SECON International 2nd Annual International ISC2 Chapter Conference 2023
SECON International 2nd Annual International ISC2 Chapter Conference 2023 will be held online , free for iSC members
 Search
Search
Type and hit enter
SECON International 2nd Annual International ISC2 Chapter Conference 2023 will be held online , free for iSC members
Threat Hunter Assessment Tool
Xcitium OpenEDR is an open-source endpoint telemetry platform that aims to provide a comprehensive and effective solution for endpoint security. It is developed by Xcitium, a company that offers cybersecurity solutions, and it is based on open-source technology, which means anyone can access, modify, and contribute to the source code on GitHub. In this review, I will evaluate the features, benefits, and challenges of Xcitium OpenEDR, and compare it with some of the existing endpoint security solutions in the market.
Incident Response Challenges Incident Response Evolution and Current Challenges Part 3 This is the third part of the article. To read Part 1 please click here, to read Part 2 please click here Preventing future breaches The last phase of an incident management plan is reporting, and avoidance of future security incidents. Therefore, a major […]
To read Part 1 of the article, please click here
Compared just with the last decade or so, the cybersecurity landscape has evolved as threats have become more sophisticated. Not only organizations but more and more individual devices are connected to the internet. While beneficial technological progress has been happening, attacks have also evolved, as illustrated in the following diagram
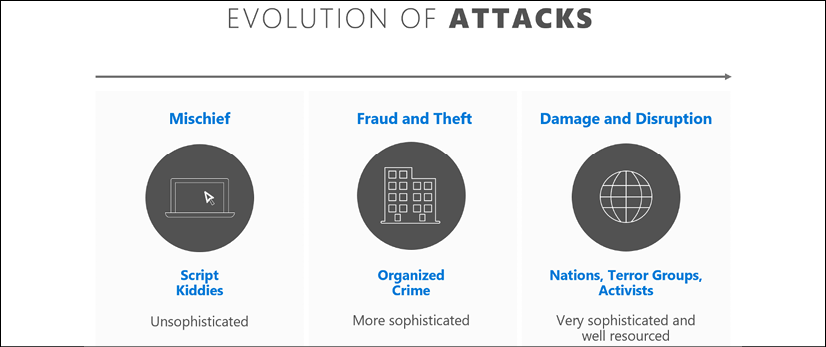
Evolution of attacks
Considering the past couple of decades since 2000, Script Kiddies were initially the main culprits, and their main motivation was “mischief.” Script kiddies are unskilled persons who use attack scripts developed by other people in attacks. They were a significant threat in the early and mid-2000s due to the increased access to personal computing, low levels of security capabilities in early computers, and access to scripts written by expert hackers.
In comparison, today we see that Organized Crime is getting more and more sophisticated and their Fraud and Theft capabilities are increasing. A good example of the damage more organized attacks can inflict is the 2017 WannaCry ransomware attack, which exploited a zero-day vulnerability in Microsoft Windows and affected 150 countries, extorting victims for decryption keys. While in the 2000s a single script could’ve been used by multiple script kiddies until it became widely known or obsolete due to patches, currently attackers can use zero-day vulnerabilities and use them to attack systems while there are no known defenses.
The activities of Nations and Terror Groups can cause serious financial damage, as well as a negative brand reputation for affected organizations. Nation-state attackers are usually sponsored by governments and they target other government agencies or critical infrastructure as well as any key industries known to contain sensitive data or intellectual property. Nation-state attackers are well known to strike via sophisticated techniques, one of the most well-known attacks being the Stuxnet attack on an Iranian nuclear plant.
It’s really important to understand the attackers and think like them to be able to create a proper IR plan. As the famous general Sun Tzu said in his book The Art of War: to win a war, we need to know the enemy, ourselves, and the attack ground. To learn more about possible attackers, it is highly recommended to read intelligence reports from security vendors such as Microsoft or Comodo, or from providers like Verizon, which can give a more detailed perspective on the current security landscape. Verizon Data Breach Report 2019 is based on a detailed analysis of 41,686 security incidents, including 2,013 confirmed data breaches. Some statistics of who was behind the recorded cyber-attacks are as follows:
When we look at the threat actors’ actions, we see the following trends:
The report also highlights that the victims were:
As you can see from the preceding figures, the increase in technology has resulted in an increase in attacks exploiting this progress. To be able to deal with these complex attacks, which can affect organizations of any size, it’s important to develop capable IR teams, ( You can fidn more about this in my Incident Response of the Age, Chapter 3, How to Organize an Incident Response Team. )
Furthermore, to combat this evolution of attacks, enforced structured change in IR has been, and continues to be, necessary in conjunction with the evolution of the threat landscape. It’s important to highlight that the threat landscape will continue to evolve, but the basics of IR will develop around the same framework: identify, contain, eradicate, and recover. IR processes have evolved in some ways, though. In the past, cybersecurity professionals were often seen as security guards at the gate, responsible for protecting corporate data and preventing cyber-criminals from gaining access to enterprise systems. This largely involved maintaining a “perimeter defense” and dealing with attacks as they came.
However, enterprises in recent years have started to use cloud services and bring-your-own-mobile-device policies, which operate outside the corporate network. This has shattered the perimeter defense concept and forced the security team to spend most of its time searching for threats that have already penetrated the organizational walls.
Thus, today, when confronted with a breach, as well as taking a more proactive approach (more on this in Chapter 3, How to Organize an Incident Response Team), more and more enterprises are aware of the importance of Digital Forensics Incident Response (DFIR) strategies. These specialist investigation techniques are used to more effectively hunt for more sophisticated malicious entities hiding in the infrastructure, as well as providing the right tools to detect and remediate compromises as soon as possible.
Despite some progress in this area, the following statistics from IBM show us why we need to continue to invest in and evolve our IR processes; the cost of a breach, on average, is astronomical, as shown by IBM’s analysis in Figure 2.2. Please keep in mind that 2020 was a more extraordinary year, where organizations needed to deal with the COVID-19 pandemic alongside normal security protocols:
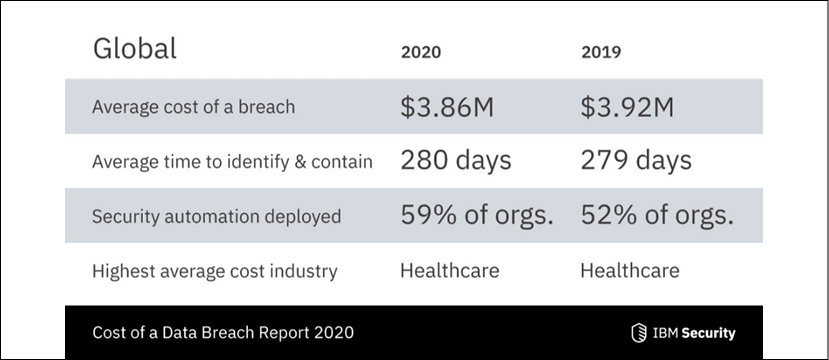
Figure 2.2: IBM cost of data breach statistics
Now, you can review the IBM statistics in the following figure, and compare them to the costs detailed in the breach report in Figure 2.2:
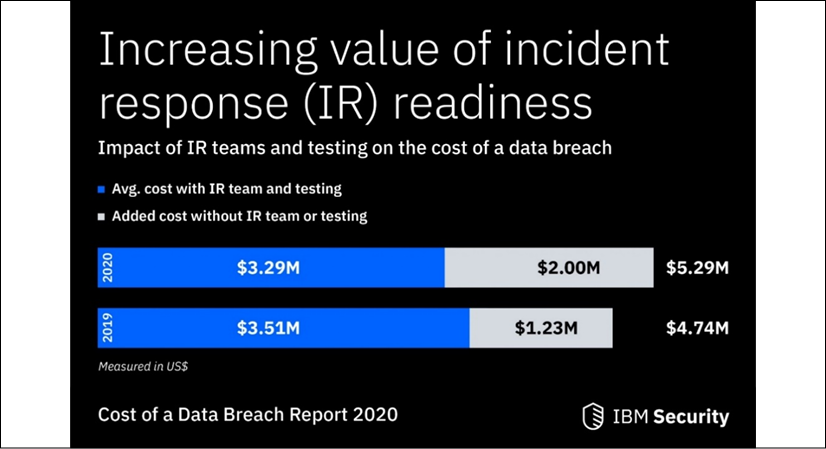
Clearly, by investing in this book and learning IR, you are on the right path for yourself and your organization.
As you have learned by now, due to the continued evolution of attackers’ techniques and methods, it is no longer a question of whether you will experience an incident, but rather when. Moving forward, readers are encouraged to communicate this to senior management since IR requires approval and input from every business unit. In the next section, we’ll take a look at how IR imposes some challenges on the teams tasked with the process.
IR is a fairly challenging process, and IR teams meet a fair share of challenges when carrying it out. Every organization is susceptible to attacks, yet it is upon IR teams to ensure the protection of the organization, its healthy reputation, and customer trust, and moreover ensure that a similar threat will not reoccur in the future.
When a security incident occurs, confusion might hit organizations, especially if they have never handled similar security events before. An informed IR plan guides organizations, regardless of prior experiences, on how to handle each aspect of an incident. IR also mitigates the effects of a security event, to ensure minimal damage and fast recovery of key business processes. Therefore, depending on the stage of an attack or intrusion, the IR plan will detail the steps that must be taken to ensure the best outcomes for the organization. Without this guiding tool, the organization would find it hard to systematically contain any security event.
However, there are still many issues that arise in the wake of an attack that an IR team will need to effectively counter. The following section will detail some of the main challenges facing IR teams. We’ll start by considering the importance of protecting the company brand.
One major challenge facing IR teams is protecting their organization’s brand, as IT security is closely tied to the reputation and valuation of an organization. As observed in recent breaches, poorly handled security incidents hurt the brands of the affected companies. For instance, Yahoo’s valuation dropped by 350 million US dollars after a hack in 2017 that was reported to have affected one billion users. Similarly, a report by Kacy Zurkus indicated that the common aftermath of security breaches in organizations is a decrease in stock price.
Zurkus’ article can be accessed here: https://www.infosecurity-magazine.com/news/companies-stock-value-dropped-1/.
Zurkus estimated the average drop of stock value to be 7.5%. However, security incidents, if correctly handled, might not have such a dramatic effect on the brand of the company. Due to effective incident management, Sergei Klebnikov reports that big-name companies that have been victims of security breaches mostly recover and outperform the market in as little as six months after the breach.
Klebnikov’s article can be accessed here: https://www.forbes.com/sites/sergeiklebnikov/2019/11/06/companies-with-security-fails-dont-see-their-stocks-drop-as-much-according-to-report/#29da9aed62e0.
Examples of post-incident activities in such companies might include more optimized customer relationship management, to ensure that the existing clientele is retained and new customers are strategically acquired. Thus, IR faces a crucial challenge in providing ways that the organization can prevent negative publicity as a result of cyber-attacks, and thereby maintain or increase its market share.
As you can see in Figure 2.4, many well-known corporations have experienced cyber incidents or been hacked:

Figure 2.4: Organizations that have fallen victim to cybercrime
As goes the popular phrase:
“There are two types of organizations: the ones that know they’ve been hacked and the ones that don’t.”
To contunie n reading the article please browse to part 3. In Part 3 we will cover the below topics:
- Preventing future breaches
- Preparing for attacks
- Developing cyber resilience
- Assessing security safeguards
- Aiding investigations and legal prosecutions
- Bringing the organization together during crises
- Ensuring the integration of security initiatives
- Improving the overall security stature of the organization
- Why do we need incident response?
- Tips
Breaking the Stereotype Whilst others consider cyber security as a protocol, Dr. Erdal Ozkaya believes that it is a mindset that goes deep into the ancient human DNA. You know it, you got it! By : Anushree Dixit via Cyber Sentinels Magazine Dr. Erdal Ozkaya’s association with IT goes back to an era in 1996 […]
Siber güvenlik bir beka sorunudur This is the ICT Media interview in Turkish ICT Media dergisine yayimlanan mulakatimiz , ICT Media websitesinde okumak icin burayi tiklayiniz : Dr. Erdal ÖZKAYA, dünya çapında siber güvenlik hizmetleri veren Xcitium (Comodo) Şirketinde Siber Güvenlik Departman Şefi olarak çalışıyor. Hayatı sayısız başarı ve sertifikalarla dolu. Siber güvenlik üzerine yurt […]
I am proud to be invited by the Ministry of Treasury and Finance of Türkiye (Turkey) to deliver a session on Securing the Digital Ecosystem on Banking. The rest of the post is going to be in Turkish.
Where: Ankara
When May 3 and 4 Continue reading Finans Sektörü Odaklı Siber Tatbikat
ICT Media Magazine Cover – I am thrilled to be in a 3rd time on a Magazine Cover. This time in Türkiye on ICT Media : It is such an amazing honor to be featured multiple times in this magazine, which showcases the best of the Information and Communications Technology (ICT) industry. This cover is […]
Trusted Security Advisor Community I am really excited to announce the “Xcitium Zero Dwell Trusted Security Advisor” community. This community came together to educate and advocate Zero Trust adoption and Cybersecurity awareness. Besides that, the Xcitium MVP’s will provide Xcitium , advisory with customer insights and real-world voices it needs to continue empowering IT professionals […]