risk is highlighted, and several organizations are working to refine and implement proper access control to files.
Incidents
Example: There has been one significant security incident during the last month.
- Type of incident: Unauthorized information disclosure
- Status: Resolved
- Description: A staff member accidentally sent a confidential customer data file to the wrong customers.
- Discovery: The client emailed the staff member to let them know they had received the incorrect information.
- Resolution: The client has confirmed and provided evidence that the three files containing other client data have been deleted. All affected clients have been informed and apologies issued. One client has decided to not continue to work with our organization.
- A DLP solution is going to be implemented to prevent this kind of mistakes
- Time to discover: 3 days
- Time to resolve: 5 hours
- Quantifiable Cost: $5,000
- Unquantifiable Cost: Brand damage and losing a customer
- Lessons Learned: After reviewing the issue, a DLP solution will be implemented to minimize the possible mistake ever recurring.
- Compliance:
- The ISO 27001 framework will be adapted to be compliant. Areas needs urgent attention to be ISO compliance
- Development of security policy
- Completion of BCP to include cybersecurity incidents
- A compliant access management plan
- Annual staff training
Report Summary [Example]
- Information protection and security awareness weaknesses need to be resolved as soon as possible.
- An unauthorized information disclosure incident has cost the organization $5,000.
- There are four key tasks left to complete to meet our ISO27001.
Cybersecurity from the technical sphere to the boardroom
Well before you present metrics to your Board, I highly recommend that you prepare yourself for the meeting. Here are a few useful tips:
- Get to know the members of the Board
- Make sure to align the Cybersecurity Strategy with the global business strategy
- Adopt a risk-based approach when it comes to risk management
- Be clear, and explain what you are trying to achieve; ely on the metrics
- Use real-life examples
- Use summaries, callouts, graphics, and other visuals. Avoid technical jargon
- Reports should also enable dialogue and debate
There are certainly more metrics to report on, and each Board meeting can be different. More blog posts are forthcoming that discuss Cybersecurity and The Board of the Directors, so please keep an eye out here at my blog site and on my LinkedIn page.

Summary
- Information protection and security awareness weaknesses need to be resolved as soon as possible.
- An unauthorized information disclosure incident has cost the organization $5,000.
- There are four key tasks left to complete to meet our ISO27001.
Cybersecurity from the technical sphere to the boardroom

Before you go ahead and present your metrics to the board, I highly recommend that you:
- Get to know the members of the Board
- Make sure to align the Cybersecurity Strategy with global business strategy
- Adopt a risk-based approach when it comes to risk management
- Be clear, explain what you are trying to achieve and relay to the metrics
- Use real-life examples
- Use summaries, callouts, graphics, and other visuals, avoid technical jargon
- Reports should also enable dialogue and debate
There are for sure much more metrics and each board meeting can be different. There will be more blog post about Cybersecurity and The Board of the directors, So please keep an ay here at my blog and my LinkedIn page
Here is one more article which may draw your attention: Cybersecurity Questions to boards
Cybersecurity Strategy Book for more details click here
Sponsored Link
If you found the article insightful then why not see how Comodo can help your organization prevent cyber-attacks at runtime? Contact us or request a free demo.
Cybersecurity Metrics to Report To The Board – With 2 great examples





